A clear and consistent CRA technical file structure is essential if you want to demonstrate Cyber Resilience Act compliance to customers, authorities and notified bodies. The technical file is the main evidence that your product with digital elements meets the CRA security requirements and that you have designed, built and maintained it in a secure way.
This guide explains how to design a practical CRA technical file structure that works for manufacturers, IoT vendors, embedded system teams and software suppliers. It shows how to organise your technical documentation, what sections to include and how to connect the technical file with your risk assessment, SBOM, vulnerability handling and conformity assessment workflow.
For a broader view of CRA documentation requirements, you can also refer to our guide Cyber Resilience Act Technical Documentation: Complete Guide, and for component transparency, see CRA SBOM Requirements.
1. What Is the CRA Technical File?
Under the Cyber Resilience Act, manufacturers must prepare and keep technical documentation that demonstrates conformity of the product with digital elements to the CRA’s essential cybersecurity requirements. This set of documentation is often referred to informally as the CRA technical file.
The CRA technical file structure is not just a legal formality. It is the central place where you:
- Describe what the product is and how it is intended to be used
- Explain the architecture and components, including third party and open source software
- Document your cybersecurity risk assessment and the rationale for your controls
- Show how you meet the CRA security requirements in Annex I
- Provide evidence of testing, validation and vulnerability handling
- Record your lifecycle commitments, such as update support and end of life policy
A good CRA technical file is readable, traceable and easy to maintain. It enables a regulator, a notified body or an internal auditor to understand your product and to see how each requirement is covered without searching through fragmented spreadsheets and emails.
2. Principles for a Good CRA Technical File Structure
Before defining specific sections, it is useful to align on a few core principles that should guide your CRA technical file structure:
2.1 Traceability from risk to controls
Your technical file should link product risks to the security measures you selected. A reviewer should be able to follow the chain: threat → risk → control → evidence. This traceability is at the heart of Cyber Resilience Act compliance and will matter even more for important and critical products.
2.2 Consistency across products
If you manufacture several products with digital elements, the CRA technical file structure should be consistent across them. Reusing the same template and section layout saves time, reduces errors and makes internal reviews much easier.
2.3 Separation of product specific and reusable content
Some information is product specific (architecture diagrams, test results), while other content is reusable (corporate secure development lifecycle, generic vulnerability handling process). A good CRA technical file structure reuses global policies where possible and adds product specific annexes instead of duplicating everything.
2.4 Up to date and lifecycle oriented
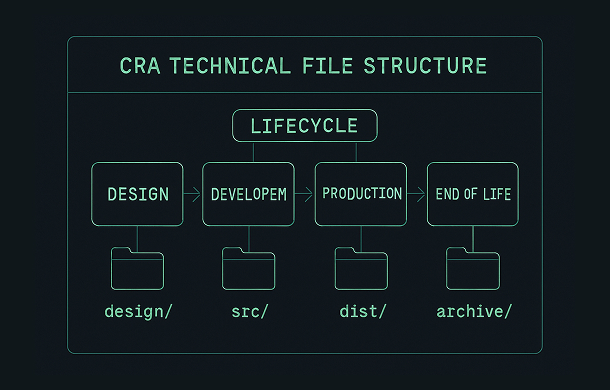
The CRA technical file is not a one time snapshot. It must be maintained as the product evolves: new versions, new features, security patches, changes in components. Your structure should make it easy to track versions and to keep documentation aligned with the actual product.
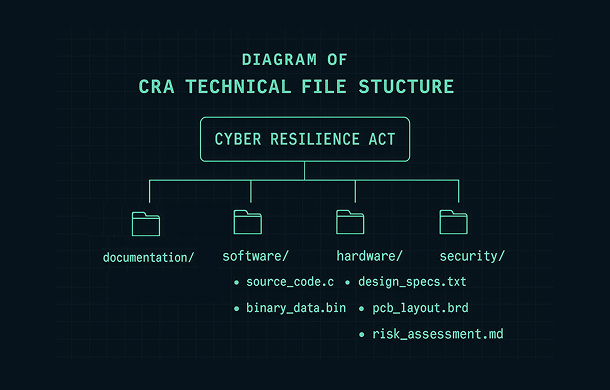
3. Recommended CRA Technical File Structure
There is no single mandatory format, but most organisations converge on a similar CRA technical file structure. Below is a recommended layout that aligns with the Cyber Resilience Act and can be adapted to your internal tools (DMS, wiki, GRC platform or a specialised CRA documentation tool such as Regulus).
3.1 Section 1 – Product overview and identification
The first part of your CRA technical file structure should introduce the product clearly:
- Product name and model(s)
- Version(s) covered by this technical file
- Intended purpose and use cases
- Target users or environments (consumer, enterprise, industrial, etc.)
- Regions and markets (EU, specific Member States)
- High level description of main features
This section anchors the technical file and provides context for the rest of the documentation. It should also clarify if the product is a complete system, a component, a software module or a combination of hardware and software.
3.2 Section 2 – Roles and CRA applicability summary
In this section, you summarise your CRA applicability and role analysis:
- Whether the product is in scope as a product with digital elements
- CRA product category (default, important or critical) and justification
- Economic operator role(s) assumed by your organisation (manufacturer, importer, distributor)
- Any relevant sector specific frameworks that modify or complement CRA (e.g. MDR, automotive regulations)
Here it is useful to reference internal analysis based on our article Cyber Resilience Act Applicability: Does the CRA Apply to Your Product? and CRA Scope: What Products Are In and Out.
3.3 Section 3 – System architecture and data flows
This part of the CRA technical file structure explains how the product is built and how it interacts with other systems:
- Logical architecture diagrams (components, modules, services)
- Network architecture and trust boundaries
- Data flow diagrams (what data moves where, and under which protection)
- Interfaces exposed (APIs, management ports, protocols)
Architecture and data flow diagrams are critical for understanding attack surfaces, responsibilities and where specific CRA security requirements are implemented.
3.4 Section 4 – Cybersecurity risk assessment
The CRA requires manufacturers to carry out a cybersecurity risk assessment as part of the design and development process. This section:
- Describes the methodology used (e.g. threat modelling, STRIDE, attack trees, IEC 62443 inspired)
- Lists threats and scenarios relevant to the product
- Identifies assets, potential impacts and likelihood
- Prioritises risks and links them to the security controls applied
If you already follow a structured approach to risk under NIS2 or ISO 27001, you can reuse parts of that framework here, but the analysis must focus on the specific product with digital elements. For a conceptual overview of risk work under CRA, see our CRA Risk Assessment Guide.
3.5 Section 5 – Mapping to CRA security requirements
One of the key elements of a CRA technical file structure is a clear mapping between the product and the CRA essential security requirements. A typical way to present this is a requirements matrix that:
- Lists the CRA security requirements (for example, secure by default, access control, logging, update mechanisms)
- Describes how each requirement is implemented in the product
- References specific design documents, code modules or configuration standards
- Links to test cases and evidence showing that the requirement is effectively met
In Regulus, this mapping is part of the Requirements Matrix module, which helps you move from abstract CRA text to concrete, product specific obligations.
3.6 Section 6 – Software Bill of Materials (SBOM) and components
Because the CRA expects manufacturers to maintain an inventory of software components, the technical file should include or reference an up to date SBOM:
- List of all relevant software components and libraries
- Version and supplier for each component
- Open source and third party identifiers (e.g. package names, repositories)
- Licensing information when relevant to security and support
The SBOM section of your CRA technical file structure should also explain how the SBOM is generated, maintained and used for vulnerability correlation. For more depth on expectations, see CRA SBOM Requirements.
3.7 Section 7 – Secure development lifecycle (SDL)
This section documents how the product is built securely over time:
- Overview of your secure development lifecycle (SDL) or equivalent framework
- Security activities per phase: design reviews, threat modelling, secure coding guidelines, code review, SAST/DAST, dependency scanning
- Roles and responsibilities (product security champions, security reviewers)
- Integration of security in CI/CD pipelines
You can reference a corporate SDL policy and then include product specific details in this technical file. When you later create a dedicated article on Secure Development Lifecycle under the CRA, you can link to it from this section.
3.8 Section 8 – Security testing and validation evidence
Regulators and notified bodies will expect to see evidence that security controls have been tested. This section of the CRA technical file structure typically contains:
- Security test strategy and scope
- Results of functional security tests
- Results of fuzzing, penetration testing or red teaming where applicable
- Dependency scanning and vulnerability scanning reports
- Fix tracking for critical findings before product release
It is good practice to summarise conclusions in a short security validation report and attach detailed reports as annexes.
3.9 Section 9 – Vulnerability handling process and CVD
The CRA explicitly requires a structured vulnerability handling process. This part of your technical file should:
- Describe how vulnerabilities are reported, triaged and prioritised
- Explain your Coordinated Vulnerability Disclosure (CVD) policy
- Identify your public contact channels for vulnerability reporting
- Document timelines and SLAs for addressing vulnerabilities
- Show how you document and communicate resolved vulnerabilities
For a detailed breakdown of what this entails, see CRA Vulnerability Handling Requirements (Annex I – Section 2).
3.10 Section 10 – Update and patch management
This section of the CRA technical file structure explains how the product receives updates:
- Update architecture (over the air, local updates, staged rollouts)
- How update packages are signed, validated and applied securely
- Segregation between security updates and feature updates where possible
- Notification mechanisms to inform users about security updates
- Support period and end of security updates for each version
Update and patch management are central to ongoing Cyber Resilience Act compliance. They connect your design assumptions to real world operations and incident exposure.
3.11 Section 11 – Post-market monitoring and incident handling
Post-market monitoring is how you detect problems once the product is in use. This section should cover:
- How you collect signals about security issues (logs, telemetry, customer reports)
- How you track and investigate incidents affecting the product
- How you coordinate CRA related incident notifications where required
- How you feed lessons learned back into risk assessment and product improvement
3.12 Section 12 – Lifecycle, support and end-of-life
The CRA is explicit about lifecycle security. In this part of your technical file, document:
- Planned lifetime of the product versions covered
- Period during which you commit to provide security updates
- End-of-life policy and communication to customers
- Migration or replacement recommendations when security support ends
3.13 Section 13 – EU Declaration of Conformity (DoC) and references
Finally, your CRA technical file structure should point to your EU Declaration of Conformity and any other declarations or certificates (for example, under other EU product regulations or cybersecurity certification schemes). It is common to:
- Include a copy of the DoC as an annex
- Reference harmonised standards or specifications you rely on
- List relevant certificates and assessment reports from notified bodies
4. How the CRA Technical File Fits into Your Compliance Workflow
The CRA technical file is not an isolated document; it sits at the intersection of product development, security and regulatory compliance. In a mature workflow:
- Product managers use it to understand constraints and obligations
- Engineering teams contribute architecture, code level and testing details
- Security teams contribute risk assessments, SBOMs and vulnerability handling evidence
- Compliance teams coordinate structure, versioning and conformity assessment outputs
Ideally, your CRA technical file structure mirrors the way your teams work. If you try to maintain it only as a static PDF, it will quickly become outdated. Many organisations choose to manage the technical file in a documentation system, GRC tool or a specialised CRA platform such as Regulus.
5. Common Mistakes in CRA Technical File Structure
When organisations start building CRA technical documentation, they often make similar mistakes. Typical issues include:
5.1 Mixing policy and product detail without structure
Global security policies and product specific implementations are mixed together in an unstructured way, making it difficult for reviewers to understand what applies to which product. A clearer CRA technical file structure separates global policies from product level details and links them instead of merging everything into one document.
5.2 No clear mapping to CRA requirements
Technical documentation often describes many security features but fails to explicitly show how each CRA requirement is covered. A requirements matrix or mapping table is essential to make Cyber Resilience Act compliance visible and auditable.
5.3 SBOMs not integrated into the technical file
Some teams generate SBOMs as standalone artefacts but never integrate them into the CRA technical file. The result is a gap between component inventory and other documentation. In a robust CRA technical file structure, the SBOM is referenced, explained and linked to vulnerability handling and testing processes.
5.4 Documentation created too late
Teams wait until just before release to start the technical file, which leads to guesswork and missing evidence. The CRA technical file should evolve together with the product, starting from architecture and risk assessment through to validation and post-market monitoring.
6. How Regulus Helps You Build a CRA Technical File Structure
Regulus is designed to make Cyber Resilience Act compliance more manageable for manufacturers of IoT devices, embedded systems, firmware based products and other connected solutions. Instead of maintaining a patchwork of spreadsheets and documents, Regulus provides:
- A structured CRA requirements matrix aligned with your product profile
- Guided workflows for CRA scope and applicability
- Support for documenting your CRA technical file structure in a consistent way
- Templates for risk assessment, SBOM, vulnerability handling and update management documentation
- Roadmap views that connect documentation work with 2025–2027 CRA timelines
If you are starting to design your CRA technical file structure and want to avoid reinventing everything from scratch, you can:
- Download our CRA Readiness Checklist to identify your main gaps.
- Review our documentation focused guides in the Resources section.
- Join the Regulus Early Access program to get priority access to CRA documentation workflows.