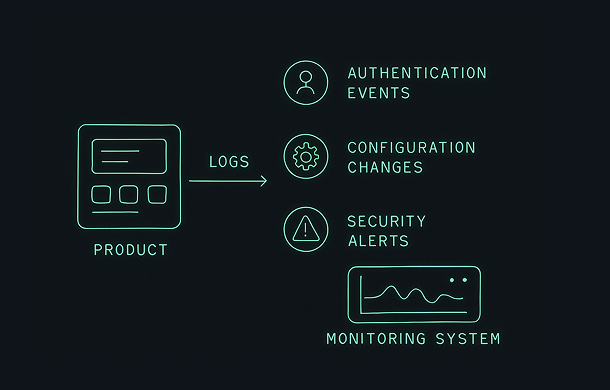
CRA logging and monitoring is one of the most practical aspects of Cyber Resilience Act compliance. Even if your product has strong security controls, you cannot demonstrate or maintain that security over time without structured logging, event monitoring and security-relevant telemetry. For manufacturers of products with digital elements, logging and monitoring are central to detecting incidents, supporting investigations and proving compliance.
This guide explains how to design CRA logging and monitoring for your product: what to log, how to protect logs, how long to retain them, how to implement monitoring in constrained IoT and embedded environments, and how logging connects to vulnerability handling, incident response and your CRA technical documentation.
If you are building your overall CRA documentation, you may also want to review our guides on CRA risk assessment, CRA vulnerability handling requirements and CRA technical file structure.
1. Why CRA Logging and Monitoring Matter
The Cyber Resilience Act expects products with digital elements to support appropriate logging and monitoring of security-relevant events. This serves several purposes:
- Detection: identify attacks, misuse and abnormal behaviour before they escalate.
- Investigation: reconstruct what happened after an incident using reliable audit trails.
- Evidence: demonstrate that security controls operate as intended in real deployments.
- Feedback: feed real-world data back into your CRA risk assessment and hardening efforts.
Without structured CRA logging and monitoring, you risk being unable to detect incidents that must be reported, unable to understand their root cause, and unable to prove that your product behaves in line with your technical documentation and security claims.
2. Principles for CRA Logging and Monitoring
Before defining specific events and fields, it helps to anchor logging and monitoring design on a small set of principles that align with Cyber Resilience Act expectations.
2.1 Security-relevant, not everything
CRA does not require logging every possible event. Instead, you should identify security-relevant events based on your risk assessment: authentication, authorisation, configuration changes, security control status, update failures and so on. Log what is necessary to detect and investigate security issues, not every minor detail.
2.2 Privacy-aware and data-minimising
Logs should not become a source of unnecessary personal data exposure. Under the CRA and broader EU law, you must balance security visibility with data minimisation, pseudonymisation or anonymisation where feasible. Avoid including full credentials, sensitive payload data or unnecessary identifiers in logs.
2.3 Integrity and tamper resistance
For CRA logging and monitoring to be meaningful, logs must be trustworthy. You should protect logs against tampering and unauthorised deletion, for example by:
- Restricting access to log storage
- Using append-only or write-once mechanisms where possible
- Applying cryptographic integrity checks or signatures for critical logs
2.4 Lifecycle-oriented
Logging and monitoring must cover the entire product lifecycle: boot and installation, normal operation, updates, configuration changes and decommissioning. CRA expects lifecycle security, and your logs should reflect that lifecycle.
3. What to Log Under CRA Logging and Monitoring Requirements
The specific events to log depend on your product, but most CRA-compliant logging strategies include at least the following categories.
3.1 Authentication and access control events
These are central to CRA logging and monitoring because they show who accessed what, when and how:
- Successful and failed login attempts (user, admin, API keys, device credentials)
- Multi-factor authentication challenges and failures
- Account lockouts, password resets and credential changes
- Privilege changes (e.g. user granted or revoked administrator role)
3.2 Configuration and security setting changes
Changes that affect security posture or behaviour should always be logged:
- Enabling or disabling security features (firewalls, encryption, logging itself)
- Changes to access control lists, roles or permissions
- Modification of network endpoints, APIs or integration settings
- Changes in update policy or patch channels
3.3 Software, firmware and configuration updates
Because the Cyber Resilience Act emphasises secure updates, you should log:
- Attempts to download and apply updates (including failures)
- Successful installation of firmware or software updates
- Verification of update signatures or integrity checks
- Rollback events or reversion to previous versions
These logs are crucial when demonstrating that you applied patches in a timely manner and that your update mechanisms worked as documented.
3.4 Security control status and anomalies
Key security controls in the product should generate logs when:
- They are enabled, disabled or misconfigured
- They detect unusual or suspicious behaviour (e.g. rate limits triggered, brute-force attempts)
- They fail or degrade (for example, logging pipeline is full or offline)
3.5 Application- and domain-specific events
Depending on your product category, you may need to log additional domain-specific events, for example:
- For industrial devices: safety overrides, emergency stops, unexpected state transitions
- For IoT: pairing/unpairing events, device resets, remote commands received
- For security products: detection of malware, blocked connections, quarantine actions
4. Log Content: Fields and Structure
Effective CRA logging and monitoring depends not only on which events you log but also on how you structure log entries. A minimum set of fields typically includes:
- Timestamp with timezone
- Event type (e.g. auth_success, auth_failure, config_change, update_start, update_success)
- Actor (user ID, device ID, process ID, API client)
- Origin (IP address, hostname, interface)
- Target (resource modified or accessed)
- Outcome (success, failure, partial)
- Diagnostic data (codes, reason messages, error identifiers)
Using a consistent, machine-readable format (such as JSON) greatly simplifies downstream analysis and integration into SIEM or log management platforms.
5. Log Retention, Protection and Access Control
Once you generate logs, you must retain and protect them appropriately to support Cyber Resilience Act compliance.
5.1 Retention period for CRA logs
The CRA does not define a universal retention period, but you should select periods that:
- Support detection and investigation of security incidents over a reasonable timeframe
- Align with your vulnerability handling and incident reporting obligations
- Respect data protection and storage limitation principles
Many organisations adopt retention policies in the range of several months to a few years for security logs, depending on risk and regulatory expectations in their sector.
5.2 Protecting log integrity
From a CRA perspective, logs must be reliable as evidence. Protection techniques can include:
- Storing logs in separate, hardened infrastructure
- Using append-only storage or write-once media for high-value audit logs
- Applying cryptographic signatures or hash chains to detect tampering
- Replicating logs to a central server external to the device or product
5.3 Controlling access to logs
Access to raw and aggregated logs should be restricted to authorised personnel and tools. Good practices include:
- Role-based access control for log platforms
- Separation of duties between administrators and auditors
- Logging access to logs themselves for auditability
6. Monitoring, Alerting and Integration with Incident Response
Logging alone is not enough. CRA logging and monitoring also implies that you actively monitor and act on log data.
6.1 Baseline monitoring
Baseline monitoring includes dashboards and alerts for:
- Authentication failures above normal thresholds
- Unusual patterns of configuration changes
- Update failures across a fleet of devices
- Repeated triggering of security controls (e.g. rate limits or WAF blocks)
6.2 Integration with incident response processes
Logs and monitoring must feed into your vulnerability handling and incident response processes. When an incident is suspected:
- Monitoring should trigger an alert and open an investigation record
- Investigators should have access to correlated logs from relevant components
- Response actions (blocking accounts, isolating devices, applying patches) should themselves be logged
For a deeper view of incident-related processes, see our guide on CRA vulnerability handling requirements.
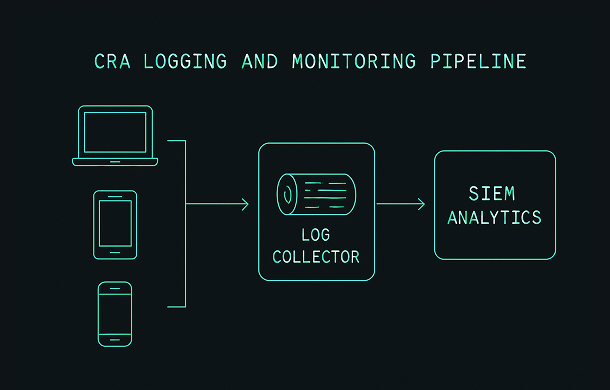
6.3 Fleet and cloud-side monitoring for IoT and embedded products
For IoT and embedded devices, local logging may be limited due to storage and power constraints. In these cases, CRA logging and monitoring typically involves:
- Lightweight local logs for critical events
- Periodic upload or streaming of key events to a backend
- Aggregation, correlation and alerting in a central platform
The CRA does not prescribe specific architectures, but expects that your overall design supports effective detection and response across the lifecycle of the product.
7. Documenting CRA Logging and Monitoring in the Technical File
From a documentation perspective, your CRA technical file should describe your logging and monitoring approach clearly enough that auditors and authorities can understand it.
Typical elements in the technical file include:
- Overview of logging architecture (on-device, edge, cloud, SIEM)
- List of main event categories logged (auth, config, updates, security controls)
- Retention and protection measures for logs
- How monitoring is performed and how alerts are integrated into incident response
- How log data contributes to post-market monitoring and risk reassessment
For structuring this documentation, you can reuse the structure suggested in our CRA technical file structure guide.
8. Common Pitfalls in CRA Logging and Monitoring
When implementing CRA logging and monitoring requirements, manufacturers often encounter similar pitfalls. Being aware of them helps you design a more robust approach.
8.1 Logging too little
Under-logging may save storage and bandwidth but leaves you blind when incidents occur. If you cannot reconstruct what happened, you weaken both your security posture and your CRA compliance position.
8.2 Logging too much, without structure
On the other hand, logging everything without structure can overwhelm your monitoring tools and teams. Focus on security-relevant events, and standardise fields and formats to keep logs usable.
8.3 Storing logs only on the device
If all logs are stored locally and can be wiped by an attacker or by a device reset, they are of limited value. Wherever possible, forward at least summary logs to a central location under your control.
8.4 Ignoring privacy considerations
Logs that contain excessive personal data or sensitive payloads may create GDPR and privacy risks. Align CRA logging and monitoring with data protection principles and minimise what you store.
8.5 Monitoring that is not actionable
Dashboards and metrics are useful, but CRA expects that security events lead to action when needed. Alerts must be tuned, assigned and integrated into real incident response workflows.
9. How Regulus Helps with CRA Logging and Monitoring
Regulus is building tools to help manufacturers, IoT vendors and embedded system teams operationalise Cyber Resilience Act compliance, including CRA logging and monitoring requirements. Instead of dealing with scattered documents and ad-hoc log designs, our goal is to provide:
- Guided mappings from CRA security requirements to concrete logging and monitoring needs
- Templates for logging and monitoring sections in your CRA technical file
- Checklists to validate that key event categories and lifecycle phases are covered
- Support for aligning logging with vulnerability handling, update management and post-market monitoring
To move forward:
- Download the CRA Readiness Checklist to assess your current logging and monitoring gaps.
- Review our CRA documentation and requirements guides in the Resources section.
- Join the Regulus Early Access program to get priority access to CRA compliance tooling.