A CRA secure development lifecycle is one of the most effective ways to operationalise Cyber Resilience Act requirements. The CRA expects manufacturers of products with digital elements to design, develop, test and maintain their products in line with security-by-design and security-by-default principles. Without a structured secure development lifecycle (SDL), it is difficult to show that your products systematically meet those expectations.
This guide explains how to build a CRA secure development lifecycle that fits your organisation and product portfolio. It covers SDL phases, concrete security activities, documentation requirements and how SDL links to CRA obligations such as risk assessment, vulnerability handling, updates, logging and technical documentation.
For broader context on Cyber Resilience Act obligations, you may want to review our articles on CRA requirements, scope and how to prepare, CRA risk assessment and CRA technical documentation.
1. Why the CRA Secure Development Lifecycle Matters
The Cyber Resilience Act does not use the term “SDL” formally, but its core ideas are embedded in the essential cybersecurity requirements and lifecycle obligations. A CRA secure development lifecycle matters because it:
- Translates high-level CRA security requirements into repeatable engineering activities.
- Reduces the risk of introducing avoidable vulnerabilities during development.
- Provides evidence that security-by-design and security-by-default are applied in practice.
- Supports vulnerability handling, updates and post-market monitoring across the product lifecycle.
Without an SDL, security improvements tend to be reactive, ad hoc and difficult to document in the CRA technical file. With a lightweight but structured CRA secure development lifecycle, security becomes an integral part of how products with digital elements are built and maintained.
2. What the CRA Expects from Secure Development
The Cyber Resilience Act expects manufacturers to ensure that products with digital elements:
- Are designed, developed and produced in accordance with essential cybersecurity requirements.
- Implement security-by-design and security-by-default principles.
- Support secure configuration, secure updates and secure communication.
- Remain secure throughout their expected lifecycle, with appropriate vulnerability handling.
These expectations are not satisfied by a single technical control or penetration test. Instead, they require an underlying CRA secure development lifecycle that connects requirements, design, implementation, testing and maintenance in a coherent way.
To build this lifecycle, you should align it with your CRA risk assessment, your vulnerability handling processes and your CRA logging and monitoring approach.
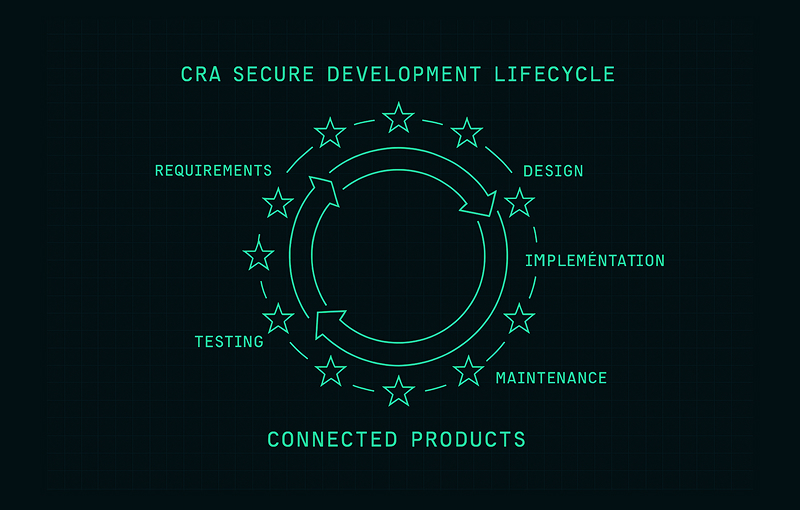
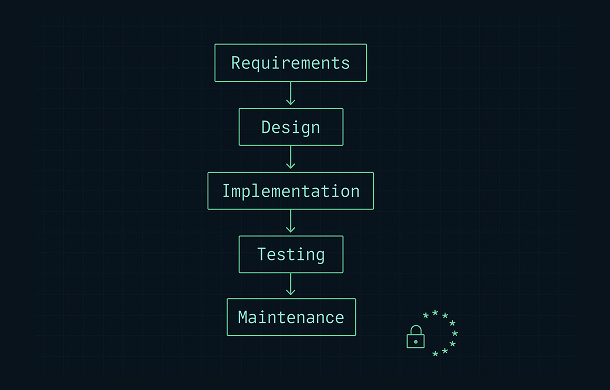
3. Core Phases of a CRA Secure Development Lifecycle
A CRA secure development lifecycle can be implemented in various ways, but most organisations follow a set of recurring phases. Whether you use agile, waterfall or hybrid models, you can map these phases to your existing process.
3.1 Requirements and planning
In the requirements phase, your SDL should ensure that:
- Product requirements explicitly include security and CRA-related objectives.
- Non-functional requirements cover security, privacy and resilience.
- Regulatory requirements, including CRA and other EU acts, are identified for the product.
- Assumptions about the operating environment, threats and dependencies are documented.
This is where you connect your CRA secure development lifecycle to your product classification and requirement mapping work.
3.2 Architecture and design
In the design phase, CRA expectations around security-by-design become concrete:
- Architectural diagrams show components, interfaces and trust boundaries.
- Security controls are selected to mitigate assessed risks.
- Security-by-default decisions are documented (e.g. default disabled services, minimum privileges).
- Threat modelling is performed for critical components and data flows.
Design reviews should explicitly verify that CRA security requirements are addressed by the proposed architecture.
3.3 Implementation and secure coding
During implementation, the CRA secure development lifecycle focuses on secure coding and dependency hygiene:
- Developers follow secure coding guidelines relevant to the languages and platforms used.
- Static application security testing (SAST) or linters are integrated into the build pipeline where feasible.
- Dependencies are managed carefully, feeding into your CRA SBOM.
- Sensitive information such as secrets, keys or credentials is handled via secure mechanisms, not hard-coded.
3.4 Verification, validation and security testing
Testing under a CRA secure development lifecycle goes beyond functional checks:
- Unit and integration tests include security-relevant behaviours (e.g. access control, error handling).
- Security testing methods, such as SAST, DAST (dynamic testing) or fuzzing, are applied where appropriate.
- Abuse cases and negative scenarios are tested, not only normal user flows.
- Findings are triaged, tracked and fixed, with evidence stored for the technical file.
3.5 Release and deployment
Before release, CRA SDL activities should include:
- Security sign-off or a final review of high and critical findings.
- Verification that security configuration defaults are correct in production builds.
- Packaging of release artifacts in a way that supports secure update mechanisms.
- Documentation updates, including user-facing security information and internal technical documentation.
3.6 Maintenance, updates and post-market monitoring
After release, the CRA secure development lifecycle connects to vulnerability handling, monitoring and updates:
- Field feedback, vulnerability reports and incident data feed back into the SDL.
- Security updates follow a documented process with regression and security testing.
- Configuration of logging and monitoring is periodically reviewed and improved.
- Lessons learned are incorporated into future design and coding practices.
4. Mapping CRA Requirements to SDL Activities
To be useful for CRA compliance, your SDL should directly support Cyber Resilience Act requirements. A practical way to approach this is to map requirements to activities and artifacts.
4.1 Risk assessment and design decisions
Your CRA risk assessment should be an input to SDL activities:
- Identified threats and vulnerabilities drive architectural choices.
- High-risk areas receive additional security testing and scrutiny.
- Risk acceptance decisions are documented and visible in SDL reviews.
This mapping shows that SDL is not isolated from your risk analysis but actively implements its results.
4.2 Security-by-default and configuration management
CRA expects secure defaults at deployment. SDL contributes by:
- Documenting default configurations and their rationale.
- Ensuring that insecure options are either unavailable or clearly documented with warnings.
- Including configuration validation in test suites.
4.3 Logging, monitoring and evidence generation
SDL should ensure that logging and monitoring are considered from the start:
- Security-relevant events are identified in design and implemented as part of development.
- Log formats and fields are standardised for later analysis.
- Tests verify that critical events are logged as expected.
This supports your CRA logging and monitoring approach and the evidence required in the technical file.
4.4 Vulnerability handling and update mechanisms
A CRA secure development lifecycle also defines how code changes, updates and patches are integrated:
- Bug and vulnerability tracking systems are aligned with your CRA vulnerability handling process.
- Update mechanisms are designed for secure delivery and validation from the beginning.
- Release notes and documentation capture security-relevant changes.
5. Practical Controls in a CRA Secure Development Lifecycle
Beyond phases and mappings, the SDL becomes real through specific controls and practices. Below is a non-exhaustive list of practical measures that support a CRA secure development lifecycle.
5.1 Secure coding guidelines and training
- Adopt secure coding standards relevant to your technologies (for example, CERT, MISRA, OWASP).
- Provide periodic training on secure coding and CRA-related security expectations.
- Maintain quick-reference materials for common pitfalls in your stack.
5.2 Code review with security focus
- Mandate peer review for changes in security-sensitive components.
- Use review checklists that include access control, error handling, logging and data validation.
- Ensure reviewers have the necessary context about CRA and product-specific risks.
5.3 Automated security testing
- Integrate SAST tools into CI pipelines where appropriate.
- Use DAST or integration-level security tests for exposed interfaces and APIs.
- For critical components, consider fuzz testing to uncover edge-case failures.
5.4 Dependency and SBOM management
- Use a package and dependency management strategy that avoids uncontrolled libraries.
- Generate and maintain an SBOM as part of your build process.
- Monitor public vulnerability feeds and advisories relevant to your SBOM components.
5.5 Secure build and release
- Protect build pipelines against tampering (access control, isolation, integrity checks).
- Use reproducible or deterministic builds where feasible for critical products.
- Sign release artifacts and updates to support secure distribution.
6. Documenting the CRA Secure Development Lifecycle
From a CRA perspective, it is not enough to run a secure development lifecycle; you must be able to show how it works. Documentation of the CRA secure development lifecycle should include:
- High-level description of the SDL process and phases.
- Roles and responsibilities for security-related activities.
- Templates or examples of threat models, risk assessments and review checklists.
- Policies for code review, testing and release approval.
- Links between SDL artifacts and CRA technical documentation sections.
This documentation becomes part of your CRA technical file and can be referenced in conformity assessments and audits.
7. Adapting CRA SDL to Different Product Types
Not all products with digital elements are the same. A good CRA secure development lifecycle is tailored to your product category and constraints, while keeping core security principles intact.
7.1 IoT and consumer devices
- Focus on secure onboarding, pairing and remote update mechanisms.
- Address constrained hardware in logging, encryption and update design.
- Consider usability when designing secure defaults for non-technical users.
7.2 Industrial and OT systems
- Account for safety implications in risk assessment and SDL decisions.
- Address long product lifecycles and legacy integration constraints.
- Align SDL practices with existing industrial security standards where relevant.
7.3 Software-heavy and hybrid products
- Integrate SDL with existing DevOps or DevSecOps practices.
- Pay special attention to cloud connectivity, APIs and data flows.
- Ensure that distributed components (clients, agents, services) are all covered by the SDL.
8. Common Mistakes in CRA Secure Development Lifecycles
When organisations start formalising a CRA secure development lifecycle, they often encounter similar pitfalls.
8.1 Treating SDL as a document, not a process
Writing an SDL policy is easy; changing how development is actually done is harder. CRA compliance depends on the process being followed in practice, not only on having a documented procedure.
8.2 Overloading teams with heavyweight processes
An SDL that is too heavy can slow development to a crawl and generate resistance. A practical CRA SDL focuses on a small number of high-impact security activities that fit the team’s way of working.
8.3 Ignoring feedback from post-market incidents
If lessons from incidents, customer feedback or penetration tests are not fed back into the SDL, the same issues will recur. CRA expects lifecycle security, which includes continuous learning.
8.4 SDL disconnected from suppliers and components
Many products rely on third-party software, libraries and hardware modules. A CRA secure development lifecycle must include mechanisms to evaluate, integrate and monitor these components, not just your own code.
8.5 No link between SDL and technical documentation
If SDL outputs and CRA documentation are maintained in silos, you will struggle to build a coherent technical file. Aligning templates, identifiers and structure from the start reduces friction later.
9. How Regulus Helps with CRA Secure Development Lifecycle
Regulus is focused on helping manufacturers, IoT vendors and embedded system teams implement the practical building blocks of Cyber Resilience Act compliance, including a CRA secure development lifecycle. Instead of relying solely on static documents, our goal is to provide:
- Guided mappings from CRA requirements to SDL activities across phases.
- Templates for risk assessment, threat modelling, review checklists and test evidence.
- Structure for integrating SBOM, logging and vulnerability handling into your SDL.
- Support for aligning SDL documentation with your CRA technical file and Declaration of Conformity.
To move forward:
- Download the CRA Readiness Checklist to identify gaps in your SDL and documentation.
- Explore our CRA documentation and requirements articles in the Resources section.
- Join the Regulus Early Access program to get early access to CRA workflows for documentation and development practices.