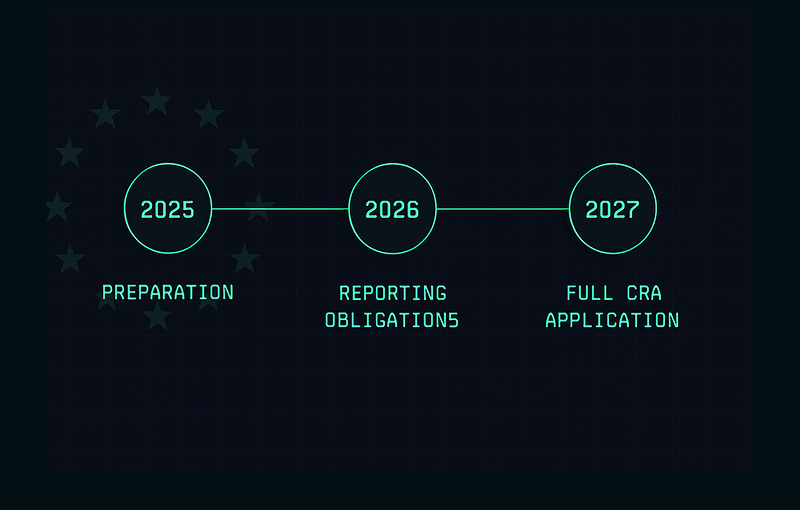
CRA deadlines 2025 2027 are not just abstract regulatory dates. They define when manufacturers, importers and distributors of products with digital elements must have their Cyber Resilience Act compliance in place. Many teams still assume that “everything happens in 2027”, but the first hard obligations arrive much earlier, especially around vulnerability reporting.
In this guide we break down the official Cyber Resilience Act timeline, explain what happens in 2025, 2026 and 2027, and show how to build a realistic CRA roadmap for your products. We will focus on what the CRA deadlines mean for manufacturers of connected devices, embedded systems, firmware-driven products and other products with digital elements.
For a broader overview of the regulation, see our article on Cyber Resilience Act requirements, scope and how to prepare, and for product-level analysis, read our CRA applicability guide.
1. CRA deadlines 2025 2027 at a glance
Before diving into practical planning, it is useful to have a clear picture of the main CRA deadlines 2025 2027. At a high level, the timeline looks like this:
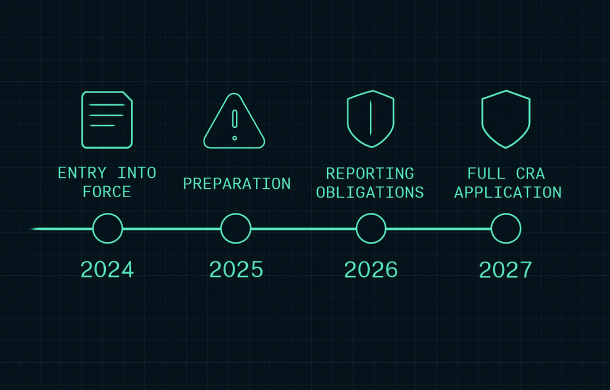
- December 2024: the Cyber Resilience Act enters into force at EU level.
- 2025: transition and preparation year – no hard application yet, but the clock is running and guidance begins to emerge.
- 11 June 2026: provisions on designation and notification of conformity assessment bodies start to apply (Chapter IV).
- 11 September 2026: vulnerability and incident reporting obligations (for actively exploited vulnerabilities and significant incidents) become mandatory.
- 11 December 2027: main CRA obligations become fully applicable; products with digital elements placed on the EU market must meet CRA cybersecurity, documentation and conformity assessment requirements.
From the perspective of a manufacturer, this means that serious reporting obligations start in 2026, while full product compliance (including CE marking under CRA) must be in place by December 2027 for new products placed on the market.
2. CRA timeline explained: from entry into force to full application
The CRA follows a familiar regulation pattern: entry into force, transition period, then full application. Understanding this structure is essential to interpret CRA deadlines 2025 2027 correctly.
2.1 Entry into force and transition period
The Cyber Resilience Act is already law at EU level. After entry into force, there is a multi-year transition period before most obligations apply to manufacturers and other economic operators. This is the window during which organisations are expected to:
- Map their product portfolio and determine CRA applicability.
- Perform initial CRA risk assessments for in-scope products.
- Design secure update, logging and vulnerability handling processes.
- Prepare technical documentation and conformity strategies.
Practically, the transition period is where you set up the foundations rather than wait for the final CRA deadline to react in a rush.
2.2 Early application of specific CRA obligations
Not all CRA provisions start at the same time. Some obligations are deliberately brought forward before full application, especially those that enable the whole framework:
- Notification and designation of conformity assessment bodies, so that they are ready before manufacturers need them.
- Vulnerability and incident reporting for products with digital elements, so that authorities have early visibility of serious issues.
This is why, in practice, 2026 is not a quiet year. It is when reporting expectations start to bite, even though full CE-level compliance under CRA only becomes mandatory in late 2027.
2.3 Full application of main obligations
From late 2027 onwards, the CRA is fully applicable. This means that products with digital elements placed on the EU market must:
- Meet the CRA essential cybersecurity requirements.
- Follow the appropriate conformity assessment route (internal control or third-party involvement, depending on classification and risk).
- Be supported by technical documentation and a Declaration of Conformity that covers CRA and other relevant legislation.
At this point, CRA becomes part of the standard regulatory backdrop alongside CE marking and sector-specific regulations.
3. What CRA deadlines mean in 2025
While there is no formal “2025 CRA deadline” in the regulation text, the year is strategically important. It is the first full year after entry into force and the earliest realistic starting point for serious CRA readiness work.
3.1 2025: inventory, applicability and gap analysis
In 2025, organisations should focus on building clarity rather than rushing into scattered implementation. Typical priorities include:
- Building a complete inventory of products with digital elements across the portfolio.
- Running high-level CRA applicability checks for each product (in scope vs out of scope, default vs higher-impact categories).
- Performing initial CRA risk assessments for representative products.
- Identifying major gaps in secure development, vulnerability handling, update mechanisms and documentation.
Our CRA Readiness Checklist is designed to support exactly this phase: mapping where you are today versus where you need to be by 2026–2027.
3.2 2025 for importers and distributors
Importers and distributors should also use 2025 to:
- Identify which supplier products fall under CRA scope.
- Clarify contractual responsibilities for vulnerability handling, updates and documentation.
- Plan how they will verify CRA conformity and documentation from 2027 onwards.
4. CRA deadlines in 2026: reporting obligations and infrastructure
The real “first hard date” in the CRA deadlines 2025 2027 is 11 September 2026
4.1 September 2026 – vulnerability and incident reporting
From 11 September 2026, manufacturers (and in some cases other economic operators) must:
- Report actively exploited vulnerabilities in their products with digital elements to the relevant EU-level bodies / national CSIRTs within defined timelines.
- Report significant cybersecurity incidents affecting the security of CRA-covered products.
- Maintain processes and evidence to show how they identify, analyse and remediate vulnerabilities.
Several legal and technical analyses point out that these obligations apply regardless of when the product was first placed on the market, which means legacy products still in support are within scope of the reporting framework.
4.2 What you should have in place by 2026
By the time reporting obligations go live, organisations should already have:
- A documented vulnerability handling process aligned with CRA expectations.
- Clear reporting lines, internal SLAs and responsibilities for vulnerability triage and incident response.
- Logging and monitoring capabilities sufficient to detect potential incidents involving their products.
- Initial versions of CRA technical documentation for key products, even if they will be refined before 2027.
If these foundations are not in place by 2026, it will be very difficult to satisfy reporting obligations in practice.

4.3 Conformity assessment ecosystem in 2026
In parallel, from mid-2026 onwards, Member States start designating and notifying conformity assessment bodies under CRA. This is a prerequisite for products that will require third-party assessment, and it is one reason why manufacturers cannot leave all conformity decisions to the last minute in 2027.
5. CRA deadlines in 2027: full application and market impact
The final and most visible milestone in the CRA deadlines 2025 2027 is the date when main obligations become fully applicable, currently planned for 11 December 2027.
5.1 What full application means for products
From full application onwards, when you place a product with digital elements on the EU market, you are expected to:
- Have implemented security-by-design and security-by-default controls aligned with CRA essential requirements.
- Have performed the appropriate conformity assessment route for that product (self-assessment vs notified body, depending on classification and risk).
- Maintain a CRA-compliant technical file, including risk assessment, architecture, security controls, testing evidence, logging and vulnerability handling descriptions.
- Issue and keep available a Declaration of Conformity that lists CRA and other applicable acts, and apply CE marking accordingly.
Products that do not meet CRA requirements may be restricted, withdrawn or prevented from being placed on the market, and supervisory authorities can apply administrative fines.
5.2 Existing vs new products at the 2027 deadline
A frequent question is what happens to products already on the market before full application. In simplified terms:
- New products placed on the market after the CRA full application date are expected to fully comply with CRA requirements.
- Existing products already in the field may still be affected by vulnerability reporting and support commitments, especially if you continue to ship updates or sell new units after the deadline.
This nuance makes it even more important to understand your product lifecycle, support policies and CRA roadmap well before 2027.
6. Building a CRA roadmap around deadlines 2025 2027
The most useful way to think about CRA deadlines is not as isolated dates, but as anchors for a structured roadmap. Below is a practical view of what to do in each period.
6.1 2025 – foundation and visibility
- Create and validate your inventory of products with digital elements.
- Run CRA applicability and classification for each product (or at least for your main families).
- Perform initial CRA risk assessments and identify high-risk products and components.
- Define your high-level CRA strategy: which products will be prioritised, which processes must change, who owns what.
6.2 2026 – processes and reporting readiness
- Formalise your vulnerability handling process and reporting playbooks.
- Implement logging and monitoring capabilities that support CRA detection expectations.
- Align secure development lifecycle (SDL) practices with CRA requirements for new releases.
- Produce the first versions of CRA technical documentation for priority products.
If you need guidance on SDL, see our article on CRA secure development lifecycle.
6.3 2027 – product-level conformity and documentation
- Complete technical files and risk documentation for in-scope products.
- Decide and apply the appropriate CRA conformity assessment routes per product.
- Finalise Declaration of Conformity templates that include CRA alongside other legislation.
- Prepare internal training and documentation so that sales, support and partners understand CRA implications.
7. CRA deadlines 2025 2027: FAQs for manufacturers
7.1 Do CRA deadlines apply to non-EU manufacturers?
Yes. CRA obligations apply based on where the product is placed on the market, not where the manufacturer is located. Non-EU manufacturers selling products with digital elements into the EU must meet the same deadlines and requirements as EU manufacturers.
7.2 What if we cannot meet CRA requirements by 2027?
If products with digital elements do not meet CRA requirements when placed on the EU market after full application, they may be restricted or withdrawn by market surveillance authorities. This makes early planning for CRA deadlines 2025 2027 essential.
7.3 Are pure SaaS products affected by CRA deadlines?
Pure SaaS services without distributed software, firmware or hardware are generally out of CRA scope, although they may be regulated by other frameworks (e.g. NIS2 or data protection law). However, SaaS that distributes agents, firmware, apps or controls devices with digital elements can fall under CRA, and therefore indirectly under these deadlines.
7.4 How do CRA deadlines interact with other regulations?
The CRA complements, but does not replace, other EU acts such as NIS2, sector-specific safety regulations or data-protection rules. For many organisations, CRA deadlines 2025 2027 will overlap with NIS2 implementation and evolving sectoral guidance.
8. How Regulus can help you plan for CRA deadlines 2025 2027
Regulus is focused on helping EU digital product companies structure their response to CRA deadlines 2025 2027 in a practical way. Instead of working with static spreadsheets and scattered notes, our goal is to provide:
- CRA scope and classification workflows that clarify which products are in scope before 2026.
- Requirements mapping that links CRA articles and essential requirements to concrete controls and documentation.
- Documentation templates for technical files, risk assessments, SBOM, vulnerability handling and CRA declarations.
- Readiness views and roadmaps aligned with the key CRA deadlines in 2026 and 2027.
To move forward:
- Download our CRA Readiness Checklist to assess your current position against CRA deadlines 2025 2027.
- Review the CRA basics and documentation guides in the Regulus Resources section.
- Join the Regulus Early Access list to receive updates on CRA tooling for scope analysis, documentation and roadmap tracking.