CRA Compliance
-

Shift to Left Security for EU CRA Compliance
To put it simply, shift to left is all about moving security and testing to the very beginning of the product development lifecycle, instead of treating them as an afterthought. If you picture the development process as a timeline from left to right, this strategy pulls critical checks from the far right (just before launch)…
-
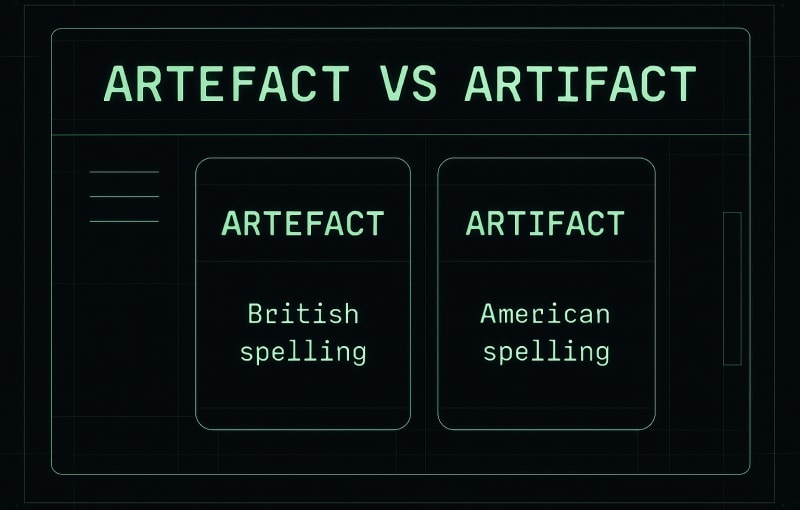
Artefact vs Artifact A Guide for Technical and Compliance Teams
When it comes to artefact vs artifact, the core of the issue isn’t about meaning—it’s about geography. The two words mean the exact same thing, but their spelling signals a regional preference. Think of it as the technical writing equivalent of “colour” versus “color.” The one you choose says a lot about your intended audience…
-

Master Terraform and Kubernetes with IaC for EKS, GKE, and AKS
When you bring Terraform and Kubernetes together, you create a single, declarative workflow for managing the entire lifecycle of your infrastructure and the applications running on it. This powerful pairing uses Infrastructure as Code (IaC) to automate everything from provisioning a cloud-managed cluster like EKS or GKE to deploying complex workloads, guaranteeing a setup that’s…
-
XDR vs EDR: Key Differences for Cyber Resilience (xdr vs edr)
When you get down to it, the difference between XDR and EDR is all about scope. Endpoint Detection and Response (EDR) is like posting a dedicated security guard at each individual device—think of a connected thermostat or a smart factory sensor. It’s hyper-focused on that single asset. In contrast, Extended Detection and Response (XDR) acts…
-
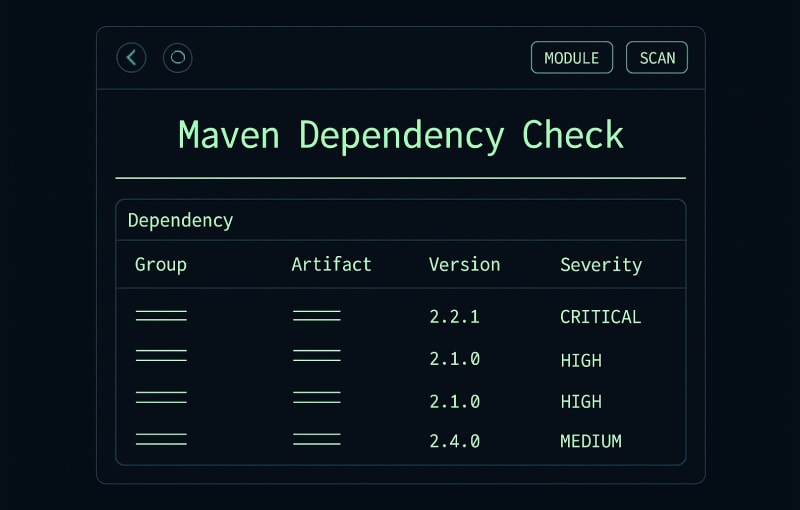
Mastering maven dependency check: A Quick Guide to Secure Builds
A proactive maven dependency check is more than just good practice—it’s a foundational part of securing your software supply chain. At its core, it’s about systematically scanning your project’s third-party libraries for known vulnerabilities, stopping security flaws from ever making their way into your codebase. Why Dependency Management Is a Security Blind Spot Let’s be…
-
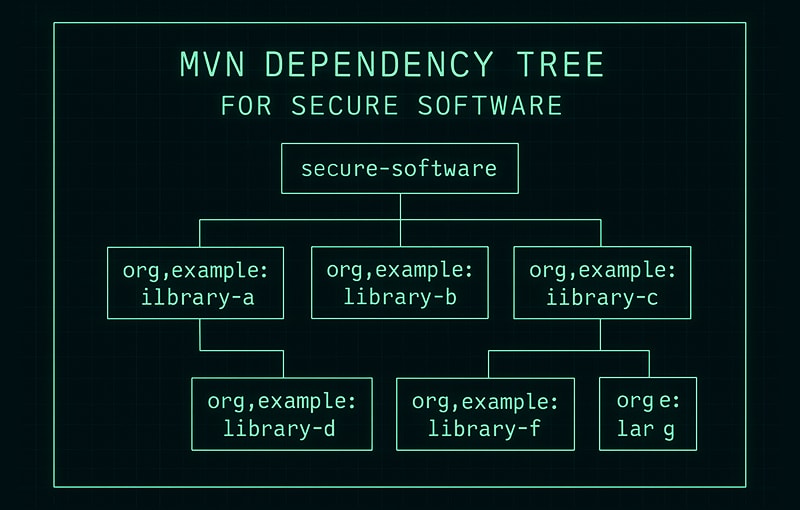
Mastering the Mvn Dependency Tree for Secure Software
When you’re working with Maven, the mvn dependency:tree command is your go-to for getting a complete, hierarchical picture of every library in your project. It doesn’t just show you the dependencies you’ve explicitly declared (direct ones), but also all the other libraries those dependencies pull in (transitive ones). Think of it as a detailed map…
-

Endpoint: endpoint protection services for IoT Cyber Resilience
Endpoint protection services are your dedicated security guard for every single device connected to a network—from a factory sensor to a smart thermostat. They provide the proactive defence and monitoring needed for individual entry points, which is absolutely vital as more and more products become internet-connected. For example, a modern car has over 100 electronic…
-
A Developer’s Guide to Docker RM Container
When you’re done with a Docker container, the docker rm command is your go-to tool for getting rid of it. You can target a container using its unique ID or its Name. Just be aware that Docker has a built-in safety net: it will throw an error if you try to remove a container that’s…
-
Maven vs Gradle Which Build Tool Is Right for Your Project?
The whole Maven vs Gradle debate really boils down to one thing: philosophy. Do you want a build tool that enforces a strict, conventional path using XML, or one that gives you a flexible, programmable toolkit with Groovy or Kotlin? Your answer depends entirely on whether your team values rigid standardisation for its predictability or…
-
Terraform vs CloudFormation A Guide for Manufacturers
The real difference between Terraform and CloudFormation boils down to a single question: Are you all-in on AWS, or do you need to keep your options open? Terraform is a cloud-agnostic tool built for multi-cloud, while CloudFormation is an AWS-native service designed for deep integration within its own ecosystem. Your choice here isn’t just technical—it’s…
-
A Practical Guide to Test SQL Injection for CRA Compliance
Test SQL Injection for CRA Compliance Testing for SQL injection isn’t just a technical best practice anymore; it’s a critical compliance mandate. For manufacturers selling products in the European Union, a single SQL injection (SQLi) flaw can trigger serious regulatory consequences under the Cyber Resilience Act (CRA), making proactive testing a non-negotiable part of your…
-
A Practical Guide to Security by Default for CRA Compliance
Security by default is a simple but powerful idea: the responsibility for making a product secure lies with the manufacturer, not the customer. It means building products to be as tough as possible right out of the box, with the safest settings already switched on. Security isn’t an optional extra; it’s part of the foundation.…
-
Anatomy of a Supply Chain Attack Your Guide to Defense
A supply chain attack is a bit like a Trojan horse, but for the modern digital world. Instead of launching a frontal assault on a well-defended target, attackers get clever. They find a crack in the armour of a trusted third-party supplier, vendor, or software component and slip in unnoticed. For example, instead of trying…
-

A Guide to Check Point Endpoint Security for EU Compliance
Check Point Endpoint Security isn’t just another antivirus program. Think of it as a complete security system for the devices that form the backbone of your operations—laptops, servers, and mobile phones. It provides multiple, overlapping layers of defence, including proactive threat prevention, access control, and data protection, to lock down the entry points into your…
-

A Practical Guide to NIST 800 53 for CRA Compliance
Think of NIST Special Publication 800-53 less like a rigid rulebook and more like an encyclopaedia of security best practices. It’s a massive catalogue of security and privacy controls developed for all U.S. federal information systems, excluding those tangled up in national security. For everyone else, it provides a foundational framework for managing risk and…
-

EU CRA revamp targets high risk vendors: Your Practical Compliance Roadmap
The European Union’s Cyber Resilience Act (CRA) is about to overhaul digital product safety, and its latest version puts high-risk vendors squarely in the spotlight with much stricter rules. If your company makes hardware or software with digital parts for the EU market, this isn’t just another update. It transforms cybersecurity from a “nice-to-have” into…
-
Testing for sql injection: Essential Guide to Secure Your Applications
At its heart, testing for SQL injection is about sending carefully crafted inputs to an application to see if you can trick its database. It’s a hands-on method for finding those dangerous cracks in the armour where an attacker could slip through, bypass security, steal data, or even corrupt your entire database. Proactive, effective testing…
-

How to obtain a CE certificate for the CRA: A practical guide
Getting your product CE certified under the Cyber Resilience Act (CRA) might seem daunting, but it’s a journey with a clear, logical path. This guide is your practical roadmap, designed to turn the CRA’s complex legal requirements into a straightforward, actionable plan for manufacturers. Your Practical Roadmap to CRA CE Certification The Cyber Resilience Act…
-
The Top 12 Firewall Open Source Solutions for 2026
In today’s interconnected environment, securing your network perimeter is non-negotiable. While commercial solutions abound, the firewall open source ecosystem offers powerful, flexible, and transparent alternatives for businesses, home labs, and even complex IoT projects. These community-driven projects provide robust security features without the hefty price tag or vendor lock-in, giving you complete control over your…
-

A Practical Guide to NIST SP 800-53 for EU Compliance
If you’ve spent any time in cybersecurity, you’ve likely come across NIST Special Publication (SP) 800-53. It’s a beast of a document, a massive catalogue of security and privacy controls developed by the U.S. National Institute of Standards and Technology. Although it started life as a framework for American federal agencies, it’s now recognised globally…
CRA Compliance: what it is and how to achieve it without unnecessary friction
CRA Compliance refers to meeting the requirements of the EU Cyber Resilience Act (CRA) for products with digital elements across their full lifecycle. For organizations that design, develop, import, distribute, or support connected hardware, software, or related services, CRA introduces a clear expectation: security by design, security by default, and continuous vulnerability handling over time.
This page brings together practical guidance and a curated set of related posts to help you understand CRA requirements, translate them into operational controls, and prepare defensible compliance evidence.
Who CRA applies to and why CRA Compliance matters
CRA Compliance is relevant if your organization participates in any part of a digital product’s value chain. CRA raises the baseline cybersecurity standard in the EU market by reducing exploitable vulnerabilities and pushing companies to adopt systematic risk management and lifecycle security.
Benefits of a structured approach to CRA Compliance
Beyond reducing regulatory exposure, CRA Compliance can strengthen your overall security posture, streamline customer audits, and improve trust in your product through demonstrable secure engineering and disciplined vulnerability management.
Key CRA Compliance requirements for products with digital elements
In practice, CRA Compliance translates into concrete obligations spanning governance, secure development, testing, vulnerability management, communication, and post-market support.
Security by design and by default
Embedding controls early avoids late rework and reduces remediation cost, while improving resilience in production environments.
Recommended practices for security by design
- Threat modeling from early product stages
- Least privilege and secure hardening baselines
- Appropriate authentication and encryption aligned to risk
- Secure configuration and secrets management
Vulnerability management and lifecycle obligations
CRA places strong emphasis on how vulnerabilities are discovered, triaged, fixed, and communicated, as well as how the product is maintained over time with security updates.
Typical evidence expected for vulnerability management
- A formal vulnerability management process
- Clear reporting channels and internal remediation SLAs
- Change records and traceability
- A support and security update policy
Technical documentation and traceable compliance
CRA Compliance is not only about doing the work, it is also about proving it. Documentation should substantiate security decisions, test outcomes, risk treatment, and maintenance commitments.
Documentation that is commonly useful for audits and assessments
- A component inventory (including SBOM where applicable)
- Risk assessments and mitigation decisions
- Testing evidence (SAST, DAST, penetration testing, reviews)
- Incident response and notification procedures
How to implement CRA Compliance in your organization
An effective approach combines regulatory mapping with engineering and operational practices, avoiding unnecessary bureaucracy while keeping evidence ready for inspection.
Step 1: define scope and responsibilities
Start by identifying which products are in scope, clarifying accountability, and establishing a governance model that aligns product, engineering, security, legal, and support teams.
Minimum kickoff checklist
- A catalog of products with digital elements
- Role ownership by function (product, engineering, security, legal, support)
- A map of critical dependencies and supply chain touchpoints
Step 2: map CRA requirements to controls and processes
Convert obligations into concrete controls within your SDLC and operational workflows so compliance becomes repeatable rather than a one-off effort.
Common operational controls
- A secure SDLC with security gates
- Dependency and supply chain security management
- Continuous vulnerability monitoring and patching
- Secure configuration baselines and access control policies
Step 3: build evidence and metrics
If it cannot be audited, it will not be trusted. Metrics help sustain CRA Compliance over time and demonstrate continuous improvement.
Suggested metrics
- Mean time to remediate vulnerabilities by severity
- Coverage of static and dynamic security testing
- Percentage of dependencies kept up to date
- Security incidents per release or version
Related posts and resources on CRA Compliance
This section is designed to host and continuously expand a library of content related to CRA Compliance, including implementation guidance, operational playbooks, and audit readiness resources.
Practical guides
How to prepare your organization for the Cyber Resilience Act
A practical overview of scope, typical decisions, and the fastest path to get started with CRA-aligned controls and documentation.
CRA Compliance and secure SDLC
How to integrate CRA requirements into product delivery workflows without slowing down teams or compromising time to market.
Vulnerability management and supply chain
SBOM and CRA Compliance: when it helps and how to implement it
What to expect from a component inventory, how it supports vulnerability response, and how to operationalize SBOM management.
Patching and update policy: support, versions, and communication
How to structure security updates, version support windows, and customer communication in a way that aligns with CRA expectations.
Audit and evidence
CRA Compliance evidence: what to document and how to keep it current
Recommended artifacts, traceability patterns, and lightweight governance practices to keep compliance defensible over time.
Download free CRA Checklist 2025
The definitive CRA checklist for assessing your organization’s readiness for the Cyber Resilience Act.
By submitting this form, you accept our Terms and acknowledge that Regulus will process your data to send the checklist. For more details, see our Privacy Policy.
