Uncategorized
-

Your Guide to the National Vulnerability Database
The National Vulnerability Database (NVD) is the U.S. government's public library for cybersecurity vulnerabilities. It takes the raw list of Common Vulnerabilities and Exposures (CVEs) and enriches it with crucial analysis, like severity scores and details on affected software. Think of it as the place that provides the full story behind every identified digital flaw.…
-

Path Traversal Attack Your Guide to CRA Compliant Security
A path traversal attack, sometimes called directory traversal, is a classic web security vulnerability that lets an attacker read—and in some cases, write to—files they should never be able to reach. It’s a simple but powerful trick. Attackers pull this off by manipulating file paths using the "dot-dot-slash" (../) sequence. Think of ../ as a…
-

Your Guide to Cross Site Scripting Attacks and Prevention
Cross-site scripting, or XSS, is one of the most persistent and damaging vulnerabilities plaguing the web. It’s a sneaky type of attack where a threat actor injects malicious code, usually JavaScript, into a legitimate website. When an unsuspecting user visits that site, their browser executes the script, believing it’s part of the trusted content. The…
-

A Practical Guide to SQL Injection Test Labs and Vulnerability Hunts
A SQL injection test is a security procedure we use to find vulnerabilities in an application’s database layer. It’s all about sending carefully crafted, malicious SQL queries to an input field—like a search bar or login form—to see if the application will blindly execute them. If it does, an attacker could potentially expose, manipulate, or…
-

A Practical Guide to the OWASP Top Ten for CRA Compliance in 2026
The OWASP Top Ten provides an essential framework for identifying the most critical security risks facing web applications, IoT devices, and embedded systems. For manufacturers targeting the European market, this list is no longer just a set of best practices. It has become a direct map to the security obligations mandated by the EU’s Cyber…
-
A Practical Guide to OWASP Dependency Check
OWASP Dependency-Check is a free, open-source Software Composition Analysis (SCA) tool that acts as your first line of defence against vulnerable third-party components. Think of it as an automated security guard for your project’s dependencies, constantly checking them against public vulnerability databases like the National Vulnerability Database (NVD). Modern software isn’t built from scratch. We…
-

A Practical Guide to Static Code Analysis
Think of static code analysis as a spellchecker, but for your source code. It’s an automated process that scans your code for potential errors, vulnerabilities, and deviations from best practices before you even try to run it. It’s like having an expert engineer meticulously review every line of a building’s blueprint for structural flaws before…
-
A Guide to Dynamic Application Security Testing for CRA Compliance
Dynamic application security testing (DAST) is a black-box security testing method that probes an application from the outside, mimicking exactly how a real-world attacker would approach it. DAST interacts with the application while it’s running—without any knowledge of its internal code or architecture—to find vulnerabilities that only show up during operation. This approach is essential…
-

Your Guide to the Secure Software Development Life Cycle
A secure software development life cycle (SDLC) is a framework that weaves security practices into every single stage of creating software. Instead of treating security as a final check before launch, it becomes a core part of the process from the very beginning. This concept is often called ‘Shift Left’, and it’s all about building…
-

A Guide to the Modern Product Lifecycle Manager
When you hear the term product lifecycle manager, it’s easy to get confused. Are we talking about a person or a piece of software? The answer is both. The term refers to two distinct but deeply connected concepts: a strategic professional role and a powerful software tool. Both are absolutely essential for steering a product…
-
Top 12 Supply Chain Softwares for EU Manufacturers in 2026
The European Union’s upcoming Cyber Resilience Act (CRA), set to be enforced from 2026, fundamentally changes the requirements for manufacturers. Selecting the right supply chain softwares is now a critical task, shifting from a focus purely on operational efficiency to one centred on compliance, security, and sustained market access. This guide is designed to help…
-
Cyber Resilience Act Compliance Roadmap 2025–2027: Complete Guide
This long-form guide provides a complete Cyber Resilience Act compliance roadmap for manufacturers, importers and distributors of products with digital elements. It explains CRA scope, obligations, deadlines 2025–2027, key technical requirements and documentation, and links to detailed articles, templates and checklists to help you move from awareness to execution.
-
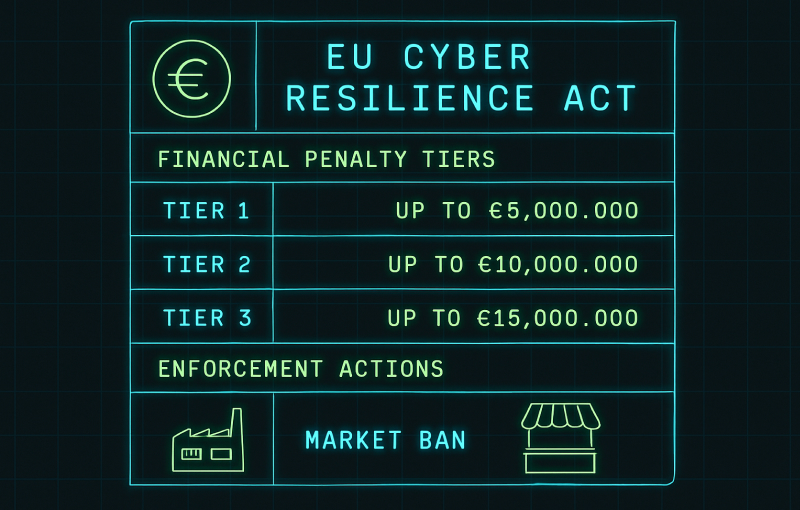
CRA Penalties and Enforcement: Complete Guide
CRA penalties can reach up to €15 million or 2.5% of global annual turnover, and authorities can also order recalls, withdrawals and market bans. This guide explains how CRA penalties work, the different fine tiers, how enforcement is applied in practice and what manufacturers, importers and distributors can do to reduce enforcement risk.
-
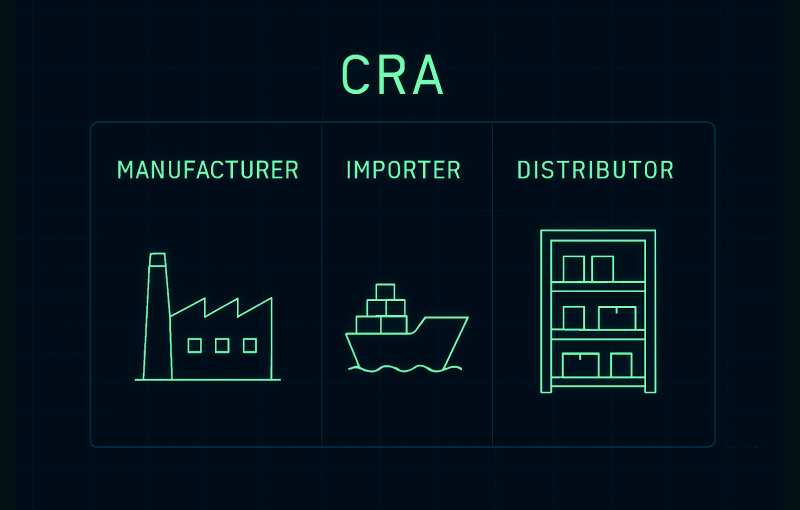
CRA Manufacturer, Importer and Distributor Obligations: Complete Guide
The Cyber Resilience Act introduces specific obligations for manufacturers, importers and distributors of products with digital elements in the EU. This guide explains CRA manufacturer obligations in depth, shows how importer and distributor duties compare and clarifies when an importer or reseller becomes a manufacturer in the eyes of the regulation.
-
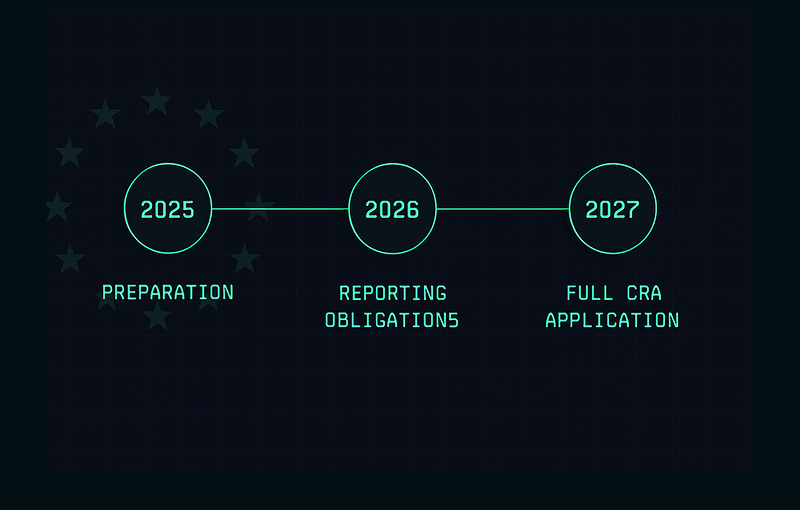
CRA Deadlines 2025–2027: Key Dates and What Manufacturers Must Do
Understand CRA deadlines 2025–2027. This guide explains the official Cyber Resilience Act timeline, what changes in 2025, 2026 and 2027, and how manufacturers, importers and distributors should plan their compliance roadmap.
-
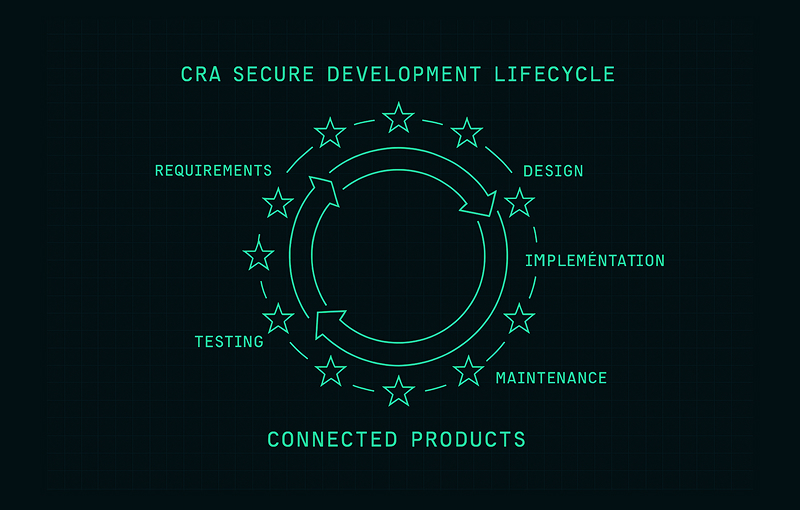
CRA Secure Development Lifecycle (SDL): Practical Guide for Manufacturers
A practical guide to the CRA secure development lifecycle. Learn how SDL activities, controls and documentation support Cyber Resilience Act compliance across the product lifecycle.
-
CRA Logging and Monitoring Requirements: Complete Guide
CRA logging and monitoring requirements help you detect incidents, investigate root causes and prove security controls over time. Learn what to log, how to protect and retain logs, and how to document telemetry for compliance.
-

CRA Declaration of Conformity (DoC) Guide: How to Build a Compliant CRA DoC
A practical guide to the CRA Declaration of Conformity. Learn how to structure a Cyber Resilience Act DoC, what it must contain, how it connects to the technical file and common mistakes to avoid.
-

CRA Technical File Structure: Complete Guide for Cyber Resilience Act Compliance
A practical guide to CRA technical file structure. Learn how to organise Cyber Resilience Act technical documentation, from product architecture and risk assessment to SBOM, testing evidence and lifecycle security.
-

Cyber Resilience Act FAQ: 30 Essential Questions Answered
A practical Cyber Resilience Act FAQ for manufacturers, IoT vendors and software teams. This guide answers the most common CRA questions about scope, obligations, deadlines, documentation, SBOM and conformity assessment.
Download free CRA Checklist 2025
The definitive CRA checklist for assessing your organization’s readiness for the Cyber Resilience Act.
By submitting this form, you accept our Terms and acknowledge that Regulus will process your data to send the checklist. For more details, see our Privacy Policy.
