Endpoint protection services are your dedicated security guard for every single device connected to a network—from a factory sensor to a smart thermostat. They provide the proactive defence and monitoring needed for individual entry points, which is absolutely vital as more and more products become internet-connected. For example, a modern car has over 100 electronic control units (endpoints), each requiring protection to prevent malicious attacks that could compromise vehicle safety.
Why Endpoint Protection Is Now Critical for Manufacturers

Think of every device you manufacture as a potential door into your customer’s network. In the past, network security was like having a single guard at the main entrance of a building. That model worked well enough when all your valuable assets were kept safely inside that one perimeter.
But the explosion of Internet of Things (IoT) devices has completely shattered that old security model. Your products now represent thousands of individual doors, each one a potential entry point for a cyberattack. A single unsecured smart appliance on a home network could be all an attacker needs to compromise more sensitive devices, like a personal computer. For instance, the infamous Mirai botnet attack in 2016 was launched by hijacking thousands of insecure IP cameras and home routers—a perfect practical example of endpoints being turned into weapons.
This shift transforms security from a simple IT concern into a fundamental product compliance issue. You’re no longer just selling hardware; you are responsible for the digital security of the products you place on the market.
From IT Problem to Compliance Mandate
This new reality is being written into law. Upcoming regulations like the EU’s Cyber Resilience Act (CRA) place direct legal obligations on manufacturers to ensure their products are secure by design and throughout their entire lifecycle.
This is where endpoint protection services become indispensable. To really appreciate their role, it helps to understand what modern endpoint security actually entails.
These services provide the necessary framework to meet strict CRA mandates, such as:
- Security-by-Design: Building security in from the very first stages of product development, not just bolting it on at the end. A practical example is integrating a security agent into the base firmware of a smart thermostat before it even leaves the factory, ensuring it’s protected from its first boot.
- Vulnerability Management: Actively finding, reporting, and patching security flaws in your products without delay.
- Secure Updates: Making sure that security patches can be deployed reliably and safely to every device out in the field.
A manufacturer of connected security cameras provides a perfect example. Without endpoint protection, a vulnerability discovered after launch could leave thousands of homes exposed. A robust service allows the manufacturer to detect the threat, develop a patch, and push a secure update to all cameras, fulfilling their CRA obligation to manage vulnerabilities.
The market reflects this urgency. The European cybersecurity market is forecasted to hit €67 billion in 2025, driven by a constant barrage of cyber incidents—ENISA logged a staggering 11,079 attacks between July 2023 and June 2024 alone.
Before we go deeper, it’s useful to see just how far we’ve come from basic antivirus software. The table below highlights the key differences and shows why a modern approach is no longer optional.
From Traditional Antivirus to Modern Endpoint Protection
| Feature | Traditional Antivirus | Modern Endpoint Protection Services (EPS) |
|---|---|---|
| Primary Focus | Signature-based malware detection (known threats). | Proactive threat hunting, behaviour analysis, and incident response (known and unknown threats). |
| Scope | Individual, often disconnected, machines. | Entire fleet of endpoints (laptops, servers, IoT, mobile) managed from a central console. |
| Threat Detection | Reactive. Detects threats after a signature is created. | Proactive. Uses AI, machine learning, and behavioural analysis to spot suspicious activity in real-time. |
| Response | Limited to quarantining or deleting malicious files. | Automated response actions like isolating endpoints, terminating processes, and rolling back changes. |
| Vulnerability Mgmt. | None. Focuses only on malware. | Integrated vulnerability scanning and patch management support to close security gaps before they are exploited. |
| Regulatory Fit | Insufficient for modern compliance like the CRA. | Provides the tools and evidence needed for security-by-design, vulnerability handling, and secure updates. |
As you can see, modern services offer a comprehensive suite of tools designed for today’s complex and regulated environments.
Ultimately, failing to secure your product’s endpoints is no longer just a technical oversight; it’s a direct business and legal risk. Implementing these services is the foundational step toward building a secure, compliant, and trustworthy product ecosystem.
What’s Inside an Endpoint Protection Platform? A Look at the Core Capabilities

To really get a feel for what modern endpoint protection services can do, you have to look under the bonnet. These platforms aren’t just single tools; they’re a suite of interconnected functions working together to provide layered security. Think of them as a highly organised security detail for each of your products, where every component has a specific—and critical—role to play.
At the heart of these services are four main pillars that defend, detect, and fix threats. Grasping how they work together is the key to understanding their value, not just for product security but for hitting your regulatory compliance targets.
Endpoint Protection Platform (EPP): The Proactive Shield
The first layer of defence is the Endpoint Protection Platform (EPP). Its main job is to stop infections before they can even start. Imagine a vigilant security guard at the door of each device, checking every file and process that tries to get in.
EPP uses a couple of key methods to stop threats in their tracks:
- Signature-Based Analysis: This is the classic approach. The EPP keeps a huge library of known malware signatures—like a digital fingerprint database. It scans files and immediately blocks anything that matches a known threat. For example, if a user on a corporate laptop downloads a file containing the WannaCry ransomware, the EPP recognizes its signature and deletes it before it can execute.
- Behavioural Analysis: This is a much smarter technique. Instead of just looking for known criminals, it watches for suspicious behaviour. For example, if an app that seems harmless suddenly tries to encrypt files or mess with sensitive system settings, the EPP flags it and shuts it down. This proactive stance is essential for dealing with new and emerging malware. Our guide on how to scan for malware goes deeper into these detection methods.
The global push for stronger security is impossible to ignore. Spain, for example, has become the fastest-growing market for endpoint security in Europe, with a CAGR of 7.5% in 2024. This isn’t surprising when you consider the country’s expanding IT sector and a dramatic 75% surge in cybercrime incidents back in 2022, which intensified regulatory pressure.
Endpoint Detection and Response (EDR): The Investigation Team
While an EPP is a fantastic shield, some advanced threats are built specifically to sneak past initial defences. That’s where Endpoint Detection and Response (EDR) steps in. If the EPP is the guard at the door, the EDR is the comprehensive surveillance system and on-site investigation team.
EDR doesn’t just block threats; it continuously monitors and logs all activity on an endpoint. It gathers enormous amounts of data—every process started, every registry change, every network connection—to build a clear picture of what “normal” looks like. When it spots a subtle anomaly that an EPP might miss, it alerts your security teams.
For instance, a threat actor might use legitimate system tools in a malicious way, a technique an EPP might not catch. EDR would detect this unusual sequence of actions, isolate the affected device from the network to stop the threat from spreading, and give security analysts a complete timeline of the attack so they can investigate and clean up the mess.
This capability gives you the deep visibility needed to hunt down and eliminate intruders who have already made it past the perimeter. For a closer look at these advanced functions, you can read more about how Endpoint Detection and Response (EDR) works.
Vulnerability and Patch Management: The Health Inspector
An attacker’s favourite way in is often a known vulnerability in outdated software. Integrated vulnerability and patch management acts like an automated health inspector for your devices. It constantly scans each endpoint to identify missing security patches and other software weaknesses.
This component doesn’t just point out problems; it helps you fix them. A modern endpoint protection service can:
- Identify Vulnerabilities: It creates an inventory of all the software on a device and checks it against massive databases of known vulnerabilities. For example, it might detect that an industrial controller is running a version of the Apache web server vulnerable to the Log4Shell exploit.
- Prioritise Risks: It helps teams figure out which vulnerabilities are the most critical and need to be fixed right now.
- Support Patching: It often works directly with update mechanisms to help roll out the necessary patches efficiently across your entire fleet of devices.
This function is a cornerstone of meeting regulatory demands like the Cyber Resilience Act, which requires manufacturers to fix security flaws without delay.
Robust Update Mechanisms: The Critical Lifeline
Finally, none of the above capabilities mean a thing if you can’t actually deliver fixes and updates to your products out in the field. A robust and secure update mechanism is the lifeline that connects all your security efforts to every single deployed device.
It ensures that security patches, new EPP signatures, and EDR agent improvements can be delivered reliably and without creating new risks. For maintaining long-term product security and compliance, this is absolutely non-negotiable. A practical example is an over-the-air (OTA) update system for smart cars, which securely delivers critical security patches to vehicles without requiring a trip to the dealership.
How Endpoint Protection Services Deliver CRA Compliance

The Cyber Resilience Act (CRA) elevates product security from a recommended practice to a legal mandate. For manufacturers, the real work lies in translating these new legal duties into tangible technical controls. This is exactly where modern endpoint protection services come in, bridging the gap between regulatory theory and practical, on-the-ground implementation.
These services do more than just defend your devices; they create a verifiable, auditable record of your security diligence. The CRA insists that manufacturers prove they are managing security throughout a product’s entire lifecycle. A robust endpoint protection platform gives you the built-in machinery to meet these demands head-on, turning compliance from a documentation nightmare into a streamlined, evidence-backed process.
Meeting Post-Market Surveillance Mandates
One of the heaviest lifts under the CRA is the requirement for post-market surveillance. You can no longer just ship a secure product and call it a day. Now, you’re on the hook for its security long after it has left the factory.
This is where Endpoint Detection and Response (EDR) capabilities become absolutely essential. Think of EDR as a permanent security camera on every single device, continuously recording system events, network traffic, and process behaviour.
This constant stream of telemetry is exactly what you need to conduct effective surveillance. If a new attack technique surfaces, your security team can immediately hunt for its tell-tale signs across your entire fleet of deployed products. This isn’t just good security practice; it’s the hard evidence you need to prove you are actively monitoring your devices as the CRA demands. You can dig deeper into the specifics in our guide to CRA logging and monitoring requirements.
Imagine a company that makes connected home appliances, like smart refrigerators. An EDR agent running on each unit is constantly sending back security data. When a new threat targeting the device’s Linux kernel is discovered, the manufacturer’s security team can instantly query every refrigerator in the field to see if any show signs of compromise. This provides immediate visibility and demonstrates active surveillance in action.
Handling Vulnerabilities Without Delay
The CRA is crystal clear about vulnerability management. Article 10 states that manufacturers must have processes to handle vulnerabilities “without delay.” This means you need a rock-solid system to find, assess, and patch security flaws as soon as they appear.
An integrated vulnerability scanner within an endpoint protection platform automates this whole workflow. It periodically scans every device for outdated software and known Common Vulnerabilities and Exposures (CVEs). When a new vulnerability pops up, the platform flags every affected device and helps you prioritise patching based on severity.
This automated detection is then coupled with a secure update mechanism, letting you deploy the patch to all devices quickly and efficiently. The platform logs the entire process, generating reports that confirm the patch was deployed successfully—creating the exact paper trail required for a compliance audit.
The table below maps these capabilities directly to CRA obligations, showing how a modern endpoint protection service acts as a powerful compliance engine.
CRA Obligation and Endpoint Protection Service Alignment
| CRA Obligation (Example) | Relevant Endpoint Protection Capability | How It Helps Demonstrate Compliance |
|---|---|---|
| Annex I, Section 2(1): Handle vulnerabilities without delay. | Vulnerability Scanning & Patch Management | Automates the detection of known vulnerabilities (CVEs) across all deployed devices and manages the deployment of security patches, with logs to prove timely action. |
| Annex I, Section 2(5): Monitor for security-relevant events. | Endpoint Detection & Response (EDR) | Provides continuous monitoring of device activity, generating telemetry and logs that serve as evidence of active post-market surveillance. |
| Annex I, Section 1(3)(f): Protect confidentiality and integrity of data. | EDR & Network Monitoring | Detects and blocks unauthorised access attempts, data exfiltration, and malicious processes, helping prove that data protection controls are in place. |
| Annex II: Maintain technical documentation for 10 years. | Centralised Logging & Reporting | Gathers and securely stores all security events, vulnerability scans, patch deployments, and incident responses in one place, creating a long-term, auditable record. |
| Article 11: Report actively exploited vulnerabilities to ENISA within 24 hours. | Incident Detection & Threat Hunting | EDR capabilities provide the rapid detection and detailed forensic data needed to confirm an active exploit, enabling fast and accurate reporting to authorities. |
This alignment isn’t just about ticking boxes; it’s about building a resilient security posture that naturally produces the evidence needed to satisfy regulators.
A Real-World Compliance Scenario
Let’s walk through a practical example. Imagine a company that manufactures smart industrial sensors used in factories across Europe. A security researcher privately discloses a zero-day vulnerability in their sensor firmware.
Here’s how their endpoint protection service helps them navigate the CRA compliance minefield:
- Detection and Analysis: The EDR component, which is already monitoring the sensors, gives the security team detailed logs. They use this data to confirm the vulnerability’s real-world impact and check if any sensors have already been exploited.
- Containment: The team quickly uses the platform to create custom detection rules based on the attacker’s observed techniques. These rules are pushed out to all sensors in minutes, effectively containing the threat while a patch is developed.
- Coordinated Disclosure and Patching: While engineers work on the firmware update, the compliance team uses the platform’s asset inventory to notify every affected customer, as required by the CRA. Once the patch is ready, it’s deployed through the platform’s secure update mechanism.
- Evidence Generation: Throughout this entire incident, the endpoint protection platform logs every single action—from the initial detection to the final patch confirmation. This creates a perfect, auditable trail proving the manufacturer acted swiftly and responsibly, directly fulfilling their CRA obligations.
This integrated approach is fast becoming the industry standard. In 2024, the Europe endpoint security market was valued at USD 5.05 billion and is projected to hit USD 10.09 billion by 2033. This growth underscores the surging demand for robust security as manufacturers gear up for regulations like the CRA. For any business aiming to meet these new standards, aligning endpoint security with compliance isn’t just a good idea—it’s a critical step forward.
Choosing the Right Endpoint Protection for Your IoT Products
Picking the right endpoint protection for your IoT products isn’t like choosing a solution for company laptops. A standard office IT setup is pretty uniform, but the world of connected devices is a wild mix of hardware, operating systems, and tight performance limits. Slapping a one-size-fits-all security solution on top is not just ineffective—it can cripple your product’s performance and ruin the user experience.
The trick is to evaluate potential services through the lens of embedded and IoT devices. A security agent that hogs memory on a smart thermostat could make it frustratingly slow. Likewise, a service that only speaks Windows and macOS is completely useless for a fleet of industrial sensors running a specialised version of Linux.
Evaluate Support for Diverse Operating Systems
The first and most important checkpoint is operating system compatibility. Your products probably don’t run on standard desktop operating systems, so you absolutely have to confirm that a potential service offers lightweight, dedicated agents for the specific platforms you use.
Look for explicit support for:
- Embedded Linux Distributions: This means Yocto, Buildroot, and other custom Linux builds that are common in IoT.
- Real-Time Operating Systems (RTOS): For devices where timing is everything, like medical equipment or industrial controls, support for systems like FreeRTOS or Zephyr is non-negotiable.
- Legacy Systems: If you have older products still active in the field, you might need support for outdated but functional operating systems.
A vendor whose bread and butter is enterprise IT probably lacks the deep-down knowledge needed to secure these specialised environments. Always ask for case studies or proof of successful deployments on systems that look like yours. For example, ask a vendor, “Can you show us a deployment on a device using an ARM Cortex-M processor running FreeRTOS?”
Prioritise Low Resource Consumption
By design, IoT devices are resource-constrained. They have limited CPU power, memory (RAM), and storage. An endpoint protection agent built for a high-powered laptop will quickly overwhelm a low-power device, leading to sluggish performance or even complete failure.
When you’re evaluating a solution, demand hard data on its resource footprint:
- CPU Utilisation: What’s the average and peak CPU usage during normal operation and during a full scan?
- Memory Footprint: How much RAM does the agent use when it’s idle versus when it’s actively scanning?
- Agent Size: How much storage space does the agent itself take up? This is critical for devices with minimal flash memory.
Practical Example: A smart home hub manufacturer tested two endpoint protection services. Service A, designed for corporate laptops, had a 250 MB agent and used 150 MB of RAM. Service B, built specifically for IoT, had a tiny 15 MB agent and needed only 20 MB of RAM. For their hub with limited memory and storage, Service B was the only real choice to keep things running smoothly.
Scrutinise Integration and API Capabilities
Your endpoint protection service can’t operate in a silo. It has to plug neatly into your existing development, operations, and compliance workflows. This is where a solid Application Programming Interface (API) is essential, allowing you to automate tasks and feed security data into your other systems. For a more detailed look at how different security components work together, you can read more about Check Point’s approach to endpoint security.
Key integration capabilities to look for include:
- CI/CD Pipeline Integration: Can you build security scanning directly into your continuous integration and deployment pipeline to find vulnerabilities before a product ever ships? For example, your Jenkins or GitLab pipeline could have a stage that uses the service’s API to scan the final firmware image for known CVEs, failing the build if a critical vulnerability is found.
- SIEM/SOAR Integration: Does the service offer connectors to push alert data into your Security Information and Event Management (SIEM) or Security Orchestration, Automation, and Response (SOAR) platform?
- Compliance Tooling: Can you pull data from the service to automatically generate the reports you’ll need for CRA compliance and other regulatory audits?
Without strong API support, your team will be stuck with manual, error-prone processes that slow down your response to security incidents. The right partner provides a service built for the reality of modern product development, not one awkwardly retrofitted from the corporate world.
Best Practices for Deploying Endpoint Protection in Your Products
This is where the rubber meets the road. An effective deployment is where your entire security strategy becomes reality. It’s not about just ticking a box by installing an agent at the end of the production line; it’s about weaving security deep into your product’s DNA, making it a core design principle rather than an afterthought.
Real resilience starts long before a product ever ships. By adopting a ‘shift-left’ approach, you embed security considerations directly into the design and development phases. In practical terms, this means building the security agent into your product’s firmware or base operating system image from the very beginning.
This proactive method is a game-changer. It ensures every device is protected from the moment it’s first powered on, closing a critical window of vulnerability that would otherwise exist. It also makes fleet-wide management and updates vastly simpler, since the security foundation is a consistent, baked-in part of the product architecture.
Balancing Security with Performance
One of the biggest concerns for any embedded or IoT device is the performance hit from extra software. An overly aggressive security agent can hog precious CPU cycles and memory, degrading the user experience or, worse, disrupting the device’s core functions. The real art is finding the sweet spot between robust protection and operational efficiency.
You get there through careful tuning and customisation.
Take a manufacturer of resource-constrained medical devices, like an infusion pump. They absolutely cannot allow a security scan to interfere with the pump’s primary job. They would tune the endpoint protection service to use custom, low-impact detection rules and schedule intensive tasks, like full scans, for periods of inactivity to guarantee patient safety and device reliability.
This level of granular control is non-negotiable. It lets you tailor the security posture to the specific needs and limitations of each product, ensuring protection doesn’t come at the cost of performance.
Phased Rollouts and Continuous Testing
Pushing a security update to thousands—or even millions—of devices is a high-stakes move. One minor bug could cause major operational headaches for your customers. This is why a phased rollout strategy isn’t just a best practice; it’s essential for responsible fleet management.
A structured rollout process usually looks something like this:
- Internal Testing: First, deploy the update to a small group of devices in your own controlled lab environment. For example, deploy to 20 devices in the engineering lab and run automated functional tests for 48 hours.
- Pilot Group: Next, roll it out to a limited, hand-picked group of friendly customers or internal users in a real-world setting.
- Gradual Fleet Deployment: Once the pilot is successful, release the update in waves to the broader device fleet, often segmented by region or product model. You might start with 1% of your fleet, then 10%, then 50%, monitoring telemetry at each stage.
This methodical approach lets you monitor the update’s performance and stability at each stage. It gives you the chance to catch and fix potential issues before they can impact your entire customer base, minimising risk and ensuring a smooth deployment.
Turning Data into Active Defence
Finally, deploying endpoint protection is not a “set it and forget it” task. You unlock the platform’s true value when your product security teams are trained to actively use the data it generates. The telemetry, alerts, and logs pouring in from your device fleet are a goldmine of security intelligence.
By actively digging into this data, your team can move beyond just passive defence. They can perform proactive threat hunting, searching for the subtle signs of a compromise that automated systems might miss. For example, a security analyst might write a query to search all endpoint logs for a specific command-line argument that was recently associated with a new malware strain, even before an official signature exists. This transforms the service from a simple shield into an active, intelligent defence system, allowing you to spot and neutralise emerging threats before they can escalate into serious incidents.
Your Step-By-Step Endpoint Protection Implementation Roadmap
Alright, let’s move from theory to action. A good plan is what separates a successful security rollout from a chaotic one. This roadmap breaks down how to implement endpoint protection services into three clear phases, giving your product and compliance teams a solid path to follow.
Think of this as your practical guide. We’re going to turn those big strategic security goals into a real, deployed, and optimised solution. Each phase builds on the last, ensuring a methodical approach that keeps risks low and effectiveness high. Following these steps will help you hit those regulatory deadlines with confidence.
Phase 1: Assessment and Selection
The first phase is all about discovery and planning. You can’t protect what you don’t understand. Before you even think about choosing a vendor, you need a complete picture of your devices and your specific security obligations. Getting this foundational work right ensures the solution you pick is a perfect fit for both your product architecture and your compliance needs.
Here are the action items for this phase:
- Inventory All Endpoints: Get forensic. Create a detailed list of every product model, its hardware specs, and the exact operating systems it runs (e.g., specific Linux builds, an RTOS, etc.).
- Define Security Requirements: Document the specific security and data protection requirements your products must meet, especially those dictated by regulations like the Cyber Resilience Act.
- Evaluate Vendor Capabilities: Start comparing potential vendors. Key criteria will be things like OS support, how much CPU and memory their agent consumes, and how well their APIs integrate with your existing tools.
- Conduct a Proof of Concept (PoC): Never buy blind. Test your top one or two choices on a representative sample of your devices. This is your chance to validate their real-world performance and see if the management console is actually usable. For example, install the agent on 10 of your smart meters and measure the performance impact on their core metering functions over a one-week period.
Phase 2: Pilot and Integration
With a vendor chosen, it’s time for a controlled pilot and the real technical integration work. This phase is absolutely critical for ironing out any kinks before you go live across your entire fleet. This is where you test the solution in a real-world (but limited) setting and make sure it plays nicely with your development and security workflows.
The flow below visualises the key technical steps you’ll be taking.
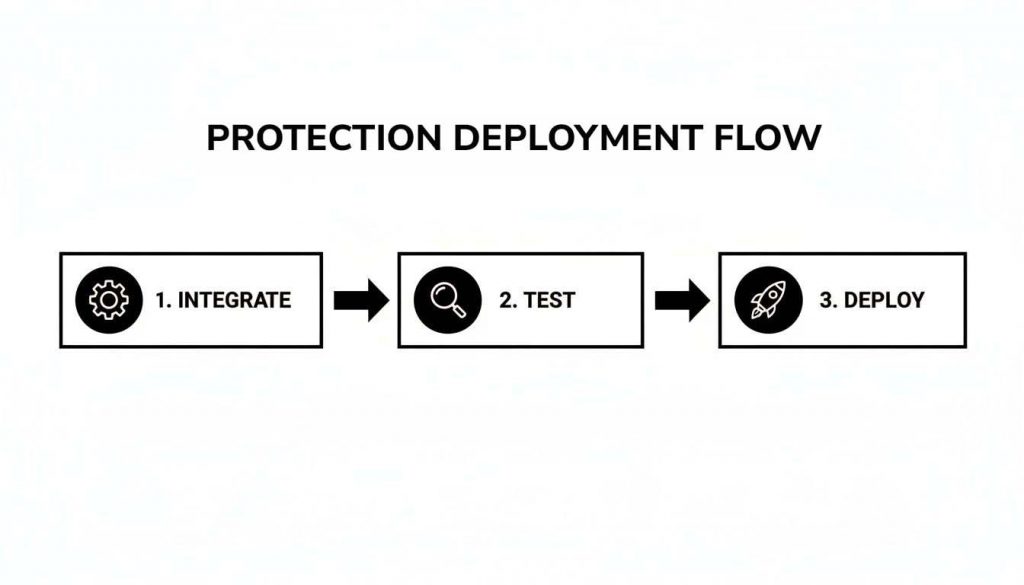
As you can see, it’s a simple but vital cycle: integrate the agent, test its impact, and get ready for the wider deployment.
Your pilot checklist should include:
- Integrate the Agent: Work with your engineers to build the lightweight security agent directly into your product’s base firmware or OS image.
- Configure Initial Policies: Don’t just turn it on. Set up baseline security policies, like detection rules and scan schedules, specifically tailored for the devices in your pilot group.
- Train Key Personnel: Your product security and incident response teams need to know how to drive this new platform. Get them trained on how to manage it and, more importantly, how to interpret its alerts.
Phase 3: Full Deployment and Optimisation
The final phase is the rollout. This involves deploying the protection service to your entire fleet of devices and, crucially, establishing the processes for ongoing management. This isn’t the end of the project; it’s the beginning of a continuous security cycle. For more on building a structured plan, our Cyber Resilience Act compliance roadmap is a great resource.
Key actions for this stage are:
- Execute a Phased Rollout: Don’t flip one big switch. Deploy the agent to your devices in gradual stages, monitoring closely for any performance issues or unexpected behaviour.
- Develop Incident Response Playbooks: When an alert fires at 3 AM, your team needs a plan. Create clear, step-by-step procedures for how to respond to the specific types of alerts the platform generates. For instance, create a playbook for a “Ransomware Behavior Detected” alert that outlines steps like: 1) Isolate the endpoint via the console, 2) Notify the security lead, 3) Analyze the EDR timeline.
- Establish a Policy Review Cadence: Threats change, and so do your products. Schedule regular reviews (quarterly is a good start) of your security policies and detection rules to make sure they stay effective.
Frequently Asked Questions
When you’re dealing with endpoint security and the new Cyber Resilience Act, it’s natural to have questions. Here are a few of the most common ones we hear from product manufacturers, along with some straightforward answers.
Is Standard Antivirus Software Enough for CRA Compliance?
In short, no. Standard antivirus software just won’t cut it for CRA compliance. The regulation requires a much more proactive and well-documented approach to security that goes way beyond simply blocking known malware.
The Cyber Resilience Act demands continuous vulnerability management, secure update mechanisms, and the ability to detect threats as they happen. Modern endpoint protection services, which include EDR and vulnerability scanning, are designed for exactly this. Traditional antivirus is really just focused on stopping threats we already know about.
How Do Endpoint Protection Services Work on Low-Power IoT Devices?
It’s a great question, as performance is everything on constrained devices. Services built for the IoT world use highly optimised, lightweight agents designed to have a minimal footprint on CPU, memory, and battery life. They pull this off by offloading the heavy-duty analysis to the cloud, so the device’s main job isn’t bogged down.
The key here is to make sure the service you choose explicitly supports your hardware and operating system, whether that’s an embedded Linux variant or a real-time OS (RTOS). Always test its performance in a real-world scenario before committing. For instance, a battery-powered security camera cannot afford a security agent that drains its battery in half the expected time.
Can Endpoint Protection Help Create a Software Bill of Materials (SBOM)?
Absolutely, and it’s one of their most powerful features for CRA readiness. Many advanced endpoint protection platforms are built to scan endpoints and identify every single piece of installed software, including libraries and their specific versions.
This inventory data gives you a solid, automated foundation for building the comprehensive Software Bill of Materials the Cyber Resilience Act requires. It delivers the transparency you need and makes the whole process of managing vulnerabilities far more efficient.
Ultimately, this isn’t just a compliance checkbox. It’s a genuine improvement to your product’s security posture.
Are you preparing your products for the Cyber Resilience Act? Regulus provides a unified software platform to assess CRA applicability, map requirements, and generate the documentation you need to place compliant products on the EU market confidently. Learn how Regulus can simplify your compliance journey at https://goregulus.com.