An open-source SIEM is a Security Information and Event Management platform built on publicly available source code. This means it’s fundamentally free-to-use—anyone can inspect, modify, and build upon it. It delivers the core functions you’d expect from any SIEM, like log collection, threat detection, and security monitoring, but without the hefty upfront licensing fees that come with commercial tools.
Think of it as a powerful, flexible foundation for building out your security operations. For example, instead of paying a vendor, you could use a tool like Wazuh to collect logs from all your web servers, databases, and firewalls, and then build your own custom dashboards to monitor for specific threats relevant to your business.
Understanding the Power of an Open Source SIEM
Imagine your organisation’s entire digital footprint—servers, firewalls, applications, cloud services—as a bustling city. Every single component is constantly generating “chatter” in the form of log files, recording every tiny action, from a user logging in to a file being accessed.
An open-source SIEM acts as the central intelligence hub for this digital city.
It doesn’t just collect all this noise. Its real job is to piece together clues from millions of seemingly unrelated events. By correlating data from different sources, it can spot patterns that would be completely invisible to the human eye, learning to distinguish between routine activity and the subtle signs of a brewing cyberattack.
What Does Open Source Mean Here?
The “open source” part is what really sets these platforms apart. It’s the difference between buying a pre-packaged home alarm system with a locked-down control panel versus building your own security setup using high-quality, community-vetted components. You get complete control.
- Total Transparency: You can look right “under the bonnet” to see exactly how the software works. There are no hidden processes or mysterious “black box” algorithms making decisions.
- Endless Customisation: You have the freedom to modify the code, add new features, and integrate it with any tool in your stack, no matter how obscure or specialised.
- Community Power: A global community of developers and security pros is constantly contributing to the project, shipping improvements, and sharing new detection rules to catch emerging threats.
Let’s say you have custom-built factory machinery that spits out logs in a bizarre, non-standard format. A commercial SIEM might throw its hands up. With an open-source SIEM, your team can simply write its own parser to understand that data perfectly, integrating it right into your security monitoring workflow.
Key Problems an Open Source SIEM Solves
At its heart, a SIEM—open source or not—is designed to close the critical security and compliance gaps that isolated tools just can’t handle. The demand for this capability is undeniable; the Security Information and Event Management market is on track to grow from USD 12.06 billion to USD 20.78 billion by 2026.
This growth is especially sharp in Europe, where regulations like GDPR, NIS2, and the Cyber Resilience Act place strict security monitoring duties on tens of thousands of businesses. You can read more about this market growth in research from Mordor Intelligence.
This is exactly where an open-source SIEM delivers its value, helping your team to:
- Centralise Visibility: It pulls all your security data into one place, giving you that coveted “single pane of glass” to monitor your entire environment. For example, you can see authentication logs from your Windows servers, network traffic from your Cisco firewall, and API calls from your AWS cloud environment all in one dashboard.
- Detect Stealthy Threats: It’s brilliant at connecting the dots. For instance, it can correlate 50 failed login attempts on a server with a successful login from a new, unexpected geographical location just moments later, immediately flagging a potential brute-force attack.
- Streamline Incident Response: When a breach happens, the SIEM gives you a chronological record of events, which becomes crucial evidence for forensic investigations. No more scrambling to piece together what happened from a dozen different log files.
- Support Regulatory Compliance: It generates the logs and reports needed to prove due diligence to auditors for regulations like the CRA. If you’re curious how this works in practice, our guide on Cyber Resilience Act applicability explains how SIEM outputs fit into the compliance puzzle.
How to Evaluate the Right Open Source SIEM
Picking an open-source SIEM is a lot like choosing the right engine for a custom-built car. You don’t just grab the one with the most horsepower on paper. You have to find the one that fits your chassis, meets your performance goals, and can actually be maintained by your team. This decision demands a practical evaluation framework that cuts through the marketing noise.
Instead of getting bogged down in endless feature lists, your evaluation should really centre on a few core pillars. These are the non-negotiables that will determine whether your SIEM project is a success or just becomes a costly maintenance headache.
Can It Scale with Your Data?
The first question you have to ask is about scalability. Your organisation’s data volume is only going in one direction: up. A SIEM that hums along nicely with today’s 100 gigabytes of logs per day might grind to a halt when that volume doubles next year.
True scalability isn’t just about storing more data; it’s about keeping query speeds fast as that dataset expands. Think of a fast-growing e-commerce company. Log volumes are going to spike dramatically during holiday seasons. Your chosen SIEM has to handle those surges without dropping events or making threat hunting impossibly slow.
Look for solutions built on architectures designed for horizontal scaling, like those using Elasticsearch or OpenSearch clusters. This approach lets you simply add more server nodes to handle the increased load, giving you a predictable path for growth.
A classic mistake is under-provisioning your infrastructure. A prototype might run just fine on a single virtual machine, but a production-ready SIEM often needs a dedicated team and a serious hardware footprint to analyse thousands of events per second effectively.
How Smart Are Its Detections?
A SIEM’s ultimate value comes down to its ability to detect threats. This is all about its detection capabilities—the quality of its analytics engine and the intelligence baked into its correlation rules. An open-source SIEM will come with a baseline set of rules, but its real power is in how easily you can customise them for your specific environment.
Imagine an IoT manufacturer looking at two different open-source SIEM tools.
- Tool A has thousands of generic, pre-built rules for common IT systems like web servers and databases. But, it really struggles to parse the proprietary log formats coming from the company’s own smart home devices.
- Tool B has fewer out-of-the-box rules but features a highly flexible and well-documented rule-writing language.
For this manufacturer, Tool B is the clear winner. Their security team can quickly write custom decoders and rules to spot unique, device-specific threats—like a thermostat suddenly trying to access a customer database. That level of tailored detection is what separates a basic log collector from a real security asset.
Integrations and Operational Costs
Seamless integrations are non-negotiable. Your SIEM has to connect effortlessly with your existing security stack, including firewalls, cloud platforms like AWS or Azure, and endpoint protection software. Without strong, pre-built integrations, your team will waste countless hours writing and maintaining custom scripts just to get data into the system.
This flows directly into the hidden operational cost: the maintenance burden. The software itself is free, but the time your team spends deploying, tuning, patching, and managing the system absolutely is not. A solution with a steep learning curve and poor documentation can quickly monopolise your most skilled engineers, completely wiping out any initial cost savings.
Understanding Open Source Licensing
Finally, you have to get your head around the licensing. Not all open-source licences are the same, and they have real business implications.
- Apache 2.0 License: This is a very permissive licence. It allows you to use, modify, and distribute the software freely, even as part of a commercial product, without having to release your own source code.
- GNU General Public License (GPL): This is a “copyleft” licence. If you modify GPL-licensed code and distribute it, you must make your modified source code publicly available under the same licence.
For most organisations using the SIEM internally, this distinction might not be a huge deal. However, if you plan to build a commercial service on top of an open-source SIEM, the difference is massive. Always run this by your legal counsel to make sure the licence aligns with your business goals and that you fully understand the total cost of ownership.
Designing Your Open Source SIEM Architecture
Building your security command centre starts with a solid blueprint. A well-designed open source SIEM architecture is crucial—it ensures you can effectively collect, process, and analyse security data without hitting performance bottlenecks or getting hit with surprise costs later on. The goal is to plan for growth from day one.
Think of your SIEM architecture like a city’s water supply system. You need an efficient way to pull water from various sources, purify it, store it for different demands, and finally, deliver it where it’s needed. Every stage has to work flawlessly for the entire system to function.
The Core Components of a SIEM
In this analogy, your SIEM has four main components working in concert to turn raw log data into actionable security intelligence. Getting how they interact is the first step towards a resilient design.
- Log Collectors (The Collection Points): These are the lightweight agents or services you install on your endpoints—servers, laptops, and network devices. Like pumps at a river, their one job is to grab raw log data and send it down the line for processing. A practical example is using a Wazuh agent on a Linux web server to forward Apache access logs and system authentication events.
- Data Processors (The Treatment Plant): This is where the real work happens. Data pipelines take in the raw logs, parse them into a structured format, enrich them with extra context (like geographic location), and normalise them so they’re all speaking the same language. This makes searching a breeze.
- Storage (The Reservoirs): Once processed, the data is stored here. Just like a water system has different reservoirs for different needs, a SIEM uses tiered storage. You’ll have fast, expensive “hot” storage for recent data you need to query instantly, and slower, cheaper “cold” storage for long-term archival.
- Visualisation Engine (The Taps): This is your user interface, typically a dashboard like the Wazuh Dashboard or Kibana. It’s what lets your security analysts query the stored data, view alerts, and build visualisations to spot trends and hunt down threats.
The following flowchart shows the key evaluation criteria—scalability, detection, and integrations—that should drive your architectural decisions.
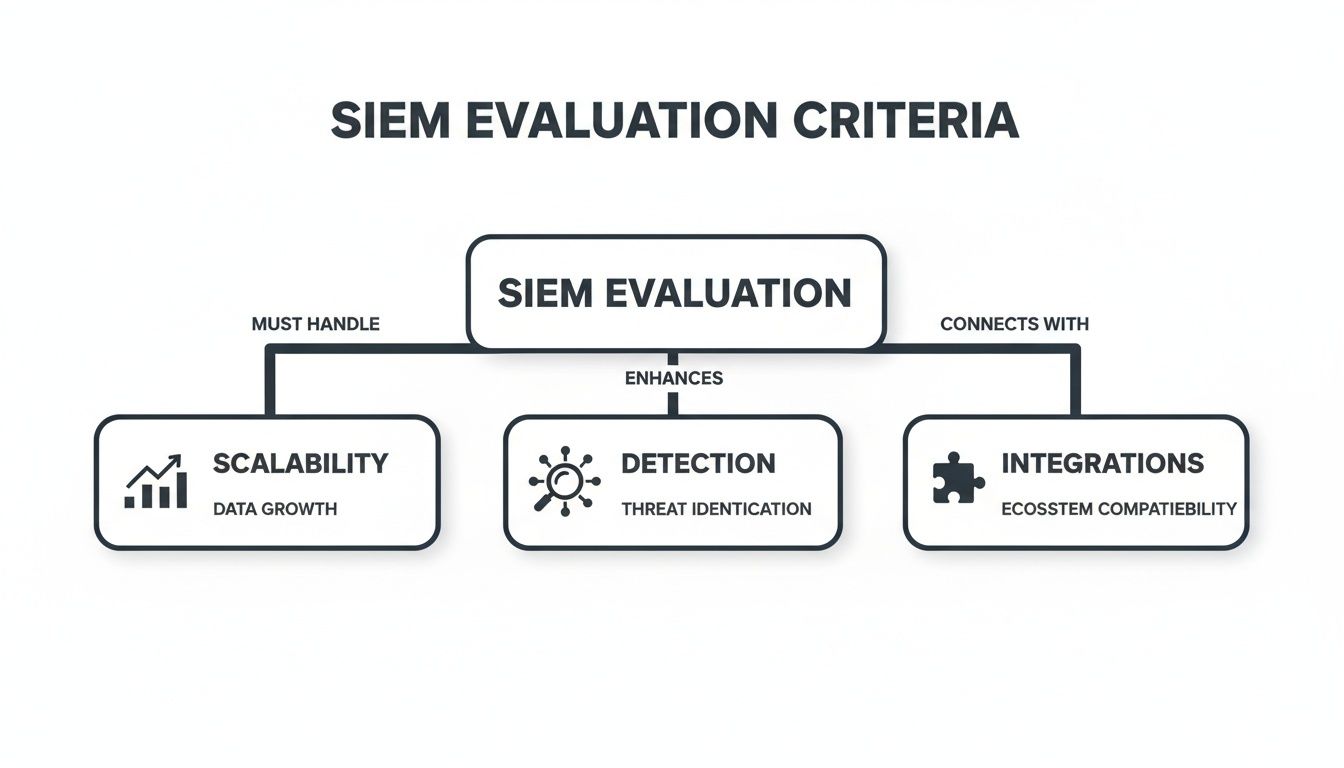
This highlights a critical point: your architecture must be built to scale as data volumes grow, support sophisticated detection rules, and integrate smoothly with the tools you already use.
A Practical Architecture Example
Let’s ground this in a real-world scenario: a small manufacturing company. They have on-premise factory equipment running legacy software alongside a modern, cloud-based management platform. Their objective is to monitor both environments from a single SIEM.
Here’s what their open source SIEM architecture could look like:
- Collection: Wazuh agents are installed on the cloud servers. For the on-premise factory equipment that can’t run an agent, a central syslog server is set up to collect their logs over the network.
- Processing: All logs are funnelled to a Logstash pipeline. The team writes a custom filter to parse the non-standard logs from the factory machines, while standard parsers handle the cloud server logs.
- Storage: The processed data is sent to an OpenSearch cluster with a simple two-tier storage policy. Data from the last 30 days stays in hot storage for rapid threat hunting, while older data is shifted to cold storage for compliance retention.
- Visualisation: The Wazuh Dashboard acts as the central hub for the security team, letting them monitor alerts and investigate incidents across both the factory floor and their cloud infrastructure.
This layered approach ensures that even complex, hybrid environments can be monitored effectively. Of course, managing a system like this in-house demands significant expertise. This is precisely why the market for managed SIEM services is booming.
The Europe Managed SIEM Services Market is projected to grow at a CAGR of 15.8% from 2023 to 2030. Germany’s market alone is expected to hit $1,371.3 million by 2030. This trend isn’t just a statistic; it underscores the immense value of specialised skills in deploying and maintaining these powerful systems.
Proper log management is also a cornerstone of regulatory frameworks. To get a handle on this, you can explore our detailed guide on the CRA logging and monitoring requirements. By planning your architecture with these needs in mind from the start, you build a system that not only strengthens your security posture but also supports your compliance obligations.
Writing Detection Rules That Actually Work
If your SIEM architecture is the skeleton, then your detection rules are the brain. A SIEM is only as smart as the logic it’s given. This is where we shift from building infrastructure to the real heart of security operations: crafting rules that turn a flood of log data into clear, actionable alerts.
Think of a correlation rule as a detective connecting clues that seem unrelated on their own. A single forced window might be suspicious. But when you combine it with muddy footprints and a disabled security camera, you’ve got a break-in. Your SIEM does the exact same thing with digital evidence.
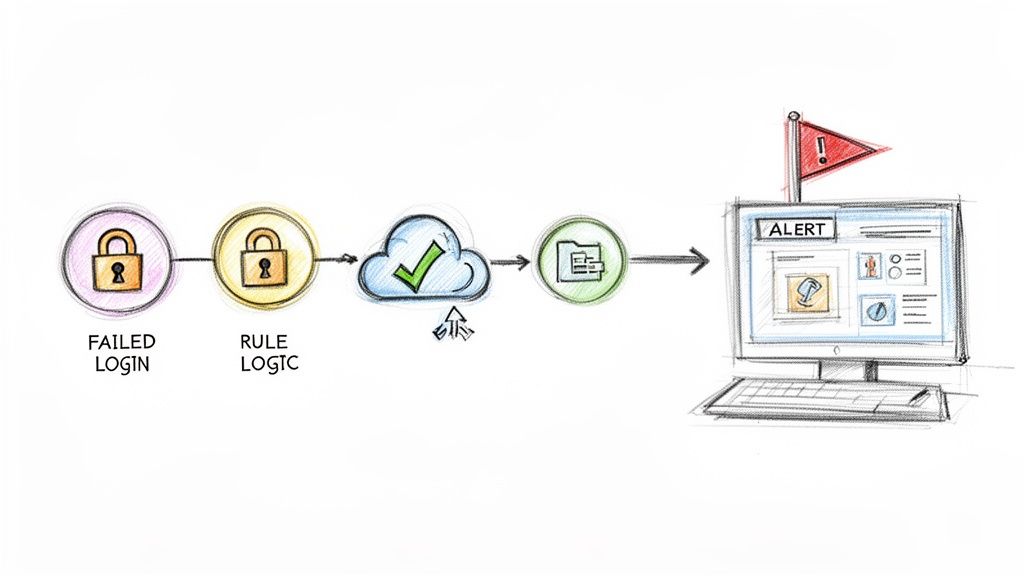
One failed login is just noise. Hundreds from the same place in minutes? That’s a pattern. A correlation rule is what teaches your SIEM to spot that pattern and flag it as a potential threat. Let’s walk through two practical examples.
Example 1: Detecting a Brute-Force Attack
Brute-force attacks are one of the most common threats out there. An attacker simply throws countless username and password combinations at your login portal, hoping one sticks. A well-written detection rule can spot this noisy activity and shut it down early.
The logic is pretty straightforward. We want to tell the security team when a burst of failed login attempts is immediately followed by a successful one from the same source.
Here’s the step-by-step logic for the rule:
- Condition 1: Identify at least 20 “Authentication Failure” events from the same source IP address.
- Condition 2: Set a tight time window for this, say within 5 minutes.
- Condition 3: Then, look for a subsequent “Authentication Success” event from that exact same IP address right after the failures.
- Action: If all three conditions are met, trigger a high-severity alert.
This simple bit of logic is brilliant at filtering out everyday typos while reliably flagging a classic sign of a compromised account.
Example 2: Spotting Potential Data Exfiltration
Catching data exfiltration is trickier because it often masquerades as legitimate user activity. The key here is to define what “unusual” actually looks like for your specific environment.
Let’s build a rule to spot a user shipping an abnormally large amount of data to an external cloud service, especially outside of normal working hours.
The logic for this rule would look something like this:
- Condition 1: Monitor network traffic logs for any outbound data transfers to known cloud storage domains (like Dropbox or Google Drive).
- Condition 2: Define a data volume threshold that’s way beyond what a typical user does in a day—for instance, more than 5 GB in one go.
- Condition 3: Pinpoint a time window that falls outside standard business hours, such as between 10 PM and 6 AM.
- Action: If all conditions are met, generate a medium-severity alert for investigation. This tells you an employee might be mishandling data, whether by accident or on purpose.
An effective rule isn’t just about detecting bad activity; it’s about ignoring normal activity. Tuning your rules to understand your organisation’s baseline is the single most important step in reducing false positives and preventing alert fatigue.
Best Practices for Rule Management
Writing a rule is just the start. Managing its entire lifecycle is what makes your siem open source platform truly effective. This means constantly tuning rules to cut down the noise, creating tiered alerts that make sense, and plugging them directly into your team’s workflow.
A crucial part of modern rule-writing is enriching your internal logs with external threat intelligence. The Europe Open Source Intelligence market is projected to expand from USD 2,503 million in 2025 to USD 12,300 million by 2034, with security analytics grabbing the largest share at 31.0%. This explosive growth points to a clear trend: using external intelligence makes internal detection rules smarter and more context-aware. You can find more details on this in a recent market research report.
To keep your security team from being buried in alerts, you need a tiered system:
- Low Priority: These are informational alerts. They get logged for context but don’t need anyone to drop what they’re doing. An example could be a user successfully logging in after hours.
- Medium Priority: Suspicious events that a junior analyst should investigate within a few hours. A practical example is an account having 10 failed logins in 10 minutes.
- High Priority: Critical alerts signalling an active threat. These should trigger an immediate, all-hands-on-deck response. The brute-force detection rule from earlier would be a prime example.
Finally, you have to integrate these alerts directly into the tools your team already uses. A high-priority alert shouldn’t just fire off an email that gets lost in a crowded inbox. It should automatically create a ticket in Jira or ServiceNow, assign it to the on-call analyst, and kickstart your entire incident response process. That’s how you make sure nothing critical ever slips through the cracks.
An open-source SIEM is much more than just a tool for spotting threats. Think of it as your strongest ally for navigating the maze of regulatory compliance. By pulling together, correlating, and storing log data from all over your environment, it becomes a system of record—giving you the verifiable evidence you need to satisfy auditors and meet critical business obligations.
This link between SIEM data and regulatory duties is especially tight for frameworks like the Cyber Resilience Act (CRA). Under regulations like this, you have to prove you’re actively managing vulnerabilities and monitoring your products after they’ve shipped. A well-configured SIEM is perfectly built to provide that proof.
Bridging SIEM Data and Compliance Audits
Picture this: an auditor asks how you handled a critical vulnerability that was disclosed last month. Instead of frantically searching through old emails and change logs, you can just turn to your SIEM.
A simple query can pull up indisputable evidence. For instance, a log from your patch management system showing a critical update was successfully rolled out to all affected servers—timestamped just hours after the vulnerability was announced—is a powerful artefact for your technical file.
A verifiable audit trail is the bedrock of modern compliance. Your SIEM provides a chronological, tamper-evident record of security actions, turning abstract policy requirements into concrete, provable facts.
This capability is essential for meeting tight incident reporting deadlines and proving that you’re embedding secure-by-design principles throughout your product’s entire lifecycle.
Fusing Vulnerability Scanning with SIEM Alerts
The real magic happens when you start blending your SIEM data with insights from other security tools. Integrating your vulnerability scanner is a game-changer, creating a powerful, context-aware security monitoring system.
When you feed vulnerability scan results into your SIEM, you enrich every incoming security event with crucial context about your assets. All of a sudden, your SIEM doesn’t just see an attack; it knows exactly how vulnerable the target is.
This integration lets you write much smarter, more effective correlation rules.
- Dynamic Alert Prioritisation: You can build a rule that automatically flags any attack targeting a server that your latest scan has marked as “unpatched” for a critical vulnerability. An attempted exploit on a hardened server might be a medium-level alert, but the same attempt on a known-vulnerable machine instantly becomes a critical incident.
- Context-Rich Investigations: When an alert fires, your security analyst can immediately see the asset’s vulnerability status right there in the SIEM dashboard. This shaves precious minutes off an investigation, as they no longer have to manually cross-reference IP addresses with separate scan reports.
- Proactive Threat Hunting: Your team can get ahead of threats by actively searching for any activity—even low-level suspicious behaviour—directed at your most critically vulnerable assets. A practical example would be querying for any traffic from a known malicious IP address that is communicating with servers flagged with “critical” vulnerabilities.
Your SIEM is a powerful engine for generating the evidence needed to meet regulatory obligations. The table below illustrates how specific SIEM outputs can be mapped directly to key requirements under the Cyber Resilience Act.
Mapping SIEM Outputs to CRA Requirements
| CRA Obligation | Supporting SIEM Output or Function | Practical Example |
|---|---|---|
| Vulnerability Handling (Annex I) | Log correlation between vulnerability scan data and network traffic logs. | The SIEM alerts when it detects network traffic matching the signature of an exploit for a vulnerability that the scanner has confirmed is present on a specific server. |
| Incident Reporting (Art. 14) | Centralised log storage with timestamping and tamper-evident features. | When a data breach is detected, the SIEM provides a complete, chronological log of all related events, which is used to build the incident report for ENISA within the 24-hour deadline. |
| Post-Market Surveillance | Long-term log retention and dashboards monitoring for anomalous activity across deployed products. | The SIEM ingests telemetry from deployed IoT devices and flags a sudden spike in failed authentication attempts across a specific product version, indicating a potential brute-force attack. |
| Secure-by-Design Proof | Logs from secure boot processes, access control systems, and cryptographic modules. | During a conformity assessment, SIEM logs are used to show that only signed firmware updates have been successfully installed, proving the integrity of the update mechanism. |
This mapping demonstrates that the data flowing through your SIEM is not just for your security team; it's a critical asset for your compliance programme.
A Core Engine for Your Compliance Strategy
This fusion of security data transforms your SIEM from a passive monitoring tool into the central engine for your entire compliance and security strategy. It becomes the hub where operational security data meets regulatory obligations. For those looking to dive deeper into the specifics, our guide on CRA vulnerability handling offers a detailed breakdown.
By correlating logs from your firewalls, servers, applications, and vulnerability scanners, you create a complete, unified view of your risk posture. This isn't just a technical advantage; it’s a fundamental requirement for proving due diligence and staying compliant in an increasingly regulated world.
Your Next Steps and Essential Resources
Getting started with an open-source SIEM project can feel daunting. I get it. But the key isn't to do everything at once; it's to start smart. While the software licence won't cost you a penny, a successful deployment demands a real investment in time, expertise, and planning.
The best approach is to start small and build outwards. This lets you show value quickly and get a feel for the platform's quirks without burning out your team. Forget about monitoring your entire estate from day one. Prove the concept, then expand.
Create an Actionable Roadmap
To get from a great idea to a working deployment, here's where I'd focus first:
- Launch a Proof-of-Concept (PoC): Before you go all-in, spin up a small test environment. Use this PoC to see how the tool really performs and, just as importantly, how your team handles managing it.
- Monitor One Critical Asset: Pick a single, high-value target. Think of your primary domain controller or a mission-critical database server. Funnel all your initial energy into collecting its logs and writing a handful of solid, targeted detection rules.
- Bookmark Community Hubs: Your biggest asset isn't the software; it's the community. Get active in the official forums and documentation for platforms like Wazuh or the ELK Stack. This is where you'll find real-world solutions.
Your first goal isn't total security coverage. It’s a "quick win." A successful PoC on one critical asset builds momentum and gets you the buy-in you need to go bigger.
Following this path will give you crucial hands-on experience and build a proper foundation for your siem open source platform. This kind of iterative, security-first process is also a core part of building a secure software development life cycle, making sure security is baked in from the start.
Answering the Big Questions
When you start exploring open-source SIEMs, a few key questions always come up. Teams want to know about scale, the real costs hiding behind the "free" label, and whether these tools can actually stand up to an auditor's scrutiny. Let's tackle these head-on.
How Much Data Can an Open-Source SIEM Actually Handle?
This is probably the most common question, and the answer is simple: as much as you can throw at it. The software itself doesn't have a hard limit. The real bottleneck is your infrastructure.
A well-designed cluster built on something like Elasticsearch can chew through terabytes of log data every single day without breaking a sweat. The trick is to plan your architecture for growth right from the start. A classic mistake is under-provisioning the hardware. Figure out your daily log volume—either in GB/day or Events Per Second (EPS)—and then build your system with at least 50% extra capacity. This gives you the headroom to scale out by simply adding more server nodes as your data grows, keeping your queries fast and ensuring you never drop a single log.
What Are the Biggest Hidden Costs?
While you don't pay for a software licence, an open-source SIEM is far from free. The real investment comes from the operational side of things, which usually breaks down into three areas:
- In-House Expertise: You need people who really know their stuff—engineers who can deploy, configure, and maintain the system. More importantly, you need analysts who can write detection rules that actually find threats. This ongoing people cost is almost always the biggest long-term expense.
- Infrastructure Investment: The servers, high-performance storage, and network gear needed to run a serious SIEM don't come cheap. A production-grade setup requires a robust, and often expensive, hardware footprint.
- Time Commitment: The initial setup is just the beginning. Ongoing maintenance, patching, and constant system tuning all take up a huge amount of your team's time—time they could be spending on other critical security tasks.
Over a 3-5 year period, these operational costs can easily match or even blow past the licence fees of a comparable commercial SIEM. That's why calculating the Total Cost of Ownership (TCO) upfront is so important.
Can an Open-Source SIEM Really Be Used for Compliance?
Absolutely. Compliance frameworks like PCI DSS and GDPR care about security capabilities, not brand names. They don't mandate a specific commercial product; they mandate things like centralised logging, access monitoring, and having the evidence you need for incident response. An open-source SIEM can deliver on all these fronts.
For instance, a tool like Wazuh can be a huge help in meeting PCI DSS Requirement 10, which is all about tracking and monitoring access to network resources and cardholder data. The responsibility, of course, is on you to implement it correctly. You have to make sure the system is configured properly, that data is kept securely for the required retention periods, and that you can pull the reports you need to prove your due diligence to an auditor.
Are you preparing for the Cyber Resilience Act? Regulus can help. Our platform simplifies CRA compliance by turning complex regulatory obligations into a clear, actionable plan. Gain clarity on your requirements, generate essential documentation, and build your roadmap to confidently place compliant products on the EU market. Learn more about Regulus.