This Cyber Resilience Act FAQ explains how the EU Cyber Resilience Act applies to software, hardware, and connected products placed on the European market. It is written for manufacturers, importers, distributors, and product teams that need clear, operational answers on compliance, risk management, documentation, and enforcement.
Cyber Resilience Act FAQ about purpose and scope
1. What is the Cyber Resilience Act?
The Cyber Resilience Act is an EU regulation that introduces mandatory cybersecurity requirements for products with digital elements. It treats cybersecurity as a product safety issue, covering the entire lifecycle from design to end of support.
2. Why did the EU introduce the Cyber Resilience Act?
The regulation responds to widespread vulnerabilities in digital products and fragmented security practices across the internal market. Its objective is to reduce systemic risk and improve baseline security for users and organizations.
3. When does the Cyber Resilience Act apply?
The regulation enters into force after a transitional period. Obligations apply progressively, giving economic operators time to adapt development processes, documentation, and vulnerability handling workflows.
4. Which products fall within scope?
Products with digital elements are in scope, including software, firmware, connected hardware, and combinations of these. Both consumer and professional products may be covered depending on functionality and risk.
5. Does the regulation apply to standalone software?
Yes. Standalone software distributed commercially can be in scope, even when no physical hardware is involved. This includes enterprise software and software delivered via digital channels.
6. Are cloud-based services covered?
Cloud services may fall under the regulation when they are supplied as software products rather than pure services. Classification depends on how functionality is delivered and controlled.
7. How is open-source software treated?
Open-source software is not automatically excluded. Obligations depend on commercial distribution and responsibility for the product. Interpretation is commonly aligned with guidance from the European Union Agency for Cybersecurity.

The most common CRA questions revolve around scope, obligations, security requirements and documentation.Cyber Resilience Act FAQ about roles and obligations
8. Who must comply with the regulation?
Manufacturers, importers, and distributors all have defined responsibilities. Each role is accountable for different aspects of compliance and market surveillance.
9. What are the main obligations for manufacturers?
Manufacturers must design secure products, manage cybersecurity risks, address vulnerabilities, and maintain technical documentation. These obligations are typically structured through a formal CRA risk assessment process.
10. What responsibilities do importers have?
Importers must verify that products comply before placing them on the EU market. This includes checking documentation, conformity assessment results, and traceability information.
11. What responsibilities do distributors have?
Distributors must ensure that products remain compliant during distribution and must take corrective action if they become aware of non-compliance or serious vulnerabilities.
12. What cybersecurity requirements are imposed?
Products must be designed to prevent known vulnerabilities, resist attacks, and limit the impact of incidents. Secure configuration and protection against unauthorized access are core expectations.
Cyber Resilience Act FAQ about technical and security requirements
13. What is Annex I and why is it important?
Annex I defines essential cybersecurity requirements. It acts as the technical foundation for assessing whether a product meets regulatory expectations.
14. What is Annex II?
Annex II specifies technical documentation requirements. It explains what evidence manufacturers must keep to demonstrate compliance, including design decisions and security controls. Detailed guidance is available in the CRA technical documentation guide.
15. Are vulnerability handling processes mandatory?
Yes. Coordinated vulnerability disclosure and remediation processes are required. Manufacturers must be able to receive, assess, and fix reported issues in a timely manner, as defined under CRA vulnerability handling requirements.
16. Are Software Bills of Materials required?
In many cases, yes. Software Bills of Materials improve transparency and supply chain security and are closely linked to CRA SBOM requirements. Additional international context can be found in guidance from the Cybersecurity and Infrastructure Security Agency.
17. How long must security updates be provided?
Updates must be provided for the expected lifetime of the product or for a minimum period defined by the regulation. The duration depends on product type and risk profile.
Cyber Resilience Act FAQ about compliance, enforcement and documentation
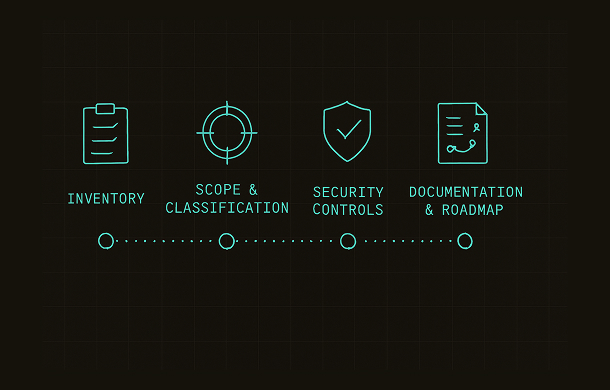
A clear sequence of steps helps organizations start Cyber Resilience Act compliance with structure and focus.18. What is the compliance timeline?
The regulation includes a phased implementation. Companies are expected to prepare early by aligning development, documentation, and post-market processes using a structured Cyber Resilience Act compliance roadmap.
19. What penalties apply for non-compliance?
Penalties can include significant administrative fines and market restrictions. Enforcement follows principles similar to other EU product safety frameworks.
20. How does CE marking relate to cybersecurity?
For covered products, cybersecurity becomes part of conformity assessment. Products must meet applicable requirements before CE marking can be affixed.
21. What documentation must be retained?
Manufacturers must retain technical documentation, risk assessments, and records of vulnerabilities and updates. These documents must be available to authorities upon request.
22. What is a Declaration of Conformity?
The Declaration of Conformity confirms that a product meets applicable regulatory requirements. Practical guidance is available in the CRA Declaration of Conformity guide.
23. Are legacy products affected?
Products already on the market may be affected if they continue to receive updates or are significantly modified. Legacy exposure should be assessed carefully.
24. How does this regulation interact with NIS2?
The regulation focuses on product security, while NIS2 targets organizational and operational resilience. Both frameworks are complementary but distinct in scope.
25. Is the approach risk-based?
Yes. Requirements scale based on product criticality, intended use, and potential impact. Higher-risk products face stricter obligations.
26. How should companies prepare for audits?
Preparation involves documented processes, evidence of secure development, and traceable vulnerability handling. Internal reviews and gap analyses are strongly recommended.
27. What role does secure development play?
Secure-by-design and secure-by-default principles are fundamental. Security must be integrated into development processes rather than added after release.
28. What happens if a vulnerability is actively exploited?
Manufacturers must notify authorities and users within defined timelines and provide remediation guidance. Incident response readiness is essential.
29. How does the regulation affect supply chains?
Supply chain transparency and accountability increase. Manufacturers are expected to understand dependencies and manage third-party risk effectively.
30. Where can companies find practical compliance tools?
Checklists, templates, and structured guidance can support implementation. A practical starting point is the CRA compliance checklist.
This Cyber Resilience Act FAQ is intended as a practical reference that supports ongoing compliance as regulatory guidance and standards continue to evolve.