If you’ve spent any time in cybersecurity, you’ve likely come across NIST Special Publication (SP) 800-53. It’s a beast of a document, a massive catalogue of security and privacy controls developed by the U.S. National Institute of Standards and Technology. Although it started life as a framework for American federal agencies, it’s now recognised globally as one of the most comprehensive resources for building secure products and systems.
Think of it less as a rigid checklist and more as a flexible library of safeguards you can pull from.
Understanding NIST SP 800-53 and Its Role for EU Manufacturers
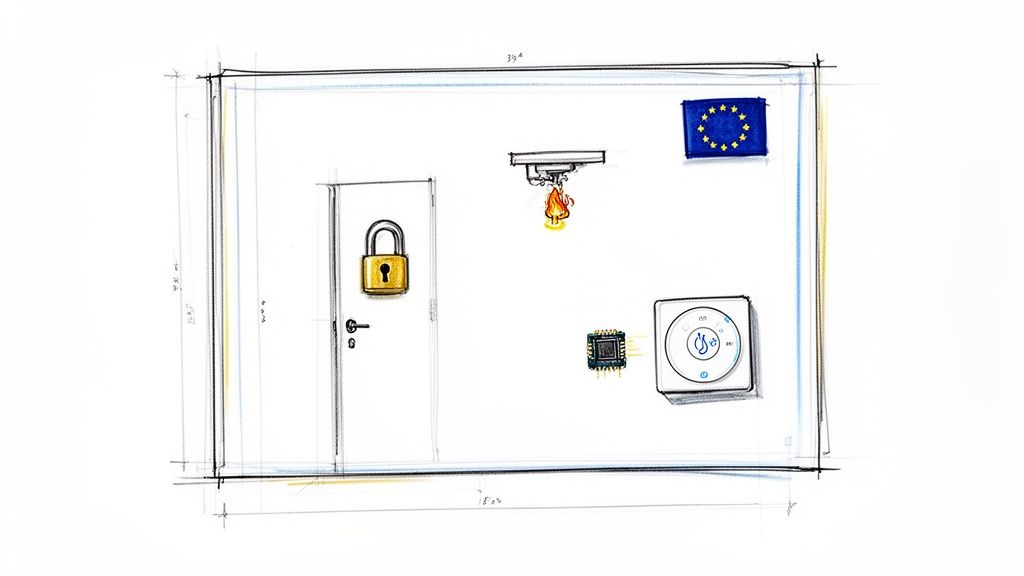
The best way to think about NIST SP 800-53 is to compare it to an architect’s blueprint for a high-security building. That blueprint doesn’t just specify the lock on the front door. It details the fire suppression system, the thickness of the walls, the placement of security cameras, and the layout of emergency exits. It covers everything.
NIST SP 800-53 does the same for digital security. It provides an exhaustive catalogue of controls that touch every conceivable aspect of cybersecurity and privacy, from managing user access to planning for disaster recovery. It’s all about building a secure foundation from the ground up, not just patching holes after the fact.
A Blueprint for Product Security
For anyone building IoT devices or software, this “blueprint” approach is incredibly valuable. Instead of trying to guess what “good security” looks like, product teams can turn to NIST SP 800-53 for proven, well-defined best practices. It helps answer the tough questions that come up every day in the development lifecycle:
- How should we properly authenticate users to our connected device? For example, should we enforce a complex password policy or implement multi-factor authentication for administrative accounts?
- What’s the most secure way to handle software updates and patches? A practical example is implementing a secure boot process that only allows digitally signed firmware from the manufacturer to be installed.
- How do we protect the personal data our product inevitably collects? For instance, a smart watch manufacturer would use NIST controls to guide the encryption of health data both when it’s stored on the device and when it’s transmitted to a cloud server.
- What’s the plan when—not if—a security incident happens? A real-world example is having a documented incident response plan that outlines how to remotely isolate a compromised device from the network to prevent an attack from spreading.
By providing this structured library of controls, the framework helps your teams translate abstract security goals into concrete, actionable steps.
Why It Matters for EU Compliance
The relevance of NIST SP 800-53 has shot up for manufacturers selling into the European Union. New regulations, particularly the EU’s Cyber Resilience Act (CRA), are placing strict cybersecurity duties on any company placing products with digital elements on the market. You can learn more about the Cyber Resilience Act’s applicability in our detailed guide.
The CRA requires manufacturers to ensure products are secure by design, manage vulnerabilities throughout their lifecycle, and provide clear security information to users. While the CRA tells you what you need to achieve, NIST SP 800-53 gives you a detailed roadmap on how to get there.
Let’s make this practical. The CRA mandates that manufacturers must have a process for handling and fixing security vulnerabilities. A product team can turn to the NIST SP 800-53 ‘System and Information Integrity’ (SI) control family, which offers specific guidance on flaw remediation, update notifications, and managing security alerts. For example, control SI-2 (Flaw Remediation) provides a concrete process: track flaws, test patches, install them within a defined timeframe, and document the entire process.
Implementing those NIST controls gives you tangible, defensible evidence that you are meeting your CRA obligations. This makes NIST SP 800-53 an essential tool for any product security team staring down modern regulatory deadlines.
Getting to Grips with the NIST SP 800-53 Structure
To use NIST SP 800-53 effectively, you first need to understand its architecture. Don’t think of it as a single, intimidating document. It’s more like a well-organised library with a clear filing system, designed to help you find the exact security and privacy safeguards your products need without getting lost in the weeds.
The framework is built on a simple, tiered system that flows from general topics down to specific actions. This logical structure lets product teams start with a broad security area and then drill down to the precise technical steps needed for their device or software.
From Families to Controls to Enhancements
At the highest level, you have the Control Families. NIST organises its huge catalogue of safeguards into 20 distinct families, each covering a specific area of security or privacy. These families are like chapters in a book, grouping related topics together so you know where to look.
Within each family, you find individual Controls. These are the specific security and privacy requirements your organisation needs to implement. A control describes a desired outcome or a specific action needed to protect a system. They are the core building blocks of your security programme.
Let’s walk through a practical example using one of the most fundamental families:
- Control Family: Access Control (AC). Its purpose is simple: make sure only authorised users can get to your product and its data.
- Control: AC-2, Account Management. This control tells you to manage user accounts—including their creation, changes, and eventual deletion. A real-world application would be a company creating a formal process for their IT department to follow whenever a new employee needs access to a system, or an employee leaves the company.
- Control Enhancement: AC-2 (3), Disable Inactive Accounts. This is an optional, more specific requirement that adds another layer of security. It directs you to automatically disable accounts after a defined period of inactivity. For example, a company might configure its network to automatically lock any user account that has not been logged into for 90 days.
This hierarchy—Family, Control, and Enhancement—is what makes the framework so adaptable. You can pick the level of detail that fits your product’s specific risks, from foundational principles to highly targeted security measures.
A Quick Tour of the Control Families
To make this more concrete, let’s look at a few of the 20 control families. They cover everything from physical security to incident response and supply chain management. The table below summarises a handful of them and gives a practical example for a connected product manufacturer.
| Control Family (ID) | Purpose | Practical Example for an IoT Device |
|---|---|---|
| Access Control (AC) | Limits system access to authorised users, processes, or devices. | Implementing role-based access so an end-user cannot access firmware update functions reserved for administrators. |
| Configuration Management (CM) | Establishes and maintains baseline configurations and inventories of systems. | Creating a "golden image" of the device firmware and tracking any changes or patches applied over its lifecycle. |
| Identification and Authentication (IA) | Verifies the identity of users, processes, or devices before granting access. | Requiring multi-factor authentication (MFA) for technicians accessing the device's management portal. |
| Incident Response (IR) | Establishes capabilities to detect, analyse, contain, and recover from security incidents. | Developing a plan to remotely quarantine a compromised device and push a security patch to it. |
| Supply Chain Risk Management (SR) | Manages risks associated with the development, acquisition, and delivery of system components. | Requiring an SBOM (Software Bill of Materials) from a third-party chip supplier to track component vulnerabilities. |
| System and Information Integrity (SI) | Protects system and information integrity by guarding against unauthorised modification or destruction. | Using a secure boot process to ensure the device only loads trusted, digitally signed firmware. |
These examples show how the families provide a structured way to think about all the different facets of product security, from the silicon on the board to the cloud services it connects to.
Selecting the Right Control Baseline
One of the most powerful features of NIST SP 800-53 is its use of control baselines. These are pre-selected sets of controls designed for systems with different levels of risk. Instead of building your control list from scratch, you begin by figuring out your system's impact level.
The framework defines three starting points:
- Low-Impact: The loss of confidentiality, integrity, or availability would have a limited adverse effect on operations, assets, or people. For example, a smart light bulb. If compromised, it's an inconvenience but doesn't cause significant harm.
- Moderate-Impact: The loss could have a serious adverse effect. Think significant operational damage, financial loss, or non-life-threatening harm. A smart home security system would be a practical example, where a breach could lead to theft.
- High-Impact: The loss could have a severe or catastrophic effect, potentially causing organisational shutdown, major financial loss, or even loss of life. An example would be a network-connected pacemaker, where a malfunction could be fatal.
Imagine a manufacturer of a smart thermostat. The device collects user schedules and home temperature data. While a breach isn't catastrophic, it could expose personal habits—a definite privacy concern. The manufacturer might classify their product as Moderate-Impact. This choice immediately gives them a starter set of recommended controls from the NIST catalogue, all tailored to that risk level.
This risk-based approach is fundamental to building a solid security programme. In fact, it’s a core principle behind creating a secure software development life cycle in our guide.
By defining these baselines, NIST SP 800-53 provides a practical starting point. It transforms the overwhelming task of picking from over a thousand controls into a manageable, risk-informed process. It ensures your security efforts are proportional to the actual threats.
This methodology works. A 2025 ENISA study found that 51% of Spanish and Italian software manufacturers implemented these three assessment levels, leading to a 29% improvement in risk-based control selection. The expanded 20 control families in NIST Rev. 5 provide the backbone for 68% of these firms' vulnerability management, aligning well with new regulations like the CRA. You can find more insights in this Apptega guide on NIST 800-53.
Understanding this structure is the key. It helps you navigate the framework efficiently and focus on the controls that truly matter for your products.
Key Changes from Revision 4 to Revision 5
The jump from Revision 4 to Revision 5 of NIST SP 800-53 was more than just a simple update; it was a fundamental shift in philosophy. Officially released on 23 September 2020, Rev. 5 reimagined the framework to tackle the security and privacy challenges of modern technology head-on.
For EU manufacturers, the most critical change was the deliberate removal of the word "federal" from the title. This wasn't just a cosmetic tweak. It signalled that NIST SP 800-53 was no longer just a US government-centric document but a globally relevant catalogue of security best practices for any organisation, anywhere.
This shift in focus makes Rev. 5 directly applicable to private companies, including IoT and software vendors across Europe. It provides a common language and a structured approach to security that easily crosses borders.
A Unified Approach to Security and Privacy
A major headache in Rev. 4 was its separation of security and privacy controls. Privacy was always a consideration, but it often felt bolted on rather than built-in. Revision 5 fixed this by weaving privacy controls directly into the main security control catalogue.
The result is a single, consolidated set of safeguards. Now, when your product team is looking at a requirement like data protection, the associated privacy obligations are right there in the same control family, making it much harder to overlook them.
This integrated structure is incredibly helpful for complying with regulations like GDPR and the CRA, where security and privacy are two sides of the same coin. It naturally encourages a "privacy by design" approach, making it easier to build products that respect user data from the ground up.
For instance, a team building a smart health device can now find controls for encrypting data right alongside controls for user consent and data minimisation—all within one cohesive framework. This holistic view simplifies implementation and strengthens overall compliance.
Introducing Supply Chain Risk Management
Perhaps the most forward-thinking update in Rev. 5 was the creation of a brand-new control family: Supply Chain Risk Management (SR). This was introduced to address the growing threats coming from third-party components, whether it's an open-source library or a hardware chip from a supplier.
The SR family provides specific controls for:
- Identifying and managing risks from your suppliers.
- Protecting the supply chain from tampering and counterfeit parts.
- Requiring crucial security documentation, like a Software Bill of Materials (SBOM).
For an IoT manufacturer, this is intensely practical. A practical example would be a company that makes smart TVs. They use an open-source video decoding library in their software. The SR controls would guide them to obtain an SBOM for that library, monitor it for new vulnerabilities, and have a plan to update the library on all their TVs if a critical flaw is discovered. This directly addresses CRA requirements around third-party component security.
Emphasis on Outcomes and Broader Applicability
Finally, Rev. 5 changed its language to be more outcomes-based. Instead of giving overly rigid instructions, the controls now focus on the desired security result. This gives your teams more flexibility in how they achieve that result. The framework also swapped the term "information system" for the much broader term "system."
This simple change allows the framework to apply seamlessly to just about anything—from cloud platforms and industrial control systems to IoT devices and embedded software. It’s a far more adaptable and future-proof approach.
This diagram helps visualise the simple yet powerful hierarchy of the NIST SP 800-53 framework.
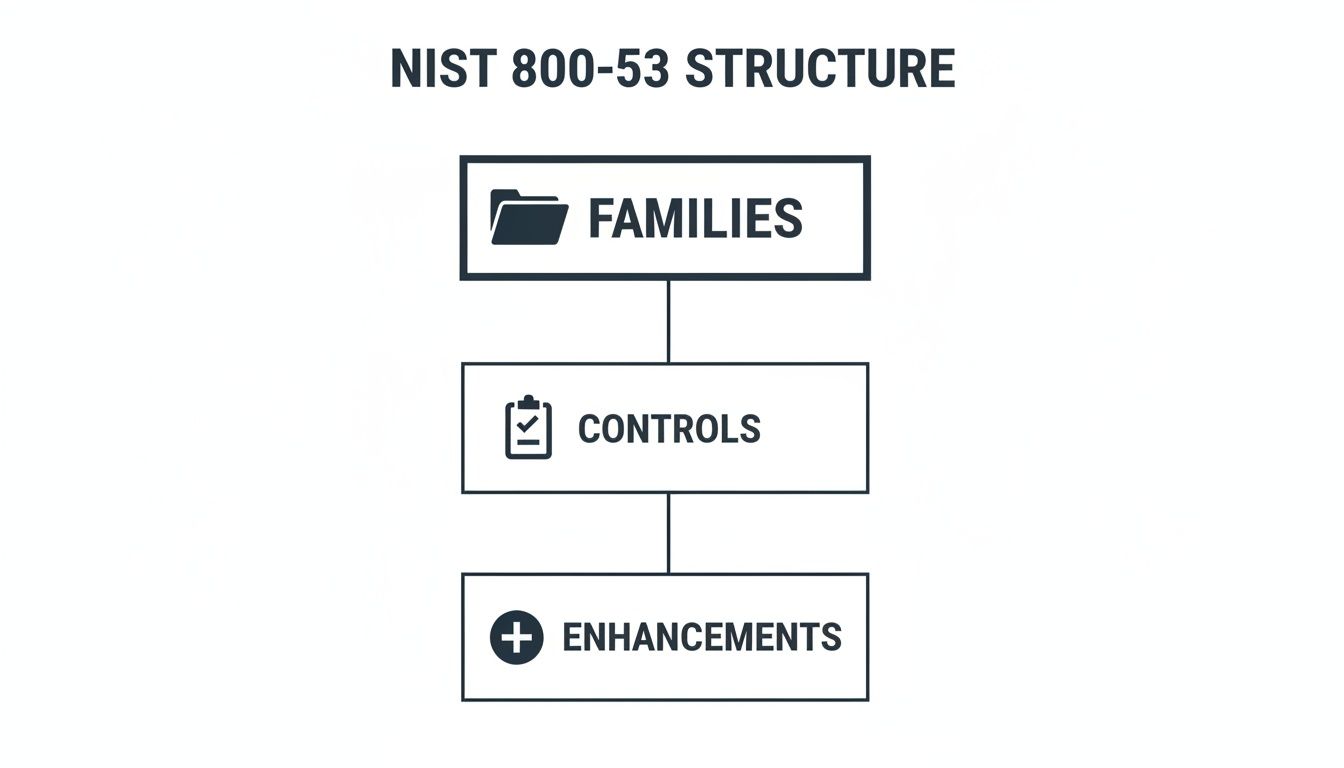
As you can see, broad security Families are broken down into specific Controls and even more granular Enhancements, which allows for a very tailored implementation.
The impact of these changes has been significant. Our own data shows that NIST SP 800-53 compliance among ES-region connected hardware vendors surged 44% after Rev. 5 was published. Today, 39% of Portuguese and Swedish digital product teams use its controls to fulfil CRA applicability assessments, with 76% reporting better resilience against firmware exploits. You can read the full details about NIST SP 800-53 Rev. 5 on the official site.
Mapping NIST SP 800-53 to EU Regulations Like the CRA
For companies selling into the EU, the real magic of NIST SP 800-53 is how it acts as a practical translation layer for complex regulations. While laws like the Cyber Resilience Act (CRA) tell you what security outcomes you need to achieve, NIST gives you a detailed catalogue of how to get there. This makes it a priceless tool for turning dense legal obligations into concrete engineering tasks.
Instead of staring at a blank page, your product teams can use the NIST control families as a ready-made starting point for their compliance strategy. This approach doesn't just save time; it gives your security programme a defensible, internationally recognised foundation.
Bridging the Gap Between NIST Controls and CRA Obligations
The alignment between NIST SP 800-53 and the CRA is surprisingly direct. Many of the CRA’s core requirements for products with digital elements have a clear counterpart in the NIST control families. This direct mapping means that a solid implementation of NIST controls can generate much of the evidence you'll need for your conformity assessment.
Let's look at a real-world example. The CRA is very clear that manufacturers must have a process for handling and fixing discovered vulnerabilities.
- CRA Requirement: Article 10(4) of the CRA insists that manufacturers ensure vulnerabilities, including those in third-party components, are "handled effectively and in a timely manner."
- NIST SP 800-53 Control: This maps cleanly to control SI-2 (Flaw Remediation) from the 'System and Information Integrity' family. This control gives you specific guidance on identifying, reporting, and correcting software flaws.
By implementing SI-2, you aren't just following a security best practice; you are building the exact processes and documentation needed to prove you comply with a critical part of the CRA.
Tackling Supply Chain Security with the SR Family
Another area where this mapping proves its worth is in managing supply chain risks—a massive focus of the CRA. Today's products are assembled from countless third-party components, and regulators want to see proof that you're managing the security of that entire ecosystem.
The Supply Chain Risk Management (SR) family in NIST SP 800-53 is designed for exactly this challenge.
- CRA Requirement: The CRA demands that manufacturers document the software components in their products, including those from third parties. This is usually done with a Software Bill of Materials (SBOM).
- NIST SP 800-53 Control: Control SR-3 (Supply Chain Controls and Processes) provides a framework for managing supplier relationships. This includes setting security requirements for your vendors and verifying the integrity of the components they provide, which naturally leads to creating an SBOM.
Putting the SR controls into practice helps your team build a structured process for vetting suppliers and tracking components, giving you the hard evidence needed to show due diligence under the CRA. For more on how this fits into the bigger picture, check out our guide on the CRA conformity assessment process.
By systematically mapping CRA articles to NIST SP 800-53 controls, you transform vague legal language into an actionable project plan. This removes ambiguity and empowers your engineering teams to build compliance into the product from day one.
The platform screenshot below shows how compliance software can centralise this mapping work.
A tool like this simplifies the whole process by directly linking regulatory articles to actionable controls and evidence tasks, cutting down on manual effort.
The table below gives a few more practical examples of how you can map specific NIST SP 800-53 controls to key requirements in the Cyber Resilience Act.
NIST SP 800-53 Controls Mapped to CRA Requirements
| CRA Requirement | Relevant NIST SP 800-53 Control Family | Example NIST Control | How It Helps Meet the Obligation |
|---|---|---|---|
| Annex I, Sec. 2(1): No known exploitable vulnerabilities. | System and Information Integrity (SI) | SI-2 (Flaw Remediation): Identify, report, and correct flaws in a timely manner. | Provides a structured process for tracking and patching vulnerabilities before release. |
| Annex I, Sec. 2(5): Protection against unauthorised access. | Access Control (AC) | AC-2 (Account Management): Manage system accounts, including creation, modification, and termination. | Ensures only authorised users can access the product, a core CRA security principle. |
| Annex I, Sec. 2(6): Confidentiality of stored and transmitted data. | System and Communications Protection (SC) | SC-8 (Transmission Confidentiality and Integrity): Protect the confidentiality of transmitted information. | Guides the implementation of encryption (e.g., TLS) for data in transit. |
| Annex I, Sec. 2(8): Limitation of attack surfaces. | System and Information Integrity (SI) | SI-7 (Software, Firmware, and Information Integrity): Detect unauthorised changes to software and firmware. | Helps implement secure boot and code signing to minimise attack vectors. |
| Annex VII: Technical Documentation must include the SBOM. | Supply Chain Risk Management (SR) | SR-3 (Supply Chain Controls and Processes): Establish controls for managing supply chain elements. | The process of vetting and tracking components naturally produces the data for an SBOM. |
This mapping isn't just a theoretical exercise. It's a practical way to build a compliance programme that is both robust and auditable, turning legal requirements into a clear set of engineering deliverables.
How ISO 27001 Fits into the Picture
It's also worth understanding how NIST SP 800-53 relates to another major standard, ISO 27001. While NIST provides a detailed catalogue of controls, ISO 27001 specifies the requirements for an Information Security Management System (ISMS)—the overarching programme that manages all your security efforts.
Think of it like this:
- ISO 27001 is the blueprint for your security programme. It defines how you manage risk, assign roles, and continuously improve.
- NIST SP 800-53 is the detailed library of safeguards you select and implement within that programme.
The two work together perfectly. Many organisations use ISO 27001 to build their management framework and then use the NIST SP 800-53 catalogue to pick the specific technical and operational controls they need. This combination provides a powerful and globally recognised approach to security and compliance.
This trend is picking up speed across Europe. In the European manufacturing sector, NIST SP 800-53 has seen a 35% adoption increase among IoT vendors since 2022, largely due to its strong alignment with CRA requirements. A 2025 ENISA report also found that 62% of German and French hardware manufacturers classed as 'critical' now map their NIST implementations to CRA obligations, which has cut their compliance audit times by 28% on average. You can discover more insights about NIST SP 800-53's role in the industry from Cisco.
A Practical Implementation Roadmap for Product Teams
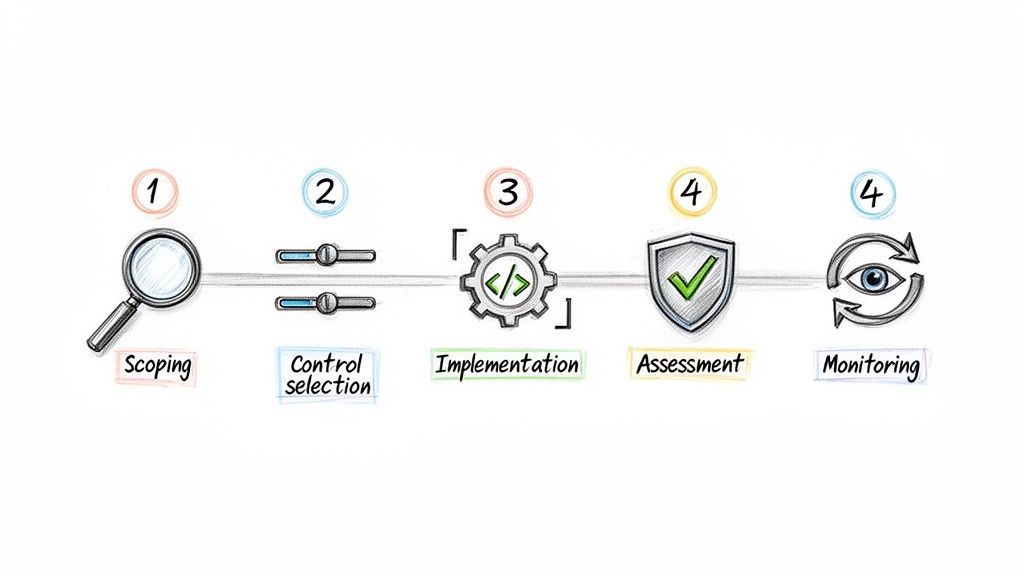
Let's be honest: translating the dense NIST SP 800-53 catalogue into something your team can actually execute on feels like a massive task. The secret isn't to tackle it all at once. The key is to break it down into manageable, logical phases.
Think of this less as a one-off project and more as an ongoing cycle of improvement that weaves security deep into your product's DNA. This roadmap gives product managers and engineering leads a clear plan to adopt the framework without the overwhelm.
Step 1: Scoping Your Product Boundary
Before you even think about a single control, you have to know exactly what you’re protecting. This first step, known as scoping, is all about drawing a clear boundary around your product and its entire ecosystem. This goes way beyond just the physical device or the software itself.
You need to map out every interconnected component:
- The firmware running on the device.
- The mobile app that your customers use to control it.
- The cloud backend that crunches all the data.
- Any third-party APIs your product talks to.
For example, a team building a smart lock would define their system boundary to include the lock's hardware and embedded firmware, the companion mobile app, and the cloud servers that handle user accounts and access logs. Each of these parts has entirely different security needs.
Step 2: Selecting and Tailoring Controls
With your boundary set, it's time to choose the right controls from the vast NIST SP 800-53 library. This starts with figuring out your product’s impact level—Low, Moderate, or High—which gives you a starting baseline of controls. From there, you'll need to tailor this baseline to fit your product's specific context.
Tailoring is where you get smart about security. You might add, remove, or modify controls based on your product’s architecture, its operating environment, and the actual risks you've identified. Maybe you need to add controls for a specific technology you’re using, or perhaps you can remove ones that are completely irrelevant.
Tailoring isn't about weakening security; it's about focusing it. This process ensures your security efforts are efficient and directly address the real-world risks your product faces, preventing wasted effort on irrelevant controls.
For instance, if your IoT device doesn't have a screen, any controls related to session locking on a display would be tailored out. If your product is a completely offline device, you could tailor out a significant number of controls related to network security and remote access. Simple.
Step 3: Integrating Implementation into Your Workflow
You’ve got your tailored list of controls. Now what? The most effective approach is to bake these security tasks directly into your existing development lifecycle. Don’t treat security as a separate, last-minute check. For agile teams, this means turning controls into clear, actionable stories or tasks right inside your sprint planning.
Let’s say a software team needs to implement control AC-2 (Account Management). They could break it down like this:
- Sprint 1: Develop the functionality to create and provision new user accounts securely.
- Sprint 2: Build the feature to modify user permissions and roles.
- Sprint 3: Implement an automated process to disable accounts after 90 days of inactivity.
This approach makes security a shared responsibility and guarantees it's built in, not bolted on. Integrating these tasks is a core principle of modern development. To see how this fits into a broader workflow, check out our guide on building a secure CI/CD pipeline.
Step 4: Assessing and Documenting Evidence
Implementation is one thing, but proof is everything. The assessment phase is where you verify that your controls are working correctly and are genuinely effective. This means gathering evidence to demonstrate compliance—something that’s absolutely critical for any audit or regulatory assessment.
Evidence can be anything that proves your work, such as:
- Penetration test reports that validate your defences.
- Secure coding checklists signed off by developers.
- Configuration files showing that secure settings are active.
- Screenshots from admin panels that demonstrate access controls are in place.
This evidence becomes the bedrock of your technical documentation for regulations like the CRA. It’s also important to remember that this isn't a one-and-done deal. The concept of Compliance As A Continuous System is key here; assessment and monitoring have to be perpetual.
Automation platforms like Regulus can really help here. They provide a central place to map requirements to the controls you've implemented and link them directly to the evidence you've gathered. This creates a clean, auditable trail that makes conformity assessments a whole lot simpler.
FAQ About NIST SP 800-53
As product teams start getting their hands dirty with NIST SP 800-53, a lot of practical questions tend to pop up. Here are some clear, straightforward answers to the most common queries we hear from manufacturers, engineers, and compliance managers.
Is NIST SP 800-53 Mandatory for Private Companies in the EU?
No, NIST SP 800-53 is not a law and isn't directly mandatory for private companies selling products in the European Union. It started life as a security framework for U.S. federal agencies.
However, its role has expanded far beyond that. EU regulations like the Cyber Resilience Act (CRA) are mandatory, and they tell you what security outcomes you must achieve. NIST SP 800-53 offers a detailed playbook on how to achieve them, making it one of the most effective tools for demonstrating compliance.
Think of it this way: the law tells you to build a secure house. NIST gives you a set of world-class architectural blueprints. You aren't legally forced to use those specific blueprints, but they represent an industry-accepted best practice that makes it much easier to prove your house is safe and up to code.
Can We Achieve Compliance with Just a Subset of Controls?
Yes, absolutely. Trying to implement all 1,000+ controls in the NIST SP 800-53 catalogue would be a massive waste of time and resources for most products. The framework is specifically designed to be tailored.
The right way to approach it is with a risk-based mindset:
- Categorise Your System: First, figure out if your product is a low, moderate, or high-impact system based on the potential damage a security breach could cause.
- Select a Baseline: This category gives you a pre-selected baseline of controls—your starting point.
- Tailor the Controls: From there, you adapt the baseline to your product's specific technology, operating environment, and risk profile. You'll remove controls that don't apply and add others that do.
For example, a team building a simple connected toaster (a low-impact device) will have a much smaller set of controls to worry about than a company engineering a network-connected medical implant (a high-impact device). The toaster team might focus on basic access control and secure updates, while the medical device team will need extremely stringent controls for data encryption, incident response, and physical anti-tampering measures.
How Is NIST SP 800-53 Different from ISO 27001?
This is a common point of confusion, but the distinction is really important. The two frameworks have different jobs, but they work together perfectly.
- ISO 27001 is a standard for an Information Security Management System (ISMS). It’s the management framework. It defines the high-level processes for how your organisation governs, manages, and continuously improves its security programme.
- NIST SP 800-53, on the other hand, is a detailed catalogue of specific security and privacy controls. It’s the library of controls. It gives you the granular technical, operational, and management safeguards you can actually implement.
Here’s an analogy: imagine you're building a professional kitchen. ISO 27001 is the overall project plan—it defines who’s in charge, the budget, the safety procedures, and the process for inspecting the final work. NIST SP 800-53 is the catalogue of appliances and fixtures you can choose from—the specific models of ovens, fridges, and faucets, each with its own detailed specifications.
Many organisations get ISO 27001 certified to prove they have a mature management system in place, and then use the NIST SP 800-53 controls to implement the technical requirements within that system.
Can We Use NIST SP 800-53 for a Small IoT Startup?
Yes, and it's a very smart move. The full framework can look intimidating, but its principles scale down beautifully for organisations of any size. For a startup, the key is to be strategic and focus on the fundamentals first.
A small team can get huge value by starting with the low-impact baseline and concentrating on a handful of critical control families that deliver the most security bang for the buck.
For a startup, the real value of NIST SP 800-53 isn't about checking off hundreds of boxes. It's about using the framework to build a strong security foundation from day one, which prevents costly redesigns and technical debt later on.
For instance, an IoT startup making smart home sensors could get started by focusing on just four critical areas from the NIST SP 800-53 framework:
- Access Control (AC): Making sure only authorised users can access the device and its data.
- Identification and Authentication (IA): Implementing strong password policies or other modern authentication methods.
- System and Information Integrity (SI): Building a secure process for firmware updates to patch vulnerabilities.
- Supply Chain Risk Management (SR): Simply keeping a record of third-party software components (an early-stage SBOM).
By tackling these foundational controls first, the startup builds a secure-by-design product that is far better prepared for future regulatory demands and customer expectations.
Ready to turn the complexities of the Cyber Resilience Act into a clear, actionable plan? Regulus provides the software platform you need to assess your product's applicability, map your obligations, and generate the necessary documentation. Move beyond spreadsheets and gain the confidence to place your products on the EU market. Start your CRA compliance journey with Regulus today.