CRA penalties are one of the main reasons manufacturers, importers and distributors are paying attention to the Cyber Resilience Act. The regulation does not only introduce new cybersecurity requirements. It also defines strict financial sanctions and powerful enforcement tools that can remove non-compliant products from the EU market.
In this guide we explain how CRA penalties are structured, which violations trigger the highest fines, what additional enforcement powers authorities have and how organisations can reduce the risk of sanctions through a structured compliance programme. The article is written for product, engineering, legal and security teams preparing their roadmap for CRA enforcement between 2025 and 2027.
If you are new to the CRA, start with our overview on Cyber Resilience Act requirements, scope and how to prepare, then use this guide to understand the consequences of non-compliance.
1. What are CRA penalties and why do they matter?
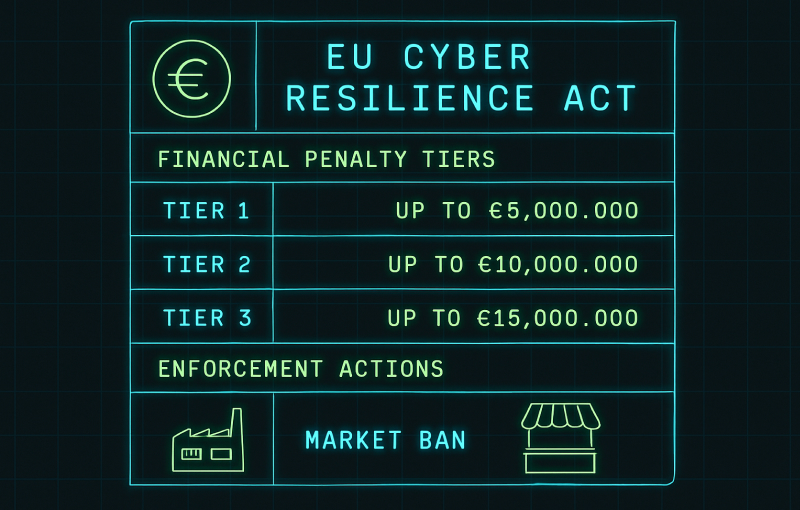
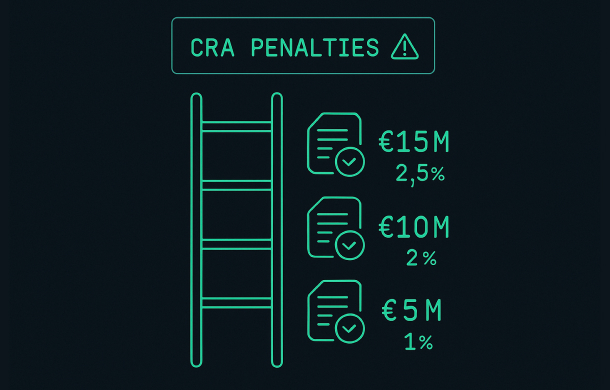
Under the Cyber Resilience Act, non-compliance can lead to administrative fines that are comparable to GDPR in magnitude. The highest CRA penalties can reach up to €15 million or 2.5% of the company’s total worldwide annual turnover, whichever is higher, for the most serious infringements such as failing to meet essential cybersecurity requirements or reporting duties.
In addition to the financial CRA penalties, market surveillance authorities can order product recalls, withdrawals and bans on making a product available on the market. For many manufacturers, losing access to the EU market can be more damaging than the fines themselves.
For this reason, CRA penalties are not only a legal topic. They shape product strategy, risk appetite, engineering priorities and post-market support commitments.
2. CRA penalty tiers and maximum fines
The Cyber Resilience Act uses a tiered structure for fines. Different categories of infringements trigger different maximum CRA penalties. The amounts are aligned with GDPR style sanctions and can scale with the size of the undertaking.
2.1 Highest tier – essential cybersecurity requirements and reporting
The most serious infringements involve core cybersecurity obligations, such as:
- Failure to comply with essential cybersecurity requirements in Annex I.
- Placing products on the market without required conformity assessment.
- Using CE marking without fulfilling CRA conditions.
- Failure to comply with vulnerability and incident reporting obligations.
These violations can trigger CRA penalties of up to:
- €15 million, or
- 2.5% of the total worldwide annual turnover of the previous financial year,
whichever amount is higher.
2.2 Mid-tier – other obligations under the CRA
Less severe, but still significant, infringements include failure to comply with other CRA obligations, for example:
- Inadequate technical documentation.
- Failure to perform proper risk assessment.
- Missing or incomplete vulnerability handling procedures.
- Inconsistent application of secure development and lifecycle requirements.
These issues can lead to CRA penalties of up to:
- €10 million, or
- 2% of total worldwide annual turnover,
whichever is higher.
2.3 Lower tier – incorrect or misleading information
The lowest tier of CRA penalties still represents a serious risk. It targets behaviour such as:
- Providing incorrect, incomplete or misleading information to authorities.
- Obstructing market surveillance activities.
- Refusing to provide documentation when requested.
These infringements can result in fines of up to:
- €5 million, or
- 1% of total worldwide annual turnover,
whichever is higher.
3. Enforcement powers beyond CRA penalties
Financial sanctions are only part of the enforcement toolbox. The CRA gives national market surveillance authorities a wide range of powers that can be used in combination with or instead of monetary fines.
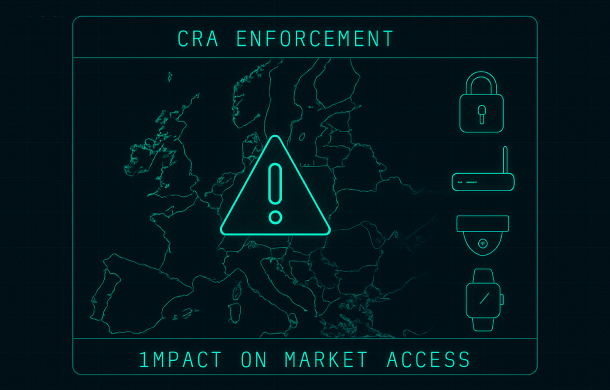
3.1 Product withdrawal and recall
Authorities can require economic operators to:
- Withdraw non-compliant products from the market, preventing them from being made available to new customers.
- Recall products that have already been supplied to users, forcing the manufacturer or importer to recover and remediate or destroy affected units.
For companies with large installed bases, the operational and reputational impact of a recall can far exceed direct CRA penalties.
3.2 Prohibition on making products available
In severe cases, authorities can issue decisions that temporarily or permanently:
- Prohibit a product from being placed on the EU market.
- Restrict its availability until non-conformities are resolved.
This effectively removes the product from the EU market and can have a decisive impact on revenues and customer relationships.
3.3 Corrective actions and public communication
Authorities can also require economic operators to:
- Implement specific corrective actions, such as security updates, configuration changes or architectural mitigations.
- Inform customers and users about the risks, the non-compliance and the corrective steps being taken.
These measures are part of the broader enforcement landscape and are often combined with CRA penalties in high-profile cases.
4. Typical non-compliance scenarios that trigger CRA penalties
While every case is different, several recurring patterns are likely to attract attention from authorities and lead to CRA penalties or other enforcement measures.
4.1 Shipping products with known vulnerabilities and no update path
Examples include:
- IoT devices that ship with hard-coded or unchangeable default passwords.
- Embedded devices without secure update mechanisms or no update mechanisms at all.
- Software components with publicly known vulnerabilities that remain unpatched.
These situations point directly at failures to meet essential cybersecurity requirements and vulnerability handling obligations, which can fall in the highest tier of CRA penalties.
4.2 Incomplete or missing technical documentation
Another common scenario is when manufacturers cannot provide technical documentation that demonstrates compliance with Annex I, Annex II and Annex VII. Typical gaps include:
- No structured risk assessment.
- No Software Bill of Materials (SBOM).
- No documented vulnerability handling or incident response procedures.
- Missing information about update mechanisms or lifecycle support.
These issues are closely linked to mid-tier CRA penalties and can also trigger corrective actions. For a detailed breakdown of documentation expectations, see our guide to CRA technical documentation.
4.3 Misleading information to authorities or notified bodies
Providing incorrect, incomplete or misleading information during conformity assessment or market surveillance is directly addressed in the CRA penalty structure. Even if the technical compliance issues are limited, lack of transparency can escalate enforcement and lead to separate fines.
5. Who faces CRA penalties: manufacturers, importers and distributors
CRA penalties can apply to any economic operator that violates the regulation, but manufacturers carry the heaviest exposure because they are responsible for design, development, documentation and lifecycle security.
- Manufacturers face the full range of CRA penalties if they fail to meet essential requirements, do not implement vulnerability handling processes or place non-compliant products on the market.
- Importers can be sanctioned if they place products on the EU market that they know or should know are not CRA compliant.
- Distributors can be targeted if they make clearly non-compliant products available or ignore obligations to cooperate with authorities.
Importantly, importers and distributors can become manufacturers in the eyes of the CRA if they rebrand products or substantially modify them in ways that affect cybersecurity. In that case they inherit the full set of manufacturer obligations and the associated CRA penalties. For a detailed breakdown of responsibilities, see our guide on CRA manufacturer, importer and distributor obligations.
6. How CRA penalties interact with deadlines and transition periods
The CRA is expected to apply fully from December 2027, with some obligations, such as vulnerability and incident reporting, becoming effective earlier. This transition period is designed to give organisations time to adapt their processes and architecture to the new requirements.
In practice, this means:
- Authorities will expect visible progress towards compliance during the transition period.
- Companies that ignore preparation entirely are more likely to face early enforcement actions once the CRA is applicable.
- Those that can demonstrate active risk assessment, documentation and vulnerability handling will be better positioned if issues arise.
For more details on key dates and milestones, see our article on CRA deadlines 2025–2027.
7. How to reduce CRA penalty and enforcement risk
The most effective way to reduce exposure to CRA penalties is to treat the regulation as a product and process improvement framework rather than a last-minute compliance exercise. Several measures are particularly important.
7.1 Build a CRA risk assessment and classification baseline
Start with a structured CRA risk assessment for each product with digital elements. This is essential for:
- Identifying relevant threats and vulnerabilities.
- Determining whether the product is Default or Critical Class.
- Choosing the right conformity assessment route.
You can follow the methodology described in our CRA risk assessment guide.
7.2 Implement vulnerability handling and update processes early
Because reporting obligations and lifecycle security are central to the CRA, gaps in vulnerability management are likely to attract enforcement attention. To reduce CRA penalty risk, manufacturers should:
- Define a vulnerability handling policy and workflow.
- Set up a clear intake channel for vulnerability reports.
- Integrate secure update and patch management processes.
Our articles on CRA vulnerability handling requirements and CRA update and patch management provide detailed guidance.
7.3 Create audit-ready technical documentation
Because mid-tier CRA penalties are closely linked to documentation gaps, building a robust technical file significantly reduces enforcement risk. Focus on:
- Risk assessment documentation and traceability to controls.
- SBOM and third-party component tracking.
- Logging, monitoring and post-market surveillance procedures.
- Declaration of Conformity that correctly references applicable legislation.
Our checklist-style article on CRA technical file structure can be used as a blueprint.
7.4 Align governance and roles with CRA expectations
Finally, CRA penalties often arise in environments where responsibilities are unclear. Manufacturers, importers and distributors should assign:
- A clear CRA compliance owner.
- Defined responsibilities for vulnerability handling and incident reporting.
- Processes for escalating potential non-compliance and cooperating with authorities.
8. CRA penalties – frequently asked questions
8.1 What are the maximum CRA penalties for non-compliance?
The highest CRA penalties can reach up to €15 million or 2.5% of the company’s worldwide annual turnover for the preceding financial year, whichever amount is higher. This tier applies to serious breaches of essential cybersecurity requirements and key reporting obligations.
8.2 Are CRA penalties similar to GDPR fines?
Yes. CRA penalties follow a similar logic to GDPR: percentage of global turnover, use of the higher amount and a tiered structure based on seriousness of the infringement. However, the CRA focuses on cybersecurity and product security rather than data protection.
8.3 Can small or medium enterprises also face CRA penalties?
Yes. CRA penalties can apply to organisations of any size. While authorities may consider proportionality, the regulation does not exempt SMEs from essential cybersecurity requirements. Using proportionality as a planning assumption is risky.
8.4 Are fines the only consequence of CRA non-compliance?
No. Authorities can combine CRA penalties with product recalls, withdrawals, bans on market access and requirements to implement specific corrective actions. Reputational damage and operational disruption are often more costly than the fines themselves.
8.5 How can manufacturers show they are reducing CRA penalty risk?
Manufacturers can reduce their CRA penalty exposure by documenting a clear compliance programme. Evidence of structured risk assessment, secure development practices, vulnerability handling and technical documentation will be important if an incident or investigation occurs.
9. How Regulus helps you avoid CRA penalties
Regulus is focused on helping EU digital product companies turn CRA requirements into practical workflows that reduce enforcement risk. Instead of relying only on manual spreadsheets, you can use structured tools to:
- Assess CRA applicability and scope – determine which products are in scope and what obligations apply.
- Map requirements to controls – connect Annex I and documentation expectations to specific implementation tasks.
- Structure technical documentation – build a CRA-ready technical file with clear traceability.
- Track CRA readiness over time – monitor gaps that could lead to CRA penalties if left unresolved.
To start reducing CRA enforcement risk:
- Download the CRA Readiness Checklist to assess gaps across scope, documentation and lifecycle security.
- Explore our CRA articles and technical guides to deepen your understanding.
- Join the Regulus Early Access list to receive updates on tools that help you operationalise CRA compliance.