The Cyber Resilience Act introduces detailed CRA manufacturer obligations and extends specific duties to importers and distributors of products with digital elements. For any organisation placing connected products, embedded systems, firmware-based devices or software with remote data processing on the EU market, understanding who is responsible for what is critical.
This guide explains how the CRA allocates responsibilities across manufacturers, importers and distributors, when an importer or reseller is treated as a manufacturer and what practical steps each role should take to be ready for enforcement. It is written for product, engineering, security and compliance teams who need a concrete mapping rather than high-level summaries.
If you are still validating whether your products fall under the CRA, start with our article on Cyber Resilience Act applicability and our overview of CRA requirements, scope and how to prepare.
1. Economic operators under the Cyber Resilience Act
The CRA uses a familiar New Legislative Framework structure. It defines several economic operators involved in making products with digital elements available on the EU market:
- Manufacturer – designs, develops or manufactures the product and markets it under their name or trademark.
- Importer – places on the EU market a product with digital elements that bears the name or trademark of a person established outside the Union.
- Distributor – makes a product available on the EU market in the supply chain without affecting its properties.
- Authorised representative – acts on behalf of the manufacturer for specific tasks.
From a practical point of view, CRA manufacturer obligations are the heaviest. Manufacturers must ensure security by design and by default, run cybersecurity risk assessments, implement vulnerability handling processes, perform conformity assessment, draw up technical documentation and keep products secure during the defined support period.
Importers and distributors have lighter, but still important duties. They must verify that only compliant products with a valid CE marking and technical documentation reach customers, and they must cooperate with authorities, especially when non-conformities or incidents are discovered.
2. CRA manufacturer obligations in detail
Manufacturers are at the center of CRA compliance because they control the design, development and support of the product with digital elements. At a high level, CRA manufacturer obligations cover five main areas: risk assessment, secure design and development, vulnerability handling, documentation and conformity assessment.
2.1 Cybersecurity risk assessment and secure design
Manufacturers must perform a structured cybersecurity risk assessment for each product with digital elements. This assessment should consider intended purpose, reasonably foreseeable use, interfaces, data flows and dependencies. The outcome must influence architecture, design decisions and security controls.
- Document risks and link them to security requirements and controls.
- Ensure the product is designed according to secure by design and secure by default principles.
- Consider the entire lifecycle, including updates, decommissioning and end of support.
For a deeper discussion of risk assessment expectations, see our guide to CRA risk assessment.
2.2 Secure development lifecycle and testing
Manufacturers are expected to integrate cybersecurity into their development lifecycle. In practice, this means:
- Defining security requirements early in the lifecycle, not only at the end.
- Embedding security activities in design, implementation, integration and system testing.
- Performing security testing that matches the risk level of the product.
- Ensuring that vulnerabilities found before release are triaged and addressed according to their severity.
You can find a more detailed breakdown in our article on the CRA Secure Development Lifecycle (SDL).
2.3 Vulnerability handling and incident reporting
One of the most visible CRA manufacturer obligations is the requirement to set up and maintain a vulnerability handling process that stays in place throughout the support period. Key elements include:
- A documented vulnerability handling policy and workflow.
- Clear intake channels for vulnerability reports from researchers, customers and partners.
- Prioritisation, remediation and communication processes based on severity and exploitability.
- Timely reporting of actively exploited vulnerabilities and severe incidents to the single reporting platform and the designated CSIRT.
We cover these topics in depth in our guide on CRA vulnerability handling requirements and in our article on CRA update and patch management.
2.4 Technical documentation and Declaration of Conformity
Manufacturers must create and maintain a technical file that demonstrates how the product meets essential cybersecurity requirements. This documentation is central to CRA manufacturer obligations and must be available to market surveillance authorities on request.
- Technical documentation in line with Annex II and Annex VII.
- Risk assessment, security architecture, SBOM, logging and monitoring descriptions.
- Test results, vulnerability handling procedures and update processes.
- An EU Declaration of Conformity referencing the CRA and other relevant legislation.
For structured templates and examples, see our article on CRA technical documentation and the guide to the CRA Declaration of Conformity.
2.5 Support period and lifecycle obligations
Manufacturers must define and communicate a support period for each product with digital elements and are expected to keep the product secure during that period. This includes:
- Providing security updates that address known vulnerabilities.
- Communicating lifecycle information, including end-of-support dates.
- Reassessing risk when new threats or vulnerabilities emerge.
All of these elements contribute directly to CRA manufacturer obligations and will be scrutinised if a product is involved in a serious incident or enforcement action.
3. CRA importer obligations – verifying compliance before entry
Importers act as the gateway for products with digital elements entering the EU market. They are not expected to redesign the product, but they share responsibility for ensuring that only compliant products are placed on the market. CRA importer obligations include several due diligence and documentation checks.
3.1 Verifying manufacturer compliance
Before placing a product on the EU market, importers must verify that:
- The product has been subject to the appropriate conformity assessment procedures.
- The manufacturer has drawn up the EU Declaration of Conformity.
- CE marking is affixed correctly and corresponds to the product and its cybersecurity claims.
- The required technical documentation exists and can be made available to authorities upon request.
In practice, CRA importer obligations mean checking that the manufacturer actually behaves like a CRA-compliant manufacturer, not just relying on marketing claims.
3.2 Labelling, instructions and traceability
Importers must also ensure that:
- The product bears the manufacturer’s name, registered trade name or trademark and contact details.
- Where required, the importer’s name and contact details are indicated on the product, its packaging or accompanying documentation.
- Required safety and cybersecurity information, including instructions for use and support period, are provided in the correct language.
3.3 Acting on suspected non-compliance or risks
If an importer has reason to believe that a product is not CRA compliant or presents a significant cybersecurity risk, they must:
- Refrain from placing the product on the market until it is compliant.
- Inform the manufacturer and, where necessary, notify relevant market surveillance authorities.
- Cooperate in any corrective actions, recalls or withdrawals requested by authorities.
Importers who ignore these CRA importer obligations risk being treated as part of the non-compliance, even if they did not design the product.
4. CRA distributor obligations – responsibility in the last mile
Distributors are the last link in the chain before a product reaches end users. Their obligations are lighter than those of manufacturers and importers, but they still play an important role in CRA enforcement and market surveillance.
4.1 Basic checks before making products available
Before making a product available on the market, distributors must verify that:
- CE marking is present on the product.
- The product is accompanied by the required documentation and instructions.
- Any safety or cybersecurity warnings or restrictions indicated by the manufacturer are respected.
- The product appears to be in conformity and does not show obvious signs of non-compliance.
These checks are part of core CRA distributor obligations and are designed to avoid obviously non-compliant products remaining in circulation.
4.2 Storage, transport and information
Distributors must also ensure that the way they store and transport products does not compromise their compliance with CRA requirements. For example, they should not remove labels, alter packaging or ignore manufacturer communications about vulnerabilities or recalls.
4.3 Responding to non-conformities
If a distributor has reason to believe that a product is not in conformity or presents a risk:
- They must not make the product available on the market.
- They should inform the manufacturer or importer.
- Where necessary, they should cooperate with market surveillance authorities in implementing corrective actions, including recall or withdrawal.
While CRA distributor obligations are narrower, distributors that repeatedly ignore obvious non-compliance can become enforcement targets, especially where they act as major channels for risky products.
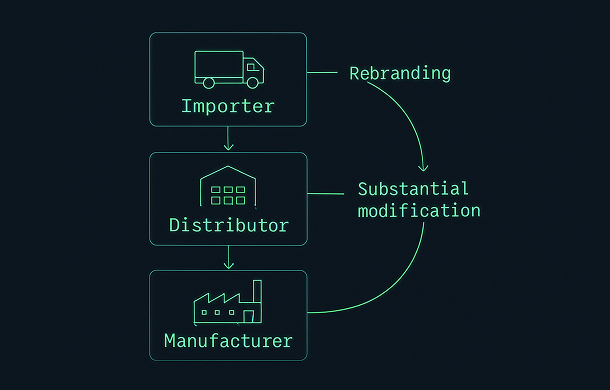
5. When importers and distributors become manufacturers
A critical point in the CRA is that roles are determined by actual behaviour, not just job titles. In some cases, importers and distributors are treated as manufacturers and therefore inherit all CRA manufacturer obligations.
5.1 Placing products under your own name or brand
An importer or distributor becomes a manufacturer in the eyes of the CRA if they:
- Place a product with digital elements on the market under their own name or trademark.
- Rebrand products in a way that makes them appear to be the original manufacturer.
In such cases, authorities will look to the rebranding entity as the manufacturer, with full responsibility for design, documentation and vulnerability handling.
5.2 Substantial modifications affecting cybersecurity
An importer or distributor also becomes the manufacturer if they perform a substantial modification that affects the product’s compliance with essential cybersecurity requirements or its intended purpose. Examples include:
- Replacing firmware or software with a custom build that changes security properties.
- Adding remote management features or cloud components essential to product operation.
- Integrating third-party components that materially change the risk profile.
Once they cross this line, they must meet the same CRA manufacturer obligations as the original manufacturer, including technical documentation, conformity assessment and vulnerability handling processes for the modified product.
6. Shared obligations and practical RACI view
While each role has its own focus, many CRA duties are shared across manufacturers, importers and distributors. Thinking in terms of a RACI matrix (Responsible, Accountable, Consulted, Informed) can help clarify ownership.
6.1 Examples of shared obligations
- Ensuring only compliant products reach the EU market Manufacturers – Responsible and Accountable Importers – Responsible for verification Distributors – Responsible for basic checks
- Vulnerability handling and communication Manufacturers – Own the process and reporting Importers – Must inform manufacturers and, where necessary, authorities Distributors – Must forward information and support corrective actions
- Documentation and traceability Manufacturers – Maintain technical documentation and Declaration of Conformity Importers – Keep documentation available for authorities Distributors – Ensure documentation and instructions accompany the product
Mapping CRA manufacturer obligations and their importer and distributor counterparts in this way is a useful step when preparing for audits and supervisory questions.
7. How this fits with CRA deadlines and enforcement
The timing of your implementation matters. The CRA defines a transition period that culminates in full applicability in December 2027. Reporting obligations for actively exploited vulnerabilities and severe incidents start earlier, which means manufacturers must have at least a basic vulnerability handling process in place before that date.
For a detailed overview, see our article on CRA deadlines 2025–2027 and our guide on CRA penalties and enforcement.
In practice:
- Manufacturers that ignore risk assessment, technical documentation and vulnerability handling are at highest risk of enforcement.
- Importers and distributors that continue to sell clearly non-compliant products despite warnings are also likely to attract attention.
- Operators who can show structured work toward CRA compliance are in a stronger position if an incident or investigation occurs.
8. CRA manufacturer, importer and distributor obligations – FAQs
8.1 Who has the main responsibility for CRA compliance?
Manufacturers have the primary responsibility. They must design and build products to meet essential cybersecurity requirements, maintain vulnerability handling processes, manage documentation and ensure the product remains secure during its support period. CRA manufacturer obligations are the most extensive in the regulation.
8.2 What are the most important CRA importer obligations?
Importers must ensure that only compliant products enter the EU market. They need to verify that the correct conformity assessment has been performed, that the Declaration of Conformity exists, that CE marking is present and that documentation is available. They must also refrain from placing obviously non-compliant or risky products on the market.
8.3 What do CRA distributor obligations cover in practice?
Distributors focus on the last mile. They must check that CE marking and required documentation are present, that instructions and safety information accompany the product and that they do not place products on the market that are clearly non-compliant. They also need to cooperate with authorities and manufacturers in recalls and corrective actions.
8.4 When do importers and distributors become manufacturers?
An importer or distributor is treated as a manufacturer when they place products on the market under their own name or trademark, or when they substantially modify the product in a way that affects cybersecurity or its intended purpose. In that case, they inherit the full set of CRA manufacturer obligations.
8.5 Do micro and small enterprises have different obligations?
The CRA recognises the situation of micro and small enterprises in some recitals and supporting measures, but the core obligations around secure design, vulnerability handling and documentation still apply where their products present cybersecurity risks. Enforcement may take proportionality into account, but it does not exempt these organisations from their responsibilities.
9. How Regulus helps economic operators operationalise CRA
Regulus is focused on helping EU digital product companies turn CRA manufacturer obligations, importer diligence and distributor checks into repeatable workflows instead of ad-hoc spreadsheets.
- Scope and role mapping – clarify which products fall under the CRA, what role you play for each product and where you might accidentally become a manufacturer.
- Requirements mapping – connect CRA obligations to concrete controls, processes and documentation tasks for each role.
- Documentation templates – structure your technical file, CRA risk assessment, SBOM, vulnerability handling procedures and Declaration of Conformity.
- Readiness tracking – follow your progress against CRA deadlines and identify where manufacturer, importer or distributor obligations are still unmet.
To move forward:
- Download our CRA Readiness Checklist and use it to assess current gaps.
- Review CRA basics, scope and documentation in the Regulus Resources section.
- Join the Regulus Early Access list to receive updates on tools that support CRA manufacturer obligations and related workflows.