Cyber Resilience Act compliance is quickly becoming a strategic topic for any organisation building connected devices, embedded systems, firmware-based products or software with digital elements for the EU market. The CRA does not just add “a few security controls”. It introduces a complete regulatory framework for product cybersecurity, with deadlines between 2025 and 2027, strict documentation requirements and significant penalties for non-compliance.
This guide is designed as a practical Cyber Resilience Act compliance roadmap for manufacturers, importers and distributors. It connects the main CRA concepts – scope, roles, deadlines, risk assessment, secure development, documentation, SBOM, vulnerability handling, conformity assessment and enforcement – into a coherent plan. Throughout the article, we link to in-depth guides and templates hosted on Regulus so you can go deeper in each area.
If you are just starting, you can read this guide end-to-end. If you already understand the basics, jump directly to the sections that matter most for your organisation and use the links to detailed CRA articles, checklists and documentation resources.
1. Why Cyber Resilience Act compliance matters now
The CRA aims to create a uniform baseline of cybersecurity for products with digital elements placed on the EU market. It applies to a wide spectrum of hardware and software, including:
- Connected consumer and industrial devices (IoT, IIoT, OT gateways).
- Embedded systems, firmware-driven products and controllers.
- Software that processes data remotely and interacts with networked environments.
- Combined hardware–software products where the software is essential to the function.
For these products, Cyber Resilience Act compliance introduces mandatory obligations on risk assessment, secure by design/default, vulnerability handling, updates, logging and monitoring, lifecycle support and technical documentation. It also defines strong penalties (up to €15 million or 2.5% of global turnover) and powerful enforcement tools, including recalls, withdrawals and market bans.
Rather than treating CRA as a late-stage legal add-on, forward-looking organisations treat it as a driver for improving their entire product security lifecycle.
2. Step 1 – Clarify CRA scope and applicability
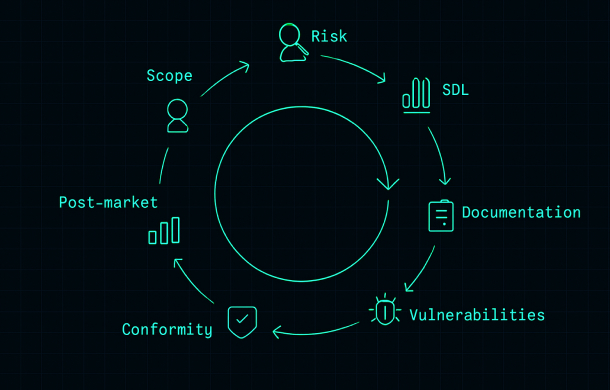
Any Cyber Resilience Act compliance roadmap starts with a clear view of whether and how the CRA applies to your products. Without this, you risk over- or under-scoping your efforts.
2.1 Determine if your products are in scope
The CRA applies to products with digital elements placed on the EU market. This includes most hardware and software that:
- Contains software or embedded software.
- Has direct or indirect network connectivity.
- Processes, transmits or stores digital data.
Some product categories are covered by sectoral legislation (for example, certain medical devices and automotive systems) and may be partially or fully excluded. Similarly, pure SaaS without installable components is typically out of scope. To work through these nuances in detail, use our in-depth guides:
- Cyber Resilience Act Applicability: Does the CRA Apply to Your Product?
- CRA Scope Explained: What Products Are In and Out
2.2 Map your product portfolio and roles
Once you know which product types are likely to be in scope, you need to map actual products and roles:
- Create an inventory of all products with digital elements you place, or plan to place, on the EU market.
- For each product, determine whether you are acting as manufacturer, importer, distributor or a combination.
- Identify where you might unintentionally become a manufacturer (for example, if you rebrand or substantially modify a product).
For a structured view of responsibilities, see our guide on CRA Manufacturer, Importer and Distributor Obligations.
2.3 Understand Default vs Critical Class
Products are further divided into classes, often summarised as Default and Critical, depending on their impact and use. Your Cyber Resilience Act compliance plan must account for this classification, because it determines the conformity assessment route and overall risk level. For a deeper dive, see:
3. Step 2 – Build your CRA risk assessment foundation
Risk assessment is at the heart of Cyber Resilience Act compliance. The regulation expects manufacturers to understand threats and vulnerabilities affecting their products with digital elements, and to use that understanding as input for design and control selection.
3.1 Product-level cybersecurity risk assessment
Your CRA risk assessment should typically cover:
- Architecture, interfaces and data flows.
- Assets (functions, data, services) that require protection.
- Threat scenarios and likely attack paths.
- Vulnerabilities in architecture and components (including third-party and open source).
- Impact and likelihood ratings that drive prioritisation.
We provide a detailed methodology, including example structures and templates, in our CRA Risk Assessment Guide.
3.2 Connecting risk assessment to controls and design
Risk assessment is not just a document. For credible Cyber Resilience Act compliance, regulators expect a clear link between risk assessment results and:
- Security requirements for the product.
- Architecture and design choices (for example, segmentation, authentication, encryption).
- Operational controls (logging, monitoring, update strategies).
This traceability also becomes part of your technical documentation, which we cover in Section 5.
4. Step 3 – Align your development lifecycle with CRA requirements
Once you understand your risk landscape, the next step in the Cyber Resilience Act compliance roadmap is integrating cybersecurity into your development lifecycle.
4.1 Secure by design and by default
The CRA explicitly requires that products with digital elements are designed and developed according to secure by design and secure by default principles. In practice, this implies:
- Defining security and safety objectives early in the lifecycle.
- Minimising attack surface and unnecessary functionality.
- Applying least privilege, strong authentication and robust access control.
- Providing secure default configurations and avoiding weak or hard-coded credentials.
4.2 Secure Development Lifecycle (SDL)
A structured SDL is one of the most effective tools for CRA compliance. It ensures that security activities are embedded into stages such as requirements, design, implementation, verification and release.
We explore this in detail in CRA Secure Development Lifecycle (SDL): Practical Guide for Manufacturers, including specific activities you can adopt and how to scale them across multiple product lines.
4.3 Logging, monitoring and post-market surveillance
Cyber Resilience Act compliance is not limited to pre-market design. The regulation expects manufacturers to monitor products after deployment and detect security-relevant events. Logging and monitoring requirements include:
- Generating logs for security-significant events (authentication, changes, updates).
- Protecting logs against tampering and unauthorised access.
- Using logs to investigate incidents and support reporting obligations.
See our in-depth article on CRA Logging and Monitoring Requirements for a detailed breakdown.
5. Step 4 – Build CRA-ready technical documentation
Even if your controls are strong, Cyber Resilience Act compliance will be judged partly on your documentation. Your technical file must show how you meet the essential requirements and support conformity assessment.
5.1 Technical documentation (Annex II and VII)
A CRA technical file usually includes:
- Product description, intended use and target environment.
- Architecture and data flow diagrams.
- Security controls and rationale, linked to risk assessment outcomes.
- SBOM and third-party component inventory.
- Vulnerability handling and update procedures.
- Logging and monitoring approach.
- Testing and validation evidence.
Use our article Cyber Resilience Act Technical Documentation: Complete Guide and CRA Technical File Structure as blueprints.
5.2 SBOM and supply-chain visibility
Many of the CRA obligations connect to supply-chain transparency. A reliable SBOM helps you:
- Understand which libraries, components and frameworks your product depends on.
- React quickly to new vulnerabilities in third-party components.
- Demonstrate due diligence to regulators and customers.
We explain expectations and practical implementation strategies in CRA SBOM Requirements: Complete Guide.
5.3 Declaration of Conformity (DoC)
Your EU Declaration of Conformity is the formal document where you state that your product meets CRA requirements (and any other applicable legislation). It must be based on your technical documentation and conformity assessment route.
See CRA Declaration of Conformity (DoC) Guide for structure, mandatory content and example formulations.
6. Step 5 – Implement vulnerability handling and update management
Vulnerability handling is one of the most visible aspects of Cyber Resilience Act compliance. The CRA expects manufacturers to maintain continuous processes for identifying, evaluating, mitigating and communicating vulnerabilities throughout the support period.
6.1 Vulnerability handling requirements
Key elements include:
- A documented vulnerability handling policy and process.
- Publicly available channels for vulnerability reporting (for example, security.txt, web forms, dedicated email).
- Prioritisation based on severity, exploitability and impact.
- Documentation of analysis, decisions and remediation steps.
We cover these responsibilities in depth in CRA Vulnerability Handling Requirements (Annex I – Section 2).
6.2 Update and patch management
Secure and timely updates are essential. Your CRA compliance roadmap should include:
- Mechanisms for authenticated and integrity-verified updates.
- Processes for planning, testing and deploying security patches.
- Clear communication to customers about update availability and impact.
For technical and organisational patterns, see CRA Update & Patch Management Requirements: Complete Guide.
7. Step 6 – Choose the right CRA conformity assessment route
Depending on the classification of your products and the standards you use, Cyber Resilience Act compliance may require different conformity assessment approaches:
- Internal control (self-assessment) for many Default Class products that implement harmonised standards.
- Third-party conformity assessment for certain important or critical products, or where harmonised standards are not fully applied.
We explain how to choose and implement the right route in CRA Conformity Assessment: Internal Control vs Third-Party Assessment.
8. Step 7 – Align with CRA deadlines 2025–2027
A realistic Cyber Resilience Act compliance roadmap must be aligned with the CRA timeline. The regulation includes a transition period leading up to full applicability in December 2027, with some obligations (such as reporting actively exploited vulnerabilities) taking effect earlier.
In practical terms:
- Use 2025–2026 to build or mature your risk assessment, SDL, documentation and vulnerability handling processes.
- Ensure that new products entering the EU market during the transition are designed with CRA requirements in mind from the start.
- By late 2027, your portfolio should have a clear conformity path for each in-scope product.
For detailed dates and planning suggestions, see CRA Deadlines 2025–2027: Key Dates and What Manufacturers Must Do.
9. Step 8 – Understand penalties and enforcement risk
No roadmap is complete without understanding the risk of inaction. As explained in our dedicated article on CRA Penalties and Enforcement, the CRA introduces significant administrative fines and strong enforcement powers.
Key points:
- Top-tier fines can reach €15 million or 2.5% of global annual turnover for serious infringements.
- Authorities can order recalls, withdrawals and bans on making products available.
- Importers and distributors can also be targeted, especially if they place obviously non-compliant products on the market.
The best mitigation for CRA enforcement risk is a transparent, documented compliance programme with clear responsibilities, traceability and continuous improvement.
10. Using the Regulus CRA Readiness Checklist and resources
To make the Cyber Resilience Act compliance roadmap more actionable, we have created a downloadable checklist and a set of supporting resources:
- CRA Readiness Checklist – assess scope, roles, risk assessment, SDL, documentation, SBOM, vulnerability handling and roadmap status.
- CRA Resources Library – curated checklists, guides and templates.
- In-depth blog articles for specific topics across CRA basics, documentation, requirements and conformity assessment.
Use the checklist to establish a baseline and revisit it periodically as your products and processes evolve.

11. Cyber Resilience Act compliance – FAQs
11.1 Who needs Cyber Resilience Act compliance?
Any organisation that manufactures, imports or distributes products with digital elements in the EU may need Cyber Resilience Act compliance. This includes manufacturers of connected devices, embedded systems, firmware-based products and combined hardware–software solutions.
11.2 Does CRA apply to pure SaaS?
Pure SaaS services without installable software or firmware are generally out of scope. However, SaaS offerings that control or update in-scope hardware, distribute firmware or include installable agents may bring the overall solution into CRA scope. It is essential to analyse the architecture rather than relying on labels like “SaaS”.
11.3 How long does CRA compliance take?
The answer depends on your current maturity. Organisations with existing secure development practices, vulnerability handling and structured documentation will move faster. Others may need the full transition period to build these capabilities. In any case, starting early is one of the most effective ways to reduce enforcement risk.
11.4 Can we rely only on external consultants?
Consultants can help interpret the regulation and design frameworks, but Cyber Resilience Act compliance ultimately depends on what your organisation actually does – the security of your products, your documentation and your post-market processes. Responsibility cannot be outsourced.
11.5 How does CRA relate to other regulations like GDPR and NIS2?
GDPR focuses on personal data protection; NIS2 focuses on network and information system security for essential and important entities. The CRA complements them by focusing on the cybersecurity of products with digital elements. Many organisations will need to manage all three frameworks in parallel.
12. How Regulus supports your Cyber Resilience Act compliance roadmap
Regulus is building self-service tools to help EU digital product companies operationalise Cyber Resilience Act compliance in a structured, repeatable way. Instead of managing CRA work in static spreadsheets and scattered documents, we aim to provide:
- Scope and role mapping workflows to clarify which products are in scope and what CRA obligations apply.
- Requirements mapping views that connect regulation text to concrete security controls, documentation tasks and processes.
- Documentation templates for technical files, SBOM, risk assessments, vulnerability handling and Declarations of Conformity.
- Readiness dashboards aligned with CRA deadlines 2025–2027 so you can track gaps and progress in real time.
To move forward:
- Download the CRA Readiness Checklist and perform an initial assessment.
- Deep dive into specific topics through the Regulus CRA Blog and Resources.
- Join the Regulus Early Access list to receive updates on tools that support your CRA roadmap.